
There is a new and live XSS vulnerability being exploited right now in Orkut – Brazil’s favorite social network, which happens to be a Google-owned property. More than 26 millions Brazilians have Orkut profiles. In less than 12 hours after being discovered and being exploited the XSS vulnerability affected more than 180,000 users and more profiles are being compromised as we speak.
No user interaction is required to be compromised – you simply need to log into your profile and go visit a friend’s profile. If you have a small picture of the Brazilian flag in your scraps section and so does your friend:

You will be infected. When infected, this message calls an external javascript file and runs it:
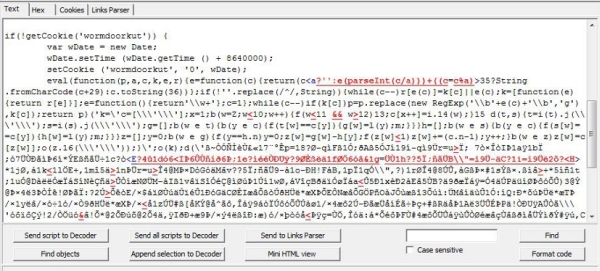
Everyone who is infected with this script is being added silently to a community called “Infected by the Virus of Orkut”, which registers all of the users compromised by this new vulnerability:
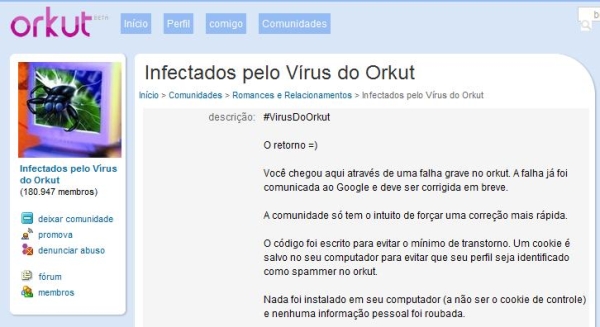
In Portuguese the description of the community says: “Voc chegou aqui atravs de uma falha grave no orkut. A falha j foi comunicada ao Google e deve ser corrigida em breve. A comunidade s tem o intuito de forar uma correo mais rpida”.
English translation:
“You arrived here by a serious security vulnerability in Orkut. This vulnerability has already reported to Google and must be fixed soon.This community only has the intention of forcing a quicker fix””.
How did this all start? The author of this community is supposedly using this XSS vulnerability to force Google to fix it quickly. This is not the only such case we have seen – in December 2007 a similar case affected more than 660,000 Orkut users in few hours.
We suggest that you avoid Orkut and/or turn off the JavaScript in your browser until Google patches this vulnerability.
But if you are a Kaspersky customer you are already protected – the javascript file exploiting this XSS and future variations is detected and blocked in all our products as Exploit.JS.Orkut.f. So just make sure your databases are updated before you go to Orkut.
Update 1: 310,000 users affected by the vulnerability and still no fix.
Update 2: after more than 400,000 users affected, Google fixed the XSS in this saturday night.






















Another live XSS vulnerability