
Spam in the spotlight
In March, spammers weren’t content to stick with traditional holiday-related advertising; they also used holiday-themed messages to con personal information from users of social networks.
March’s spam traffic included several distinctive groups of adverts – goods for car owners, offers of real estate in Crimea, language schools and services to improve office telephone communication. Many of these mailings were found in Russian and international segments of the Internet.
Holiday spam
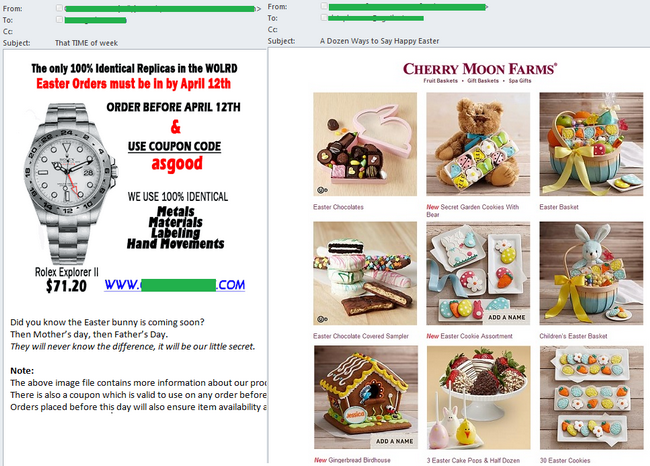
In 2014, Orthodox and Catholic Easter is celebrated on the same date – 20 April. In the run-up to the holiday English-language spam traffic distributed traditional festive adverts for fake designer goods and confectionary.
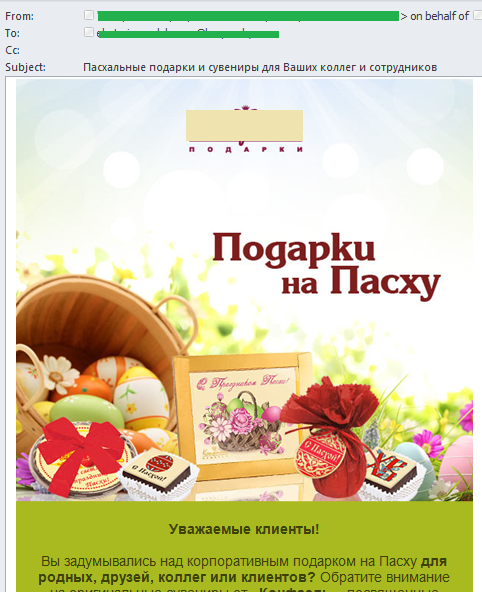
Russian-language spam also offered sweets and souvenirs with an Easter theme.
Noticeably, there wasn’t all that much Easter spam in March; we expect to see far more in April.
St. Patrick’s Day, celebrated on 17 March, was exploited by fraudsters to steal logins and passwords from LinkedIn personal accounts. A mass mailing dedicated to the holiday offered users a free premium account on the networking site. To enter the account the recipient had to click the link at the end of the email. However, the link led to a phishing page rather than to the official LinkedIn site and all information entered by the user was forwarded to the fraudsters. They used the logo of the social networking site and an autosignature to make the email look legitimate. Furthermore, the sender address also looked reliable except for the linke.com domain name used instead of the official linkedin.com.
Spamming in tongues
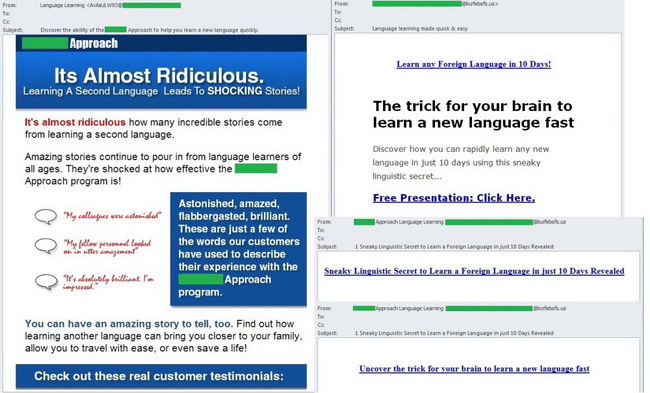
In March spam actively offered various methods of learning foreign languages. The recipients were invited to learn a foreign language in just 10 days. Instead of the the sender name such messages often contained the phrase “Language Learning” while the newly created email domains in the sender address varied from email to email. The messages contained long links which, after a series of redirects, led to an advertising site offering a discount for a set of DVDs for learning a foreign language using unique methods. When ordering, the recipient could pay using a convenient payment system.
Another mass mailing, this time sent out on behalf of translation agencies, also exploited linguistic themes. The emails appeared in different languages – English, German, French, Spanish and Dutch. Sometimes the text of the message was written in several languages. The emails contained a list of the working languages of the agency, the main language pairs for translation as well as a list of services (interpretation, translation, the most popular translation themes). Direct links to the agencies’ websites or contact phone numbers or managers’ email addresses were provided.
Spamming on the telephone
In March, spammers actively sent out adverts offering various ways to reduce telephone costs. Most of these mailings were sent to large companies. The recipients were offered ways of, for example, improving the quality of fixed office communication, connecting landlines to certain codes, or making unlimited international calls from any city at the lowest rates.
Mass mailings advertising these services arrived from addresses registered on the dedicated domains and varied from email to email. The links in the messages led to a site containing a mini-survey and after filling in the forms the user was invited to choose the most profitable solution. In the end, it all came back to advertising certain telephony services.
Statistics
Proportion of spam in email traffic
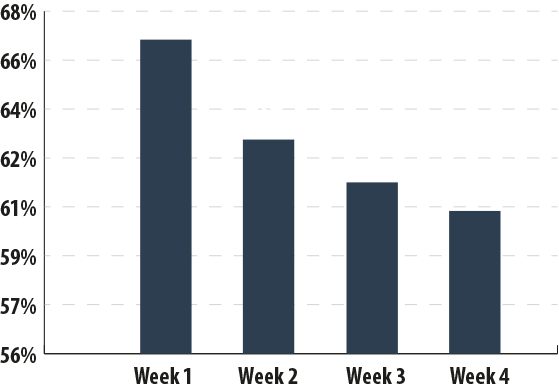
Proportion of spam in email traffic
The percentage of spam in email traffic averaged 63.5% in March. The highest levels of spam (67.3%) were recorded on the first week of the month followed by gradual decrease in spammer activity towards the end of the month.
Geographical distribution of spam sources
In March, the list of sources distributing spam worldwide looked like this:
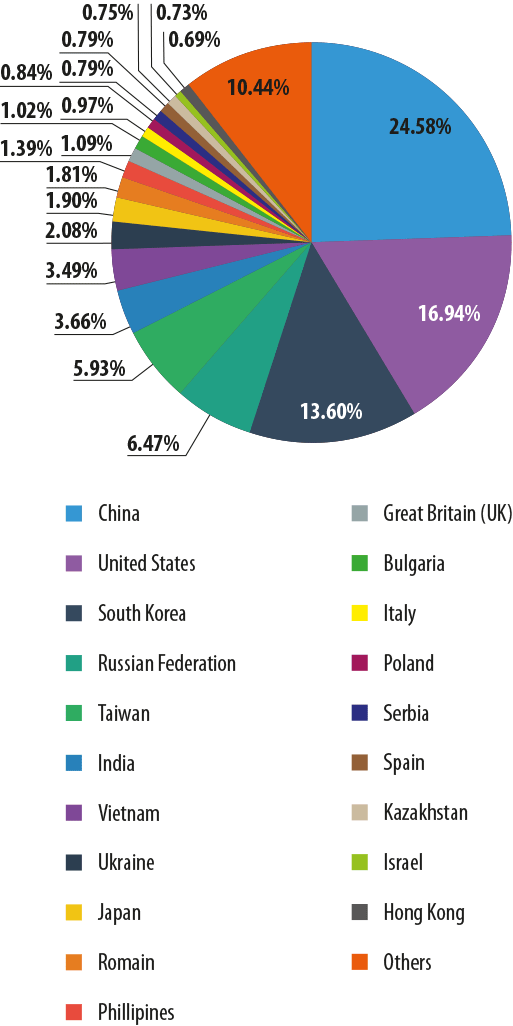
In March, China was the leading spam source with 24.6% of all distributed spam, an increase of 1.7 percentage points from the previous month. It was followed by the United States, whose contribution (17%) decreased by 2 percentage points in March. South Korea came third having spread 13.6% of the world’s spam, 0.8 pp more than in February. In March, these three countries accounted for over half of all spam sent worldwide.
Fourth position was taken by Russia (6.5%) which spread 0.5 pp less spam than in the previous month.
Next came Taiwan (6%), India (3.75), Vietnam (3.5%) and Ukraine (2%), all maintaining their postitions from February: their shares changed inconsiderably.
Japan (1.9%) climbed from tenth to ninth place although its contribution grew by only 0.15 pp. Romania (1.8%) completed March’s Top 10.
Also of note is a slight increase in spammer activity in the UK (1 pp) which pushed this country to twelfth place, eight places higher than February.
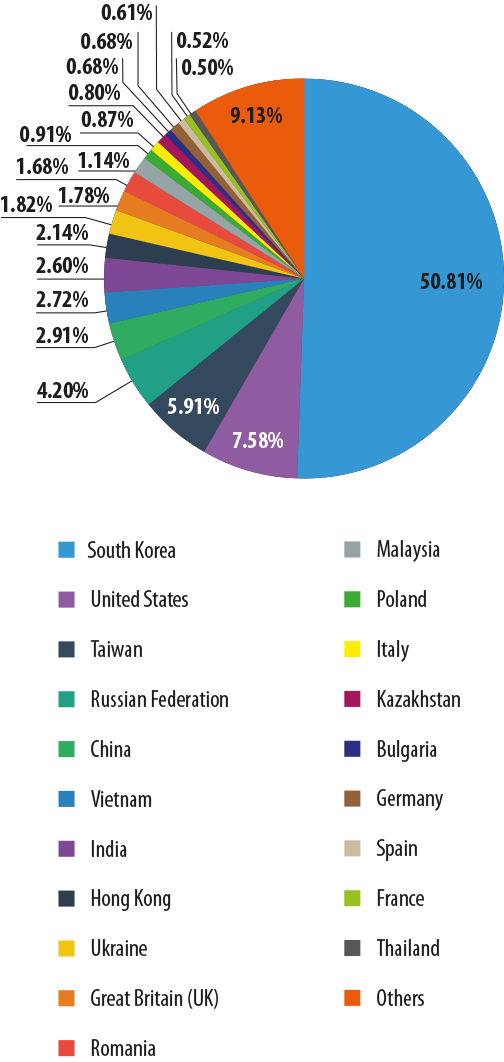
Sources of spam in Europe by country
South Korea remained the leading source of spam sent to European users (50.8%) in March: its share grew by 1.2 percentage points from the previous month. Next came the USA whose contribution decreased by 1.4 pp. Taiwan (6%) was in third place although its share grew 0.5 pp.
Russia (4.2%) remained fourth with a decrease of 0.8 pp from February.
March saw a drop in the amount of spam originating from China (2.9%), Ukaraine (1.8%) and Germany (0.7%) by 1, 0.5 and 0.7 pp respectively. At the same time there was a growth in the share of Vietnam (2.7%), India (2.6%) and the UK (1.8%) to complete March’s Top 10.
In March, France and Thailand increased their contribution by 0.5 pp each, moving these two countries into the rating of the most active distributors of spam sent to European users.
Asia remains the leading region (58%) for spam distribution – its share is 4 pp higher than the previous month. It is followed by North America (17%) and Eastern Europe (5%), whose share decreased by 2.6 and 1.4 pp respectively. The percentage of spam that originated from the other regions saw almost no change.
Malicious attachments in email traffic
In March, the Top 10 malicious programs distributed via email looked like this:
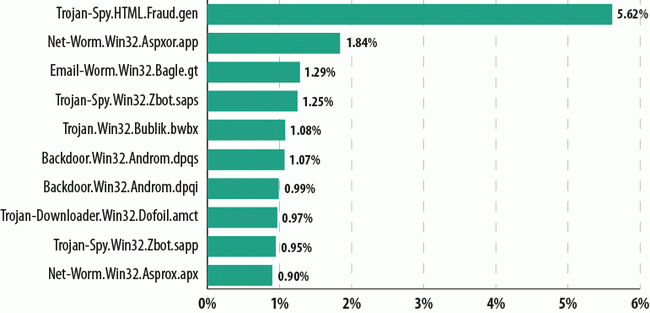
Top 10 malicious programs distributed via email
Trojan-Spy.HTML.Fraud.gen is still number one. As we wrote before, this piece of malware from the Fraud.gen family is a fake data entry HTML page that is sent to users by email, disguised as an important message from large commercial banks, online stores, software companies etc.
March’s second and tenth positions were taken by representatives of the Aspxor family. Aspxor is a spam-sending network worm. It can automatically infect websites, download and execute other software, and collect valuable data on the computer, such as saved passwords and credentials for email and FTP accounts.
Third came our old acquaintance Email-Worm.Win32.Bagle.gt, an email worm which sends copies of itself to all email addresses found on an infected computer. The worm also downloads files from the Internet without the user’s knowledge. Email-Worm.Win32.Bagle.gt uses its own SMTP library to send infected messages.
Trojan-Spy.Win32.Zbot.saps and Trojan-Spy.Win32.Zbot.sapp. were in fourth and ninth positions respectively. Zbot is a Trojan especially developed to steal confidential information. Zbot.saps, in addition to its main functionality, also installs Rootkit.Win32.Necurs (or Rootkit.Win64.Necurs) which, if installed successfully on an infected machine, interferes with the work of antivirus programs and other protection solutions.
The infamous Bublik malware family occupied fifth place in the ranking. Bublik is a Trojan downloader which downloads malicious files to user machines and then launches the files that are downloaded.
Backdoor.Win32.Androm.dpqs and Backdoor.Win32.Androm.dqpi came sixth and seventh respectively in March’s rating. The Andromeda family of malware consists of backdoors that allow cybercriminals to secretly control the compromised computer. The machines infected by these programs often become parts of botnets.
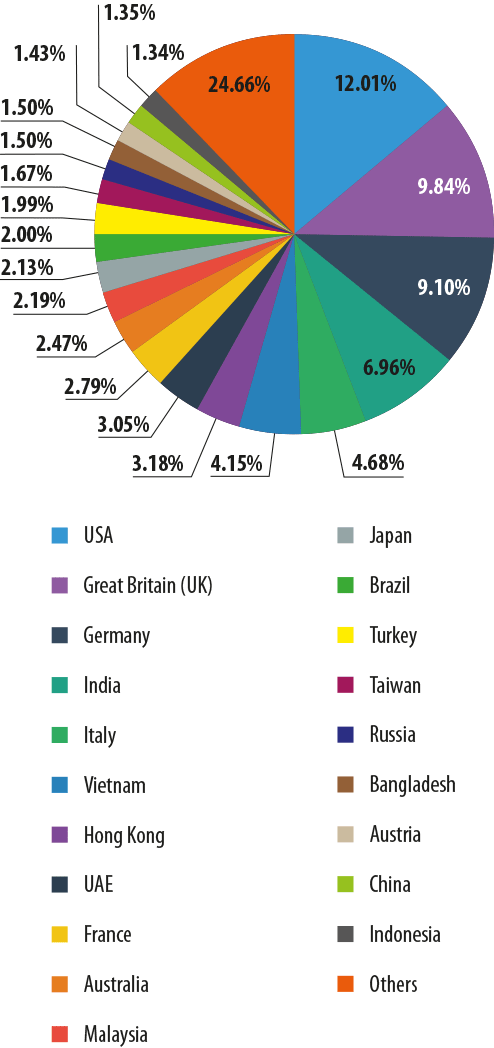
Distribution of mail antivirus detections by country
The USA (-1.2 pp) topped the rating of countries with the highest number of mail antivirus detections. The UK and Germany remained second and third.
Russia moved down from twelfth sixteenth place with a decrease of 0.82 pp in the number of mail antivirus detections. Australia also saw a significant drop (-0.75 pp), falling from seventh to tenth.
Special features of malicious spam
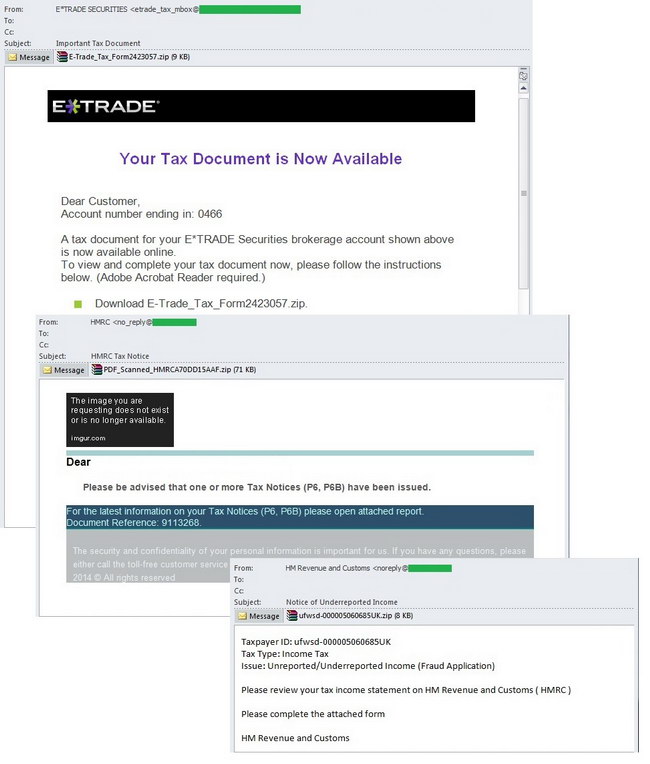
In March, lots of malicious attachments were sent on behalf of various well-known tax-related financial organizations. These messages imitated payment notifications from a tax authority, tax payment requests or notifications of the taxpayer’s undeclared income.
The emails often contained data such as the taxpayer’s ID, the type of taxation (in the example below it was income tax), a document reference number or a notification informing the recipient that his previously filed tax return was fake.
To get more details, the recipient was asked to open the attached report and sometimes to fill in an attached form with the document. In all cases, the necessary documents were supposedly included in an attached archive that actually contained an executable malicious file.
For example, these archives carried the Trojans detected by Kaspersky Lab as Trojan-PSW.Win32.Fareit.aoee and Trojan.Win32.Bublik.buya. Representatives of the first malicious family steal browser cookies and passwords from FTP clients and email programs and then send the data to a remote server run by the fraudsters. The second malware family downloads malicious files onto user computers and runs them.
Phishing
Social networking sites were once again the organizations most frequently used in phishing attacks even though their share dropped by 3.8 percentage points from the previous month to 23.5%. Next came email services (16.6%). Search engines (14.4%) and financial and e-pay organizations dropped by 2 and 3.5 pp respectively, resulting in search engines leapfrogging financial services into third place. The proportion of phishing attacks on online stores grew by 8.9 pp, lifting this category two positions up to fifth. The share of the telephony and internet service providers rose insignificantly as this category dropped to sixth.
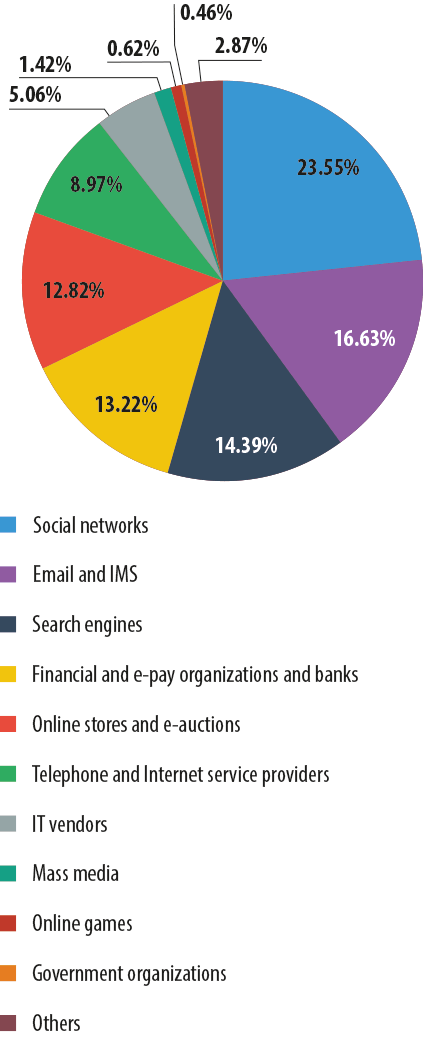
Distribution of the Top 100 organizations targeted by phishers, by category
The ranking is based on Kaspersky Lab’s anti-phishing component detections that are triggered every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
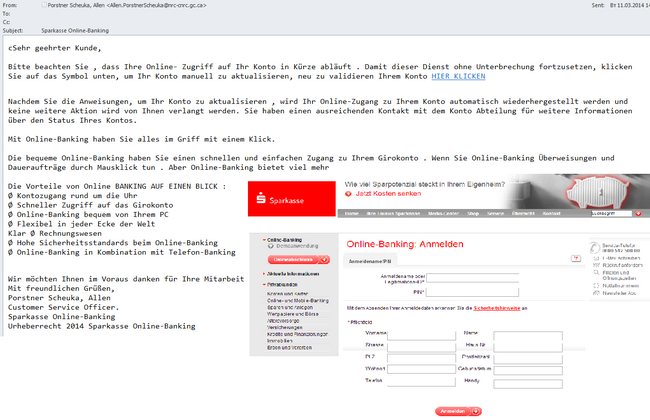
German banks are becoming frequent targets for phishers. In March we registered yet another fraudulent mass mailing aimed at stealing personal information from Internet banking users. An email sent on behalf of a bank employee informed recipients that access to online accounts would soon expire. To continue using online banking services users were invited to follow a link which in fact led to a phishing page where users were asked to enter not only logins and passwords from their online bank accounts but their personal information as well.
The fake page imitated the official website of the bank, but the phishing email itself did not contain any design elements (the bank logo, the auto signature, etc.) commonly used by fraudsters to make their emails look legitimate. Noticeably, the domain name of the server specified after the @ symbol in the sender address was owned by the National Research Council of Canada, which has nothing to do with the banking organization.
Conclusion
The percentage of spam in global email traffic in March decreased by 6.4 pp and averaged 63.5%. The total amount of holiday-themed spam also declined from the previous month. While the upcoming Easter holidays were exploited to advertise various products and festive gifts, St. Patrick’s Day was used by the fraudsters to get access to accounts on popular social networking sites.
In addition, spam traffic was flooded with huge amounts of adverts for language schools offering all types of teaching approaches. Many mailings contained information on how to optimize communication in large and medium-sized companies.
In March, the list of sources distributing spam worldwide looked like this: China (24.6%), the U.S. (17%), South Korea (13.6%). Asia remains the leader (58%) in spam distribution.
To send messages containing malicious attachments, the attackers resorted to fake notifications sent not only by reputable banks but by the other financial organizations involved in, for example, charging and collecting taxes.
In March, social networking sites were again the most popular service for phishers to imitate. Next came email services followed by search engines. The percentage of phishing attacks on online stores grew significantly allowing this category to climb two positions up to fifth place.






















Spam report: March 2014