
Q1 figures
According to KSN data, Kaspersky Lab solutions detected and repelled 479,528,279 malicious attacks from online resources located in 190 countries all over the world.
79,209,775 unique URLs were recognized as malicious by web antivirus components.
Attempted infections by malware that aims to steal money via online access to bank accounts were registered on 288 thousand user computers.
Crypto ransomware attacks were blocked on 240,799 computers of unique users.
Kaspersky Lab’s file antivirus detected a total of 174,989,956 unique malicious and potentially unwanted objects.
Kaspersky Lab mobile security products detected:
- 1,333,605 malicious installation packages;
- 32,038 mobile banker Trojans (installation packages);
- 218,625 mobile ransomware Trojans (installation packages).
Mobile threats
Q1 events
The rise of Trojan-Ransom.AndroidOS.Egat
In the first quarter of 2017, we registered a dramatic growth in attacks involving mobile ransomware from the Trojan-Ransom.AndroidOS.Egat family: the number of users attacked by this type of malware increased more than 13 times from the previous quarter. Despite this Trojan being known to us since June 2016, such an explosive increase in the number of attacks has only occurred now.
This malware has standard mobile ransomware functionality: it blocks the device, overlays all open windows with its own window, then demands money to unblock the device. In most cases, the ransom amount fluctuates between $100 and $200. Most of the attacked users were in Europe, mainly Germany, the UK and Italy.
Revamped ZTorg
We managed to detect around 30 new Trojans from the Ztorg family in the official Google Play Store. To recap, this is the family that gave us infected fake guides for Pokémon GO. It was discovered in Google Play in the summer of 2016 and was installed more than 500,000 times. After installation, Ztorg checks to make sure it isn’t running on a virtual machine. If the check is passed smoothly, the main module is loaded from a remote server. By exploiting a vulnerability in the system, the Trojan tries to gain superuser privileges. If successful, it installs its modules into the system folders and also modifies the device settings so that it remains there – even after a reset to factory settings.
Trojan.AndroidOS.Ztorg.bp in the official Google Play Store
The Trojan uses several different modules that secretly download and install various programs on the device, display ads and even buy apps. It should be noted that the functionality of this malware has changed a bit: the number of checks to verify whether the device is real has decreased; the code for downloading, decrypting and loading the main module has been placed in a downloaded library.
Asacub awakens
In the first quarter of 2017, we noted that the Trojan-Banker.AndroidOS.Asacub mobile banker was actively spreading. Over three months, the representatives of this family attacked more than 43,000 mobile devices, which was 2.5 times more than in the previous quarter. Over 97% of all attacked users were in Russia. Asacub was mainly distributed via SMS spam. After clicking a malicious link, users were directed to a page where they were prompted to view an MMS that concealed the Trojan, which was then downloaded to the device. Interestingly, if the same link was opened on a Windows device, Backdoor.Win32.Htbot.bs was downloaded.
The site from which Trojan-Banker.AndroidOS.Asacub was downloaded
It’s worth noting that Trojan-Banker.AndroidOS.Asacub is constantly expanding its spyware functionality. In addition to the standard mobile banker features, such as stealing and sending text messages, or overlaying various applications with phishing windows, this Trojan hunts for the user’s call history, contacts and GPS location.
Mobile threat statistics
In the first quarter of 2017, Kaspersky Lab detected 1,333,605 malicious installation packages, which is almost as many as in Q4 2016.
Number of detected malicious installation packages (Q2 2016 – Q1 2017)
Distribution of mobile malware by type
Distribution of new mobile malware by type (Q4 2016 and Q1 2017)
In Q1 2017, the most affected was Trojan-Ransom – its share increased from 4.64% to 16.42%, that is 3.5 times. The most rapid growth in the number of installation packages was demonstrated by the Trojan-Ransom.AndroidOS.Congur family, which will be described below.
Second came Trojan-Spyware: in terms of the growth rate, its proportion reached 10.27% (+1.83%). This was caused by the increase in the number malicious programs belonging to the Trojan-Spy.AndroidOS.SmForw and Trojan-Spy.AndroidOS.SmsThief families designed to steal SMS.
In the first quarter, the biggest decline was demonstrated by Adware (7.32%) and Trojan-Dropper (6.99%) – their shares decreased by 4.99% and 4.48% respectively. In addition, the contribution of unwanted RiskTool programs dropped by 2.55%.
TOP 20 mobile malware programs
Please note that this rating of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
In Q1 of 2017, 14 Trojans that use advertising as their main means of monetization (highlighted in blue in the table) made it into the TOP 20.Their goal is to deliver as many adverts as possible to the user, employing various methods, including the installation of new adware. These Trojans may use superuser privileges to conceal themselves in the system application folder, from which it will be very difficult to delete them.
| Name | % of attacked users * | |
| 1 | DangerousObject.Multi.Generic | 70.09 |
| 2 | Trojan.AndroidOS.Hiddad.an | 9.35 |
| 3 | Trojan.AndroidOS.Boogr.gsh | 4.51 |
| 4 | Backdoor.AndroidOS.Ztorg.c | 4.18 |
| 5 | Trojan.AndroidOS.Sivu.c | 4.00 |
| 6 | Backdoor.AndroidOS.Ztorg.a | 3.98 |
| 7 | Trojan.AndroidOS.Hiddad.v | 3.89 |
| 8 | Trojan-Dropper.AndroidOS.Hqwar.i | 3.83 |
| 9 | Trojan.AndroidOS.Hiddad.pac | 2.98 |
| 10 | Trojan.AndroidOS.Triada.pac | 2.90 |
| 11 | Trojan.AndroidOS.Iop.c | 2.60 |
| 12 | Trojan-Banker.AndroidOS.Svpeng.q | 2.49 |
| 13 | Trojan.AndroidOS.Ztorg.ag | 2.34 |
| 14 | Trojan.AndroidOS.Ztorg.aa | 2.03 |
| 15 | Trojan.AndroidOS.Agent.eb | 1.81 |
| 16 | Trojan.AndroidOS.Agent.bw | 1.79 |
| 17 | Trojan.AndroidOS.Loki.d | 1,76 |
| 18 | Trojan.AndroidOS.Ztorg.ak | 1.67 |
| 19 | Trojan-Downloader.AndroidOS.Agent.bf | 1.59 |
| 20 | Trojan-Dropper.AndroidOS.Agent.cv | 1.54 |
* Percentage of unique users attacked by the malware in question, relative to all users of Kaspersky Lab’s mobile security product that were attacked.
First place was occupied by DangerousObject.Multi.Generic (70.09%), the verdict used for malicious programs detected using cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
Trojan.AndroidOS.Hiddad.an (9.35%) was second. This piece of malware imitates different popular games or programs. Interestingly, once run, it downloads and installs the application it imitated. In this case, the Trojan requests administrator rights to combat its removal. The main purpose of Trojan.AndroidOS.Hiddad.an is aggressive display of adverts, its main “audience” is in Russia (86% of attacked users).
Third came Trojan.AndroidOS.Boogr.gsh (4.51%). Such verdict is issued for files recognized as malicious by our system based on machine learning. Despite the fact that this system can detect any types of malware, in Q1 2017, the most popular were advertising Trojans which used superuser privileges.
Eighth position in the ranking was occupied by Trojan-Dropper.AndroidOS.Hqwar.i (3.83%), the verdict used for the Trojans protected by a certain packer/obfuscator. In most cases, this name hides the representatives of the FakeToken and Svpeng mobile banking families.
The ranking also included Trojan-Banker.AndroidOS.Svpeng (2.49%), which was twelfth in the Top 20. This family has been active for three quarters in a row and remains the most popular banking Trojan in Q1 of 2017.
Trojan.AndroidOS.Agent.bw was sixteenth in the rating (1.79%). This Trojan, targeting primarily people in India (more than 92% of attacked users), just like Trojan.AndroidOS.Hiddad.an imitates popular programs and games, and once run, downloads and installs various applications from the fraudsters’ server.
The geography of mobile threats
The geography of attempted mobile malware infections in Q1 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile malware (ranked by percentage of users attacked)
| Country* | % of users attacked ** | |
| 1 | Iran | 47.35 |
| 2 | Bangladesh | 36.25 |
| 3 | Indonesia | 32.97 |
| 4 | China | 32.47 |
| 5 | Nepal | 29.90 |
| 6 | India | 29.09 |
| 7 | Algeria | 28.64 |
| 8 | Philippines | 27.98 |
| 9 | Nigeria | 27.81 |
| 10 | Ghana | 25.85 |
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
In Q1 2017, Iran was the country with the highest percentage of users attacked by mobile malware – 47.35%. Bangladesh came second: 36.25% of users there encountered a mobile threat at least once during the quarter. It was followed by Indonesia and China; the share of both countries was slightly over 32%.
Russia (11.6%) came 40th in this rating, France (8.1%) 57th, the US (6.9%) 69th line, Italy (7.1%) 66th, Germany (6.2%) 72nd, Britain (5.8%) 75th.
The safest countries were Finland (2.7%), Georgia (2.5%) and Japan (1.5%).
In all the countries of the Top 20, the same mobile objects – adware – are detected, and first of all, the representatives of the AdWare.AndroidOS.Ewind family as well as advertising Trojans.
Mobile banking Trojans
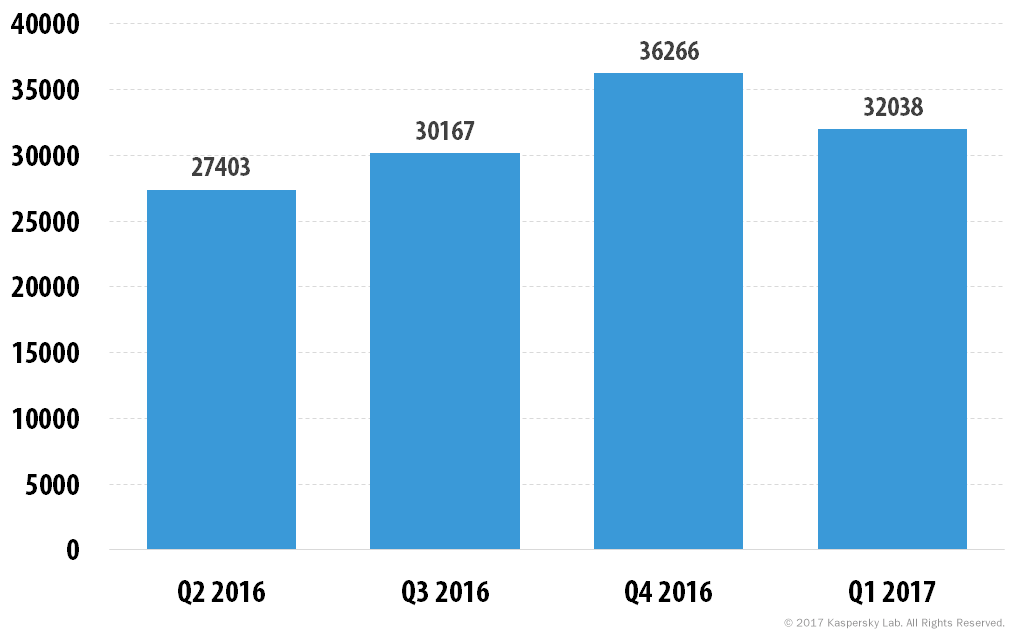
Over the reporting period, we detected 32,038 installation packages for mobile banking Trojans, which is 1.1 times as many as in Q4 2016.
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab solutions (Q2 2016 – Q1 2017)
Trojan-Banker.AndroidOS.Svpeng remained the most popular mobile banking Trojan for the third quarter in a row. This family of mobile banking Trojans uses phishing windows to steal credit card data and logins and passwords from online banking accounts. In addition, fraudsters steal money via SMS services, including mobile banking. Svpeng is followed by Trojans Trojan-Banker.AndroidOS.Faketoken.z and Trojan-Banker.AndroidOS.Asacub.san. It is worth noting that most of attacked users were in Russia.
Geography of mobile banking threats in Q1 2017 (percentage of all users attacked)
TOP 10 countries attacked by mobile banker Trojans (ranked by percentage of users attacked)
| Country* | % of users attacked** | |
| 1 | Russia | 1.64 |
| 2 | Australia | 1.14 |
| 3 | Turkey | 0.81 |
| 4 | Uzbekistan | 0.61 |
| 5 | Tajikistan | 0.48 |
| 6 | Moldova | 0.43 |
| 7 | Ukraine | 0.41 |
| 8 | Kazakhstan | 0.37 |
| 9 | Kyrgyzstan | 0.32 |
| 10 | Singapore | 0.26 |
* We eliminated countries from this rating where the number of users of Kaspersky Lab’s mobile security product is relatively low (under 10,000).
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
Although the Svpeng family topped the rating of the most popular mobile banking Trojans in the first quarter of 2017, its activity declined compared to the third quarter of 2016: the share of users attacked by these malicious programs in Russia dropped almost twofold – from 3.12% to 1.64%. At the same time, Russia remained the TOP 20leader.
In second place was Australia (1.14%), where the Trojan-Banker.AndroidOS.Acecard and Trojan-Banker.AndroidOS.Marcher families were the most popular threats. Turkey (0.81%) rounded off the Top 3.
Mobile Ransomware
In Q1 2017, we detected 218, 625 mobile Trojan-Ransomware installation packages which is 3.5 times more than in the previous quarter.
Number of mobile Trojan-Ransomware installation packages detected by Kaspersky Lab (Q2 2016 – Q1 2017)
In the first half of 2016, we saw the increase in the number of mobile ransomware installation packages caused by the active spread of the Trojan-Ransom.AndroidOS.Fusob family. In the second half of the same year, the activity of this family fell, which affected the number of detected installation packages. The growth resumed in the fourth quarter of 2016 and sharply accelerated in Q1 2017. The reason was the Trojan-Ransom.AndroidOS.Congur family – more than 86% of detected mobile ransomware installation packages belonged to this family. Usually, the representatives of Congur have very simple functionality – they change the system password (PIN), or install it if no password was installed earlier, thus making it impossible to use the device, and then ask that user to contact the fraudsters via the QQ messenger to unblock it. It is worth noting that there are modifications of this Trojan that can take advantage of existing superuser privileges to install their module into the system folder.
Despite this, Trojan-Ransom.AndroidOS.Fusob.h remained the most popular mobile Trojan-Ransomware in the first quarter, accounting for nearly 45% of users attacked by mobile ransomware. Once run, the Trojan requests administrator privileges, collects information about the device, including GPS coordinates and call history, and downloads the data to a malicious server. After that, it may receive a command to block the device.
Geography of mobile Trojan-Ransomware in Q1 2017 (percentage of all users attacked)
TOP 10 counties attacked by mobile Trojan-Ransomware (ranked by percentage of users attacked)
| Country* | % of users attacked** | |
| 1 | USA | 1.23 |
| 2 | Uzbekistan | 0.65 |
| 3 | Canada | 0.56 |
| 4 | Kazakhstan | 0.54 |
| 5 | Italy | 0.44 |
| 6 | Germany | 0.37 |
| 7 | Korea | 0.35 |
| 8 | Denmark | 0.30 |
| 9 | United Kingdom | 0.29 |
| 10 | Spain | 0.28 |
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile Trojan-Ransomware, relative to all users of Kaspersky Lab’s mobile security product in the country.
The US topped the ranking of ten countries attacked by mobile Trojan-Ransomware; the most popular family there was Trojan-Ransom.AndroidOS.Svpeng. These Trojans appeared in 2014 as a modification of the Trojan-Banker.AndroidOS.Svpeng mobile banking family. They demand a ransom of $100-500 from victims to unblock their devices.
In Uzbekistan (0.65%), which came second, most of mobile ransomware attacks involved Trojan-Ransom.AndroidOS.Loluz.a. This is a simple Trojan that blocks operation of a device with its own window and asks the user to contact the fraudsters by phone to unblock it.
Fourth place was occupied by Kazakhstan (0.54%). The main threat to users originated from representatives of the Small mobile Trojan-Ransom family. This is a fairly simple ransomware program that blocks operation of a device by overlaying all the windows on the device with its own window and demanding $10 to unblock it.
In all other countries of the TOP 10, the most popular Trojan-Ransom family was Fusob.
Vulnerable apps exploited by cybercriminals
The first quarter of 2017 was marked by the return of the degenerated exploit kit Neutrino, which had departed the cybercriminal market in the third quarter. Following Magnitude, Neutrino is changing the distribution format and abandoning wide-scale campaigns to become a “private” exploit kit. Several new players – Nebula, Terror, and other –tried to fill the vacant niche but failed: after a brief burst of activity their distribution quickly came to naught. At the moment, RIG and its modifications remain the most popular and advanced public exploit kit.
The Q1 statistics show an almost 10% decline in the number of attacked users. This is primarily caused by weak exploit kit environment, as well as the decrease in the effectiveness of exploits in general. Adobe Flash remained the only platform that demonstrated growth: although no new vulnerabilities for it had been discovered, the number of attacked users grew by 20%. The biggest decrease fell on exploits for different browsers – only 44% of attacks targeted them (against 54% in the previous quarter).
CVE-2016-0189, CVE-2014-6332 and CVE-2013-2551 remain the most popular vulnerabilities in the first quarter. Of note were also vulnerabilities in the Microsoft Edge Chakra engine, published in open access in early 2017. In addition to the detailed description of vulnerabilities, the research included a ready-to-use Proof of Concept, which shortly after the publication was integrated in the Sundown exploit kit from which it moved to Neutrino, Kaixin and others. However, exploitation of these vulnerabilities was not reliable enough, while patches for them were released as far back as in November along with the MS16-129 update, so they have not become widely spread and are now almost out of use.
Distribution of exploits used in attacks by the type of application attacked, Q1 2017
In Q1 2017, especially popular were campaigns involving mass mailings of infected documents – to distribute them, Microsoft Office exploits were used. Although the share of attacked office package users has not changed much, the same users were attacked several times – on average, one attacked user received 3 malicious documents over the quarter.
The general trend is towards the increase in the share of social engineering when delivering malware to the computer of a potential victim. Campaigns involving distribution of infected messages are always based on forcing a user to perform certain actions: unpack a file from the password-protected archive, issue a permission to execute macros from the document, etc. This method is currently beginning to be applied in exploits for browsers. Magnitude, for example, offers the Internet Explorer 11 and Windows 10 users to download a malicious file under the guise of antivirus update for Microsoft Defender. Some spam campaigns are based on imitating the Google Chrome update page. We believe that this trend will continue in the future – such campaigns are easier to maintain and implement, and their level of “penetration” is constantly growing.
Online threats (Web-based attacks)
Online threats in the banking sector
These statistics are based on detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data. Beginning from the first quarter of 2017 the statistics include malicious programs for ATMs and POS terminals but does not include mobile threats.
Kaspersky Lab solutions blocked attempts to launch one or several malicious programs capable of stealing money via online banking on 288,000 computers in Q1 2017.
Number of users attacked by financial malware, January – March 2017
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM and POS-malware worldwide, we calculate the percentage of Kaspersky Lab product users in the country who encountered this type of threat during the reporting period, relative to all users of our products in that country.
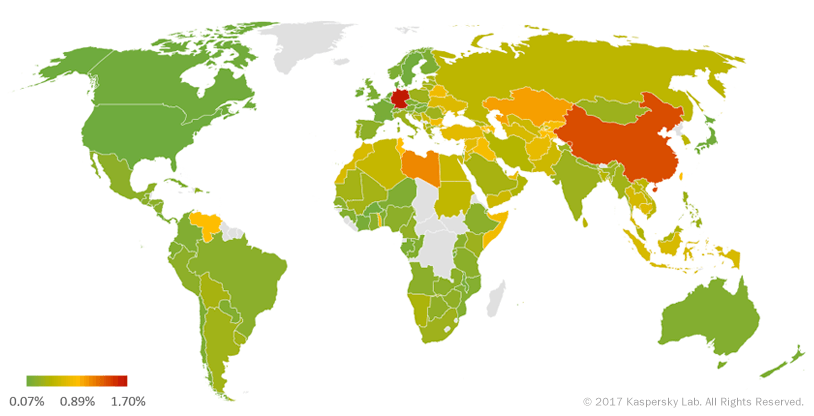
Geography of banking malware attacks in Q1 2017 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
| Country* | % of attacked users ** | |
| 1 | Germany | 1.70 |
| 2 | China | 1.37 |
| 3 | Libya | 1.12 |
| 4 | Kazakhstan | 1.02 |
| 5 | Palestine | 0.92 |
| 6 | Togo | 0.91 |
| 7 | Tunisia | 0.89 |
| 8 | Armenia | 0.89 |
| 9 | Venezuela | 0.88 |
| 10 | Taiwan | 0.87 |
These statistics are based on detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
*We excluded those countries in which the number of Kaspersky Lab product users is relatively small (under 10,000).
** Unique users whose computers have been targeted by banking Trojan attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In the first quarter of 2017, Germany (1.70%) had the highest proportion of users attacked by banking Trojans. It was followed by China (1.37%). Libya (1.12%) rounded off the Top 3.
As for the contribution of the other European countries in the Q1 rating, for example, Spain (0.24%) was on 89th position and the UK (0.15%) came 126th.
The TOP 10 banking malware families
The table below shows the TOP 10 malware families used in Q3 2016 to attack online banking users (as a percentage of users attacked):
| Name* | % of attacked users** | |
| 1 | Trojan-Spy.Win32.Zbot | 45.93 |
| 2 | Trojan.Win32.Nymaim | 29.70 |
| 3 | Trojan.Win32.Neurevt | 3.31 |
| 4 | Trojan-Banker.Win32.Gozi | 3.15 |
| 5 | Trojan-Spy.Win32.SpyEyes | 2.71 |
| 6 | Backdoor.Win32.ZAccess | 2.11 |
| 7 | Backdoor.Win32.Shiz | 1.67 |
| 8 | Trojan.Multi.Capper | 1.67 |
| 9 | Trojan.Win32.Tinba | 1.00 |
| 10 | Trojan.Win32.Shifu | 1.00 |
*The detection verdicts of Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malware in question as a percentage of all users attacked by financial malware.
As in the last year, in Q1 2017, Trojan-Spy.Win32.Zbot (45.93%) topped the rating of the most popular malware families. Its source codes have been publicly available since a leak and are now widely exploited as an easy-to-use tool for stealing user payment data. Unsurprisingly, this malware consistently tops this rating – cybercriminals regularly enhance the family with new modifications compiled on the basis of the source code and containing minor differences from the original.
Second came Trojan.Win32.Nymaim (29.70%). The first modifications of malware belonging to this Trojan family were downloaders, which blocked the infected machine with the help of downloaded programs unique for each country. Later, new modifications of the Trojan.Win32.Nymaim family malware were discovered. They included a fragment of Gozi used by cybercriminals to steal user payment data in online banking systems. In Q1 2017, Gozi (3.15%) was on 4th position in the rating.
Trojan.Win32.Neurevt (3.31%) rounded off the Top 3. It is a multifunctional Trojan written in C ++. It uses rootkit technologies to conceal its presence in the system, injects its own code into all running processes, blocks the work of some anti-virus programs, and can monitor and block installation of other common Trojans.
Ransomware Trojans
A total of 11 new cryptor families and 55, 679 new modifications were detected in Q1 2017.
The number of newly created cryptor modifications, Q2 2016 – Q1 2017
Most of detected modifications belonged to the Cerber family (the Trojan-Ransom.Win32.Zerber verdict). This cryptor, first discovered a year ago, continues to evolve, and we regularly detect its new improved versions.
The number of users attacked by ransomware
In Q1 2017, 240, 799 unique KSN users were attacked by cryptors.
Number of unique users attacked by Trojan-Ransom cryptor malware (Q1 2017)
This figure is almost half as much as that of the fourth quarter of 2016, but one should not consider it a receding threat. It is most likely that this difference is related to the methodology while the actual number of incidents is higher: the statistics only reflect the results of signature-based and heuristic detection, whereas most of the Trojan ransomware is detected by Kaspersky Lab products using behavioral methods and issuing a generic verdict that does not allow distinguishing types of malware.
The geography of attacks
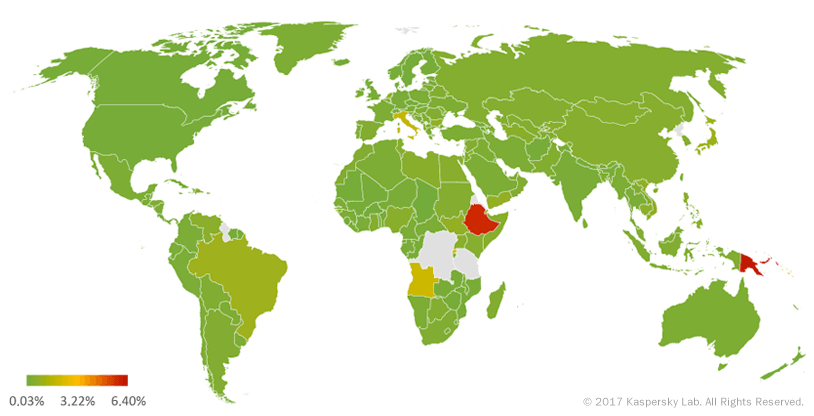
Geography of Trojan-Ransom attacks in Q1 2017 (percentage of attacked users)
Top 10 countries attacked by cryptors
| Country* | % of users attacked by cryptors ** | |
| 1 | Italy | 1.87% |
| 2 | Brazil | 1.07% |
| 3 | Japan | 0.99% |
| 4 | Vietnam | 0.74% |
| 5 | Netherlands | 0.73% |
| 6 | Cambodia | 0.70% |
| 7 | Uganda | 0.66% |
| 8 | Philippines | 0.65% |
| 9 | Venezuela | 0.63% |
| 10 | Nigeria | 0.60% |
* We excluded those countries where the number of Kaspersky Lab product users is relatively small (under 50,000).
** Unique users whose computers have been targeted by ransomware as a percentage of all unique users of Kaspersky Lab products in the country.
Italy, which was not in the Top 10 in the third quarter of 2016, now took the lead the Q1 ranking (1.87%). Second came Brazil (1.07%), the newcomer to the Top 10. This correlates with our observations that indicate an increase in the number Trojan ransomware targeting victims in Brazil. One of the examples of such malicious software was Xpan, which we analyzed last year.
Japan (0.99%), which ranked first in the second and third quarters of 2016, moved two places down but still remains at the top of the rating.
Top 10 most widespread cryptor families
| Name | Verdict* | % of attacked users** | ||
| 1 | Cerber | Trojan-Ransom.Win32. Zerber | 18.04% | |
| 2 | Spora | Trojan-Ransom.Win32.Spora | 7.59% | |
| 3 | Locky | Trojan-Ransom.Win32.Locky | 7.35% | |
| 4 | Sage | Trojan-Ransom.Win32.SageCrypt | 3.44% | |
| 5 | Cryrar/ACCDFISA | Trojan-Ransom.Win32.Cryrar | 3.20% | |
| 6 | Shade | Trojan-Ransom.Win32.Shade | 2.82% | |
| 7 | (generic verdict) | Trojan-Ransom.Win32.Gen | 2.37% | |
| 8 | Crysis/Dharma | Trojan-Ransom.Win32.Crusis | 2.30% | |
| 9 | CryptoWall | Trojan-Ransom.Win32.Cryptodef | 2.25% | |
| 10 | (generic verdict) | Trojan-Ransom.Win32.Snocry | 2.16% |
* These statistics are based on detection verdicts received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by a specific Trojan-Ransom family as a percentage of all users of Kaspersky Lab products attacked by Trojan-Ransom malware.
The Trojan Cerber (18.04%) was the most widespread in the number of attacked users in the first quarter of 2017. It is no wonder, considering a huge number of this cryptor’s modifications and its active distribution by fraudsters.
Spora (7.59%) was on the second place. This new Trojan was first discovered in January 2017 and at the “dawn of its career” only attacked Russian-speaking victims. However, a few weeks after its detection Spora spread around the world and by the end of the first quarter entered the top three most popular cryptors. The third position was occupied by Locky (7.35%) which appeared about a year and has recently reduced its activity a little.
Yet another new Trojan is Sage (3.44%). Like Spora, it emerged in the first quarter of 2017 and came fourth in the Q1 rating. The rest places went to our “old acquaintances”, which appeared in the reports for the previous quarters.
Of special note is the finding of the quarter the cryptor PetrWrap, which is used by cybercriminals for targeted attacks on organizations. Statistics show that this type of attacks is gaining popularity.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q1 2017, Kaspersky Lab solutions blocked 479, 528, 279 attacks launched from web resources located in 191 countries around the world. 79, 209, 775 unique URLs were recognized as malicious by web antivirus components.
Distribution of web attack sources by country, Q1 2017
The Netherlands (38%) took the lead in the number of web attack sources. The United States (30%), which used to top this rating for several quarters in a row, dropped to second place, although the share of this country remained almost unchanged from the 2016’s figures. Germany (9%) rounded off the Top3.
Russia (4%) and France (3%) were fourth and fifth respectively.
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers work in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
| Country* | % of users attacked** | |
| 1 | Algeria | 37.67 |
| 2 | Belarus | 33.61 |
| 3 | Tunisia | 32.04 |
| 4 | Ukraine | 31.98 |
| 5 | Kazakhstan | 29.96 |
| 6 | Azerbaijan | 29.95 |
| 7 | Albania | 29.80 |
| 8 | Bangladesh | 29.51 |
| 9 | Qatar | 29,41 |
| 10 | Armenia | 29.02 |
| 11 | Greece | 28.21 |
| 12 | Moldova | 27.46 |
| 13 | Venezuela | 27.37 |
| 14 | Kyrgyzstan | 27.02 |
| 15 | Vietnam | 26.87 |
| 16 | Russia | 26.67 |
| 17 | Morocco | 25.65 |
| 18 | Sri Lanka | 25.42 |
| 19 | Brazil | 25.10 |
| 20 | Serbia | 24.18 |
These statistics are based on detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* These calculations excluded countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
** Unique users whose computers have been targeted by Malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 20.05% of computers connected to the Internet globally were subjected to at least one Malware-class web attack during the quarter.
Geography of malicious web attacks in Q1 2017 (ranked by percentage of users attacked)
The countries with the safest online surfing environments included Luxembourg (14.4%), Germany (13.9%), Norway (13.83%), South Africa (12.5%), the United States (10.56%), Uganda (10.29%) and Japan 9.18%).
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q1 2017, Kaspersky Lab’s file antivirus detected 174, 989, 956 unique malicious and potentially unwanted objects.
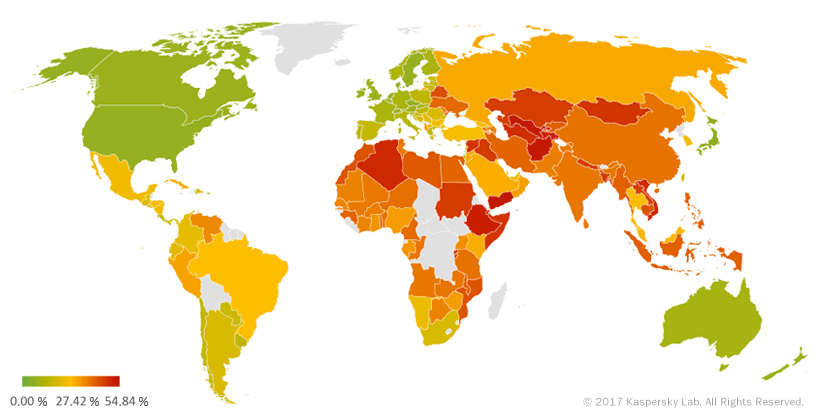
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus was triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
The rating of malicious programs only includes Malware-class attacks. The rating does not include web antivirus module detections of potentially dangerous or unwanted programs such as RiskTool or adware.
| Country* | % of users attacked** | |
| 1 | Yemen | 54.84 |
| 2 | Afghanistan | 54.27 |
| 3 | Uzbekistan | 53.80 |
| 4 | Tajikistan | 51.32 |
| 5 | Ethiopia | 50.87 |
| 6 | Djibouti | 50.03 |
| 7 | Algeria | 49.38 |
| 8 | Vietnam | 49.15 |
| 9 | Turkmenistan | 48.39 |
| 10 | Rwanda | 47.57 |
| 11 | Mongolia | 47.25 |
| 12 | Somalia | 46.96 |
| 13 | Syria | 46.96 |
| 14 | Bangladesh | 46.64 |
| 15 | Iraq | 46.59 |
| 16 | Sudan | 46.35 |
| 17 | Nepal | 46.19 |
| 18 | Kazakhstan | 46.00 |
| 19 | Laos | 45.39 |
| 20 | Belarus | 43.45 |
These statistics are based on detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (under 10,000 users).
** The percentage of unique users in the country with computers that blocked Malware-class local threats as a percentage of all unique users of Kaspersky Lab products.
An average of 23.63% of computers globally faced at least one Malware-class local threat during the third quarter. Russia’s contribution to this rating accounted for 30.51%.
The safest countries in terms of local infection risks were: Poland (14.85%), Singapore (12.21%), Italy (13.30%), France (11.15%), Australia (10.51%), Great Britain (9.08%), Canada (8.66%), the Czech Republic (7.83%), the United States (7.57%), Denmark (6.35%), Japan (6.18%).

































IT threat evolution Q1 2017. Statistics