
Spam in the spotlight
In September, “Nigerian” scammers sent out stories relating to the breaking news of the Ebola epidemic. There was festive spam, focusing on both the US Labor Day celebration and the upcoming winter holidays: spammers have started to offer products and services for Christmas. A large part of the major theme mailings promoted products and services using popular social networking sites: the spammers promised an instant influx of new customers and income growth.
The Ebola virus in “Nigerian” spam
In July, the first reports about the Ebola outbreak in Africa appeared in the media. While the world’s attention was focused on how to fight the epidemic and prevent it spreading further, scammers used the disease to create new stories for their “Nigerian” letters.
In September, we came across several mailings which mentioned Ebola. In addition to the popular “Nigerian” legends written supposedly on behalf of people with various diseases the fraudsters made up quite unusual stories. For example, an email from a rich Liberian lady dying from Ebola contained a long story about her children who died from the virus and about the local medical center which refused to help her. She was willing to donate more than $1.5 million to a recipient who would transfer this money to charities. The message contained a detailed description of the situation that is unusual for “Nigerian” letters. However, this long story was still nothing more than yet another trick to make recipients believe the story and start corresponding with the scammers.
The authors of another fraudulent mailing introduced themselves as an employee of the World Health Organization and tried an unusual tack to attract attention – the reader was invited to a conference where Ebola would be discussed along with other medical issues. The recipient was not only invited to participate in the conference as a guest but was also offered 350,000 Euro and an automobile for his work as the WHO Representative in the UK. If the victim was interested in the offer, he had to provide his personal data. Apparently, the scammers hoped that the offer of money and work in an international company would ease all the user’s doubts.
Holiday spam
In early September, the United States celebrated Labor Day and the spammers were determined not to miss out on the event. Traditionally, in the run-up to the holidays people are attracted by discounts and sales. This time, companies selling print cartridges offered discounts not only for Labor Day but also the beginning of the new school year. Pharmaceutical spam advertizing drugs for weight loss also offered discounts related to the holiday.
Spam traffic around the world also contained adverts for goods and services related to Christmas. English-language messages offered a Christmas party on board a ship and urged early booking to get the lowest prices. In addition, the spammers encouraged people to start thinking of buying Christmas gifts in September and order digital devices directly from Chinese manufacturers as well as ordering a Christmas tree for the holiday.
Earnings and advertising on social networking sites
Another major theme this month was spam messages advertising various ways to earn money online using popular social networking sites. Most often, spammers offered to create an individual profile or a group in Twitter, Facebook or LinkedIn, to design a page according to the concept of the company and the goods it sells, to provide the first subscribers as well as to create the primary content and begin to actively promote it. Naturally, all this came at a cost. After such a comprehensive approach to creating a community in a social network the authors of the mailings promised a sharp increase in the customer numbers and sales volumes. Users were asked to apply by following a link in the email.
Spammers also spent plenty of time offering professional business promotion by placing photos and videos on specialist social networking sites. The authors of these mailings also promised to provide their customers with the necessary number of subscribers, for example, in Instagram, to place the photos of goods and to achieve the first results within the next three days. The recipients were often invited to make a video presentation of the company or the product and to post it on the popular video hosting YouTube. The spammers also promised that users could make “an obscene amount of money” with the help of YouTube by spending just 40 minutes a day on it. However, these mailings were nothing more than adverts about yet another author marketing course on DVD. To buy the DVD the recipient needed to follow a link in the email to enter the necessary website and make an order.
In September, we also came across the mailings containing invitations to seminars and webinars dedicated to the “art” of group and community administration on social networks. The authors of these training sessions promised to reveal all the secrets of an administrator’s work (for example, on Facebook or LinkedIn), leading to a stable monthly income for students. To register for a webinar, the recipient had to click on the link in the email.
According to the authors of foreign language spam mailings, the most popular source for attracting new customers and revenue growth was, of course, Facebook. So the spammers proposed using the network to promote personal ads, to link specific redirects to posts and photos – in this case the number of potential customers would depend on the quality of the content and the willingness of the users to click the links published in the communities. To accomplish this, they suggested special software which could be bought via spam mailings. Sites with detailed descriptions of the software had been created a few months ago and their names contained such words as “customers”, “income”, “Facebook”
Statistics
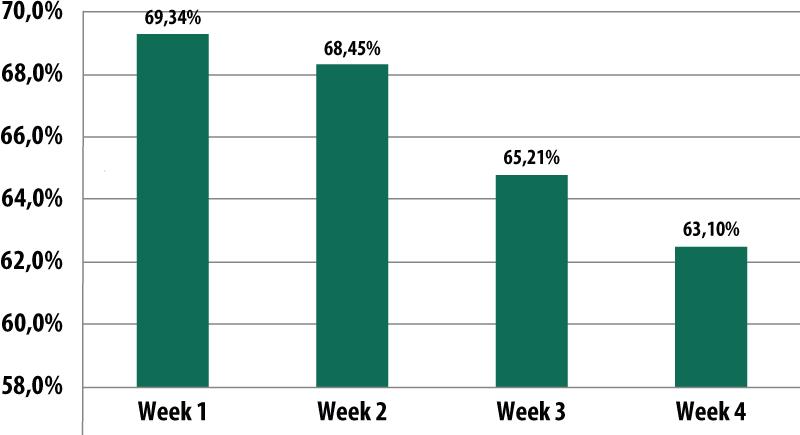
The percentage of spam in email traffic
The percentage of spam in email traffic
The percentage of spam in September’s email traffic averaged 66.5%, which is 0.7 percentage points down from August. The amount of unsolicited email consistently decreased throughout the month – in early September the percentage of spam averaged 69.3% while in the end it dropped to 63.1%.
Sources of spam by country
In September, the Top 3 most popular sources of spam were as follows. The USA remained in first position (12%) although its contribution was down nearly 4 percentage points from the previous month. Vietnam moved from fourth to second place with 9.3%; up 4.6 percentage points. Russia was in third place with 5.8% – there was little change in its numbers and it dropped one place in the table.
Sources of spam around the world
China was in 4th position with 5.6% of all distributed spam; its contribution dropped by nearly 1 pp. It is followed by India (4.7%): with almost 2 pp growth this country rocketed from 10th in August to 5th in September.
South Korea (3.2%) also increased its share by 1.3pp and placed 7th, up eight from the previous month. Meanwhile, Germany (2.9%) lost 0.7 pp and fell from 6th to 9th place in September. The Top 10 was completed with Taiwan with 2.5% of all distributed spam. France, Spain and Italy also produced a little more than 2% of the world spam.
Sources of spam in Europe by country
Vietnam was September’s leading source of spam sent to European users (11.1%). Next came the USA with 9.1% and Russia on 6%.
They are followed by China (5.3%), India (4.5%), Argentina (3.7%) and South Korea (3.5%). About 3% of European spam originated from each of Brazil, Germany and.
The rating also includes Taiwan (2.7%), Spain (2.6%), Italy (2.5%) and Mexico (2.3%) in 11th-14th place. Iran was in 15th position with 2.2% of spam sent to European users. The percentage of spam that originated from elsewhere did not exceed 2%.
Malicious attachments in email traffic
In September, the Top 10 malicious programs distributed via email were:
Top 10 malicious programs distributed via email
Dofoil:Trojan-Downloader.Win32.Dofoil.dx, Trojan-Downloader.Win32.Dofoil.dy and Trojan-Downloader.Win32.Dofoil.dz occupied 1st, 6th and 9th places respectively. This type of malware downloads other malicious programs onto the victim computer and uses them to steal user data (primarily passwords) which it then sends to the fraudsters.
Trojan-Spy.HTML.Fraud.gen was in 2nd position. As we wrote before, this piece of malware from the Fraud.gen family is a fake data entry HTML page that is sent to users by email, disguised as an important message from large commercial banks, online stores, software companies etc.
Trojan-Banker.HTML.PayPal.b came 4th. This malicious program appears in the form of the HTML page imitating a PayPal form. Recipients of an email containing this attachment is asked to fill in the form to update their PayPal account after the launch of the new IT security system. The German-language form includes fields like E-Mail Adresse, PayPal passwort, Vollständiger Name, Nachname der Mutter (Fakultativ), Geburtsdatum, Telefonnummer, Adresse, Stadt, Land, Postzahl, Kartennummer, Verfallsdatum, Kartenprüfnummer, VBV Passwort / MasterCard. It seems the fraudsters are targeting German-speaking PayPal users.
Trojan-Downloader.MSWord.Agent.ba and Trojan-Downloader.MSWord.Agent.bf placed 5th and 8th in the ranking. These programs imitate a .doc file with built-in macros written in Visual Basic for Applications (VBA), which are executed when opening the document. The macros download and run malicious software, such as representatives of the Andromeda family.
Trojan.Win32.Vundo.adc completed the list of the most popular malicious programs distributed via email. This program downloads other malware, for example, Trojan-Banker.Win32.Fibbit, which compromises the data passing through banking client applications. The Trojan intercepts keystrokes, copies data from the clipboard, searches for file certificates with the .jks extension, makes screenshots and tries to read the “keys.dat” file. All the stolen data is packed in the CAB archive and sent to the attacker’s server.
Distribution of email antivirus detections by country
For several month in a row, the three countries with the most antivirus detections have been Germany, the UK and the USA, each jostling for position at the top. In September, Germany took the lead (9.11%) followed by the UK (8.45%) and the USA (8.26%)
Russia was a big mover once again– after unexpectedly rising to 4th place in August it lost 4.14 percentage points and dropped down to 13th.
Special features of malicious spam
In September many mailings containing malicious attachments dealt with matters of hiring and firing. We registered a mass mailing that told recipient their employment contract withan organization (the company name varied from email to email) had been terminated for violations of the company’s internal policy. The messages even provided number and date of the alleged violations. The email also stated that recipients had already been issued written warnings demanding improved behavior in future. However, since nothing had been done, the labor contract was terminated.
To appeal this decision the recipient was invited to consult the lawyer before a specified deadline. The email contained an attached archive with documents about the supposed violations. To view the document, the recipient had to open the attachment. In fact, though, the attachment contained a representative of the Trojan-Downloader.Win32.Cabby family. This malware downloads other malicious software onto a victim computer, including various modifications of the Zbot family of programs.
Phishing
In September, Kaspersky Lab’s anti-phishing component registered 18,779,357 detections, 13,874,415 detections less than in the previous month. This decline in the amount of phishing was caused by the end of the summer slowdown and the beginning of the business season. It should also be noted that September is often a month for presentations and other major company events. In the run-up to these, phisher activity grows leading to a spike in the number of fraudulent attempts at the end of the summer
In September, Brazil (17.8%) was once again the leading country for phishing attacks, even though its share was down 1.7 percentage points. Australia dropped to 3rd with 11.1% of all antivirus detections. Second came India (13.4%). The UAE (10.5%) and France (10.4%) were in 4th and 5th positions respectively.
The geography of phishing attacks*, September 2014
* The percentage of users on whose computers the Anti-Phishing component was activated, from the total number of all Kaspersky Lab users
Top 10 countries by the percentage of attacked users:
| Country | % of users | |
| 1 | Brazil | 17.8 |
| 2 | India | 13.4 |
| 3 | Australia | 11.2 |
| 4 | UAE | 10.5 |
| 5 | France | 10.4 |
| 6 | Canada | 9.9 |
| 7 | China | 9.9 |
| 9 | Columbia | 9.4 |
| 8 | Bangladesh | 9.0 |
| 10 | UK | 8.0 |
Targets of attacks by organization
The statistics on phishing targets are based on detections made by Kaspersky Lab’s anti-phishing component. It is activated every time a user enters a phishing page that has not previously been included in Kaspersky Lab databases. It does not matter how the user enters this page – by clicking the link contained in a phishing email or in the message in a social network or, for example, as a result of malware activity. After the activation of the security system, the user sees a banner in the browser warning of a potential threat.
In September, Global Internet Portals were again the leading category among the organizations most often attacked by phishers with 24.7%, even though the share decreased by 6.1 pp. The contribution of Social networks (20.2%) rose by 2.8 pp from the previous month.
Organizations most frequently targeted by phishers, by category – September 2014
Financial phishing accounted for 36.9%of all detections made by Kaspersky Lab’s anti-phishing component, a 1.7 pp growth compared with the previous month. The percentage of detections affecting Banks accounted for 18.9% (+0.5pp), followed by online stores (11.4%, +1.4%) and E-payment systems (7.3%, +0.5%).
Top 3 organizations most frequently targeted by phishers
| Organization | % of detections | |
| 1 | 11.16% | |
| 2 | Yahoo! | 7.10% |
| 3 | 6.31% |
In September, Facebook (11.1%) was most heavily targeted by phishers: its share was up 1.1 pp. Yahoo came 2nd with 7.1% of all Anti-Phishing component detections. The share of Google services halved compared to August and accounted for 6.3%, placing this organization 3rd.
September’s spam traffic contained phishing mailings aimed at stealing logins and passwords to accounts with the popular Chinese online store Alibaba.com. The scammers tried to convince recipients to update their accounts or confirm their use with refer to a new security system and account maintenance. The design of fake the messages used the official logo and the Auto Signature of Alibaba.com as well as the standard anti-virus notification about the absence of threats in the email. The ‘From’ field named Alibaba.com as the sender and the sender’s address contained mainly legitimate domain names. However, on closer examination, an observant recipient could notice spelling mistakes in the addresses of senders and see domain names which obviously did not belong to the company.
Phishing pages were included directly in the fake emails and had a similar design. Recipients had to fill in the fields entering not only email addresses and passwords but also company names, countries of residence and mobile phone numbers. This way the fraudsters collected additional information about their victims for use in future scams.
Conclusion
In September, the percentage of spam in email traffic decreased by 0.7pp and averaged 66.5%. The main distributors of spam were the USA (12%), Vietnam (9.3%) and Russia (5.8%).
A Trojan downloader from the Dofoil family topped the rating of the most popular malware spread via email. This malicious program is used to download other malware onto victim computers.
In September, Kaspersky Lab’s anti-phishing component registered 18,779,357 detections. According to the statistics, 17.8% of all detections targeted the users in Brazil. Australia, which was August’s leader, moved down to 3rd position (11.1%). Global Internet Portals remained the leading category among the organizations most often attacked by phishers with 24.7% of all attacks. Financial phishing accounted for 36.9%of all detections made by Kaspersky Lab’s anti-phishing component, a 1.7 pp growth compared with the previous month. In September’s the Top 3 organizations most frequently targeted by phishers Facebook took the lead with (11.1%) of all detections.
In September, “Nigerian” scammers switched their attention from events in Ukraine to health issues, in particular to the Ebola virus which was rarely far from the headlines this month.
Promotional mailings offered goods and services dedicated to America’s Labor Day celebrations, as well as to the popular winter holidays celebrated worldwide. From now on we expect to see a sharp rise in the percentage of spam dedicated to Christmas and New Year festivities until it reaches its December peak.


































Spam in September 2014