
It’s brilliant — but is it user-friendly?
The idea behind Default Deny is very simple and logical. However, until now this approach was focused exclusively on a very narrow target audience. This was primarily because of the technical challenges arising on the road toward developing a solution that would be appropriate for broad use, and without a number of critical limitations.
New developments in Application Control
Using Default Deny mode entails a shift in priorities when selecting security policies — moving away from user freedom and convenience toward accomplishing the main goal of any data security system: minimizing the risk of data leakages and/or the loss of any critical business data.
However, the early forms of strict application control system caused major function limitations that made the use of this arrangement nearly impossible. Maintaining a quality Default Deny mode requires additional functions, or else a corporate network may not be able to operate as needed.
When transitioning to the Default Deny mode, a sysadmin will need to tackle a number of tasks. In order to make the process easier, Application Control — as the main component that will be managing a corporate network’s applications — must first undergo some substantial changes.
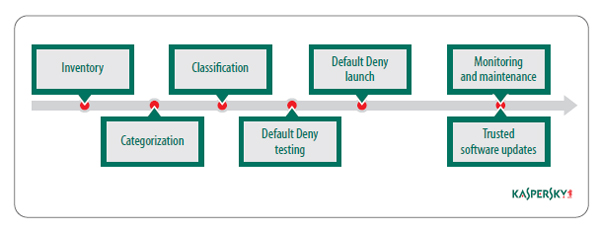
So, the use of Default Deny mode is possible and practical only after the following functions are put into place:
- Inventory – collecting information about all of the software programs installed on the corporate network, all computers, and all network resources.
- Categorization – dividing up the inventoried software into functional groups: OS components, browsers, multimedia, games, etc.
- Configuration, or Application Management – introducing Application Control restrictions for certain users or groups of users for certain application categories (basically defining security policies).
- Dynamic Allowlist – a knowledge base about all of the varieties of software around the world. Current and regularly updated information about applications, their reputations, categories, and popular or recommended analogues. This is expert-level data that is supplied by security solution developers.
- Software security update mechanisms – autonomous means of maintaining regular updates for commonly used software, thus relieving administrators of the need to repeatedly go through the lengthy procedures of identifying and legalizing applications that are updated on the network.
- Maintaining a list of trusted users and software sources – tools provided to network administrators, security engineers for simple, convenient ways to legalize software. In particular, this involves creating lists of trusted network resources on the Internet and the local corporate network (HTTP/FTP/Shared Folders/etc.) – sources of clean apps that are permitted for installation and use.
- Testing and supporting a beta mode – a means of static or dynamic detection of systemic collisions arising during the introduction of security policies (incompatibility / inoperativeness of various applications) that could lead to interference in business processes.
- User feedback and support – tools for managing incidents to ease the user-support process as much as possible.
- Monitoring and audit – various tools for collecting, aggregating, and standardizing reports.
We will now address the Allowlist Security Approach component in more detail. WSA is a dynamic database of clean files (a Dynamic Allolist). Interest in Dynamic Allowlists stems from both technical and organizational aspects, without which it would not be possible to achieve the Allowlist’s maximum effect.
The Dynamic Allowlist
So, what is a Dynamic Allowlist? It is essentially a knowledge base about all of the different types of legitimate software programs. From a technical point of view, a Dynamic Allowlist is an enormous database of “clean” software that can be continuously updated with different types of files, including new installation files, and – most importantly – information about these objects. The quality and completeness of the data in these types of expert-level data resources depends on their suppliers. Leading security software developers are the ones compiling Dynamic Allowlists.
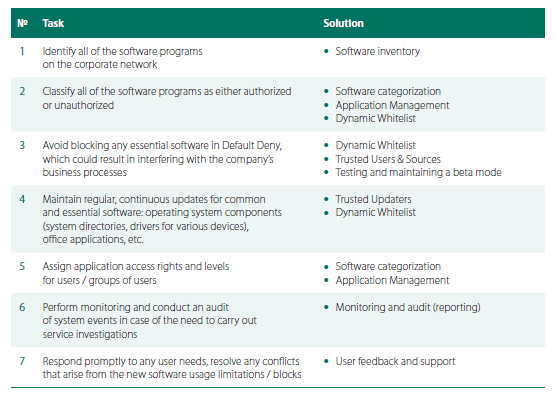
A Dynamic Allowlist is a necessary component for three of the seven tasks that need to be accomplished to make Default Deny work (see the table above). Clearly, the quality of the solution provided by a vendor will have a direct correlation to the quality of the database in that solution.
To accomplish the tasks above, the Allowlist should contain:
- A software database: the developer, product name, latest version, other information primarily derived from the attributes of each program.
- Additional information (expert-level data):
- information about the risk level – software classification, its reputation: trusted, untrusted, potential threat, etc.
- software category: OS component, browser, games, office apps, etc.
- the software’s business purpose: accounting and finance, marketing, HR, CRM, logistics, etc.
- software alternatives – data about similar programs
- statistics – prevalence, regional distribution, etc.
What other requirements are there for Dynamic Allowlists aside from data?
First and foremost, a Dynamic Allowlist should be dynamic, as its name implies. Each day, multiple new legitimate applications and updates for existing applications are released. That means that security software developers have to respond immediately to any changes in the software world, and promptly update their knowledge bases. In order to do that, they must also regularly and promptly add entries to their databases of clean software programs from the many sources from different parts of the world. These updates must take place automatically, since the volumes of data are enormous (terabytes of data every day). For this purpose, suppliers of Dynamic Allowlists send so-called ‘crawlers’ out onto the Internet — crawlers act as search agents that monitor new software and, when needed, download new applications.
To keep databases up to date, it is also important to develop technological partnerships among vendors and major manufacturers and distributors, i.e., independent software vendors. The goal of these partnerships is to obtain, process, and analyze (classify and categorize) new software before it is publicly released in order to minimize any false positives or instances where a security solution and a partner’s software are incompatible.
Another possible source of data for keeping databases up to date is a global data network created by a vendor based on user communities. This type of data network offers a major competitive edge — it helps track metadata about the software launched on user computers, and it adds data on the emergence of new apps and different software updates to the knowledge base.
| Kaspersky Lab uses all of these components to replenish its Dynamic Allowlist. Kaspersky Lab currently works with several hundred international partners and tens of millions of participants in the Kaspersky Security Network global data network, in addition to an extensive network of automated search agents. Combined, these components provide continuous updating of Kaspersky Lab’s dynamic knowledge bases, with an average of over one million new files per day.
The quality of Kaspersky Lab’s Dynamic Allowlist was proven in an independent test conducted by West Coast Labs. The study showed that Kaspersky Lab’s database contains data on 94% of all clean software released around the world. |
It is necessary to carefully control all of the programs entered into the Dynamic Allowlist, and most importantly to keep its reputation up to date. A program classified as ‘clean’ today can, after more careful analysis, turn out to be a carrier of threatening malicious code tomorrow.
Note that regularly scanning the Dynamic Allowlist is no small task. In addition to automated data processing and analysis, it also requires a team of specialists capable of analyzing program code with potential logical collisions and issuing a final verdict. Small companies and developers of “free” antivirus products cannot afford these types of dedicated antivirus labs. Furthermore, the specifics involved in processing malicious and clean software are different. Ideally, a company will not just have a dedicated antivirus lab but also a specialized Allowlisting lab where experts track incoming data flows, study intellectual systems, and respond promptly to emergencies (Kaspersky Lab has such a dedicated Allowlisting Lab).
From theory to practice: Kaspersky Lab’s Endpoint 10
Corporate network admins are faced with complex, often repetitive tasks to support numerous, multi-purpose workstations. The Allowlist Security Approach (i.e., Default Deny mode) guarantees a much higher security level for corporate networks. Furthermore, running a network on Default Deny mode, with its strict system restrictions, requires that the products involved in the system are capable of large-scale task automation to facilitate system administration.
Let us take a look at how the transition from theory to practice is made using Kaspersky Lab’s Endpoint Security solutions as an example, following the program step-by-step through its life cycle, from software inventory to corporate network maintenance (after product installation).
Allowlist Security Approach was first used in Kaspersky Endpoint Security for Windows 8 in 2011. In 2013, Kaspersky Endpoint Security for Windows 10 offers even more functionality, including in the area of Application Control.
 Stages in the Default Deny life cycle
Stages in the Default Deny life cycle
- Inventory. Right after the product is installed, an administrator will need to conduct an automatic software inventory of all of the software installed on the corporate network. Here, Kaspersky Endpoint Security collects information about all of the software programs installed on network computers and other network resources.
 Software inventory results for a specific directory
Software inventory results for a specific directory - Categorization (automatic, using Dynamic Allowlist) After the automatic inventory, all software programs are then categorized, and divided into groups according to the rules set out in the product (OS, multimedia, devices, games, browsers, etc.). This function is not offered by all Application Control solution developers. We believe, however, that this function is essential in facilitating the management of a large number and variety of software programs installed on corporate networks. That is why the Dynamic Allowlist has 16 different categories at the top level and 96 sub-categories (see our category catalog).
 Kaspersky Lab’s category catalog
Kaspersky Lab’s category catalog
In order to define the critically important OS components and drivers, Kaspersky Endpoint Security includes a special category of OS files called Golden Image. This category includes all of the requisite components for Win XP, Vista, Win7, Win8 (32 and 64) and over 15 localizations for each (over 100 versions and localizations). All an administrator has to do is add files into the Golden Image category from the local allowlist database, and the Default Deny configuration is ready.
- Categorization (manual). It’s important to take into account the fact that a allowlist from any security solution developer cannot contain data about every single software program installed on a company’s network. For example, companies often have specialized proprietary software developed either by the company itself or custom-made. Kaspersky Endpoint Security 10’s Application Control allows admins to create a local allowlist. Furthermore, Kaspersky Endpoint Security 10 also features multi-vector categorization — in other words, one application can be in several categories at once.
 Option for user file categorization
Option for user file categorization - Configuration. Kaspersky Endpoint Security offers the ability to manage categorized software for specific users and groups of users. For example, software in the Accounting category can be approved for accountants only, so that no other users will have access to the company’s financial data.It is at this stage that the use of unlicensed or non-essential software can be restricted. For example, it is possible to block the use of any software for which the company does not hold the requisite licenses, or block instant messaging programs like Skype, for example. It is also possible to block the use of specific versions of software, such as blocking all browsers except for a specific version of Internet Explorer.
- Secure software updates. The automatic software updates in Kaspersky Endpoint Security features Trusted Updaters technology, which helps perform secure update procedures for products while factoring in the complex sequence of program actions executed during the update process.
- Testing and maintaining a test mode. Since introducing strict network policies involves a good deal of responsibility, we have also incorporated a special Test Mode that a system administrator can use for modeling and evaluating how any rule works in practice. Applications aren’t actually blocked in Test Mode, but an administrator can see what the system looks like based on reports, and what would happen if a particular system arrangement were running. This helps sysadmins make the appropriate adjustments to the rules before officially rolling out new policies without causing any negative responses from users and without interfering in company business processes in the event that work becomes more difficult as a result of new policies.
- User feedback and support. A company’s IT environment is ever-changing, which is why users should have the ability to ask a system administrator for permission to launch new software, and sysadmins should be able to either block or allow that request by simply pressing a button in a user-friendly interface. Kaspersky Lab’s product provides the ability for both. To ensure flexibility — even in Default Deny mode — Kaspersky Lab allows administrators to manage user complaints and requests. If it turns out that a certain application is blocked but the user believes that application is essential to perform his official duties, all he has to do is click on “Send a Request” and a notification will automatically be sent to the administrator.
 An example of a message automatically sent to a system administrator in the event that an application is blocked
An example of a message automatically sent to a system administrator in the event that an application is blocked
Over the last year, independent test labs have started working more with Application Control. Right away, two companies verified the effectiveness of Application Control technology for protection against targeted attacks and managing unauthorized software. In early 2012, West Coast Labs published a report on the results of the industry’s first independent test, where Kaspersky Lab’s technology ranked first.
Later, Dennis Labs also conducted a comparative study, and in early 2013 released the results. Once again, Kaspersky Lab was ranked among the best.
Conclusion
The increased number and, most importantly, the complexity of threats means that antivirus software developers have to search out new solutions to provide corporate networks with effective protection. Allowlist Security Approach is a new method that allows only trusted, allowlisted programs to launch and run. As a result, a malicious program cannot simply launch on a system. This approach provides protection against complex and unknown threats, including targeted attacks.
Allowlist Security Approach is a new development in Application Control that complements the Default Deny mode and Dynamic Allowlist technologies.
Using the heightened-security Default Deny mode means introducing additional functions. Application Control should include several simple mechanisms, such as inventory, categorization, configuration (Application Management), flexible local allowlist policy management, and the ability to use a cloud-based Dynamic Allowlist, capable of responding immediately to regular changes in the software world. Furthermore, functions such as testing and support in a Test Mode are important for making the transition to Default Deny mode properly.
Allowlist Security Approach helps system administrators accomplish a number of tasks:
- Control (allow, block, flexibly restrict or audit) the launch of clean apps on workstations in line with the company’s security policies
- Receive expert-level data about the status of files from the Dynamic Allowlist database directly from software developers
- Guarantee steady operation of clean, permitted applications
- Manage software categories, rather than specific applications
- At the stage of corporate usage, monitor, control, and respond to problems that result when an application is blocked
- Streamline the use of company IT resources and boost performance by controlling the use of third-party and unlicensed software on the network.
Application Control and Default Deny mode together are powerful, convenient tools that simplify a system administrator’s job when it comes to managing corporate network workstations and keeping them secure.
At Kaspersky Lab, we believe that the Allowlist Security Approach is a key tool in the corporate network security of the future. At the same time, we believe there is no panacea or one single technology capable of protecting computers against all threats. That is why the best choice for corporate networks is the use of a powerful endpoint product that combines a variety of protection technologies. Only multi-level system security and control can provide the highest possible level of protection for corporate networks.

















Application Control: the key to a secure network – Part 2