
- June in figures
- Spam in the spotlight
- Spammer methods and tricks
- The geographical distribution of spam sources
- Malicious attachments in email
- Phishing
- Conclusion
June in figures
- The percentage of spam in email traffic in June was up 1.4 percentage points and averaged 71.1%
- The percentage of phishing emails rose slightly compared with May, and averaged 0.0032%
- Malicious attachments were found in 1.8% of all emails, a drop of 1 percentage point compared to the previous month
Spam in the spotlight
In June, spammers were actively distributing adverts of goods and services which are especially popular in summer. For example, as schools and universities swung into exam season, much of June’s spam featured mass mailings promising ready-made diplomas and school leaving certificates, as well as educational certificates. In June, holiday-related spam exploited the Father’s Day theme.
Celebrity master classes
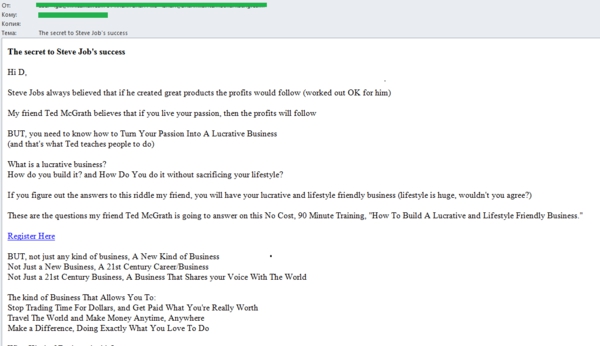
It’s already old news that scammers exploit the names of famous people to attract attention to spam mailings. This started way back, with the so-called “Nigerian letters”. However in June, we registered several mass mailings which authors used the names of celebrities a bit differently -advertising educational training and master classes.
Specifically, the spammers used the name of Steve Jobs, Apple’s founder. The heading of the unsolicited email invited the recipient to get to know the secret of the famous businessman’s success, however the body of message contained the advert of the free training. Its organizers promised in just 1.5 hours to teach everybody how to make a profitable business out of a hobby. Steve Jobs was used to attract attention to the training.
iPhone in spam
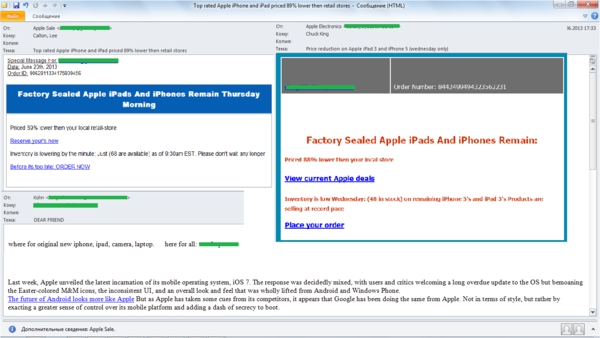
The worldwide popularity of smartphones and Apple tablets has caused the appearance of the vast number of companies specializing in selling Apple accessories and suspiciously cheap official devices. For them, spam has become an acceptable means of advertising their goods. In June, we discovered several mass mailings exploiting this theme.
In June, we often met spam messages offering huge discounts on Apple devices. To make the mailing look more legitimate, the scammers entered the name of the company in the From field, though the email address has nothing to with Apple. The authors of these emails stressed that there was a limited quantity of goods and it was essential to snap them up right away. This widespread trick was used to encourage the user to take a decision quicker and thus to click the link and order the goods.
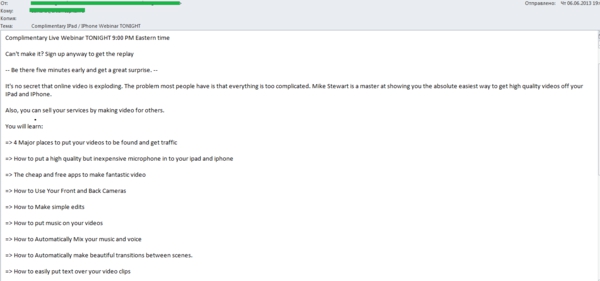
Spammers didn’t only offer Apple devices but also related training sessions. In June, we registered a mass mailing advertising a webinar about the creation of video on iPad and iPhone. The authors promised recipients that the webinar would teach them to create original, high-quality video which could help to earn extra money.
Spammers contribute to affordable education
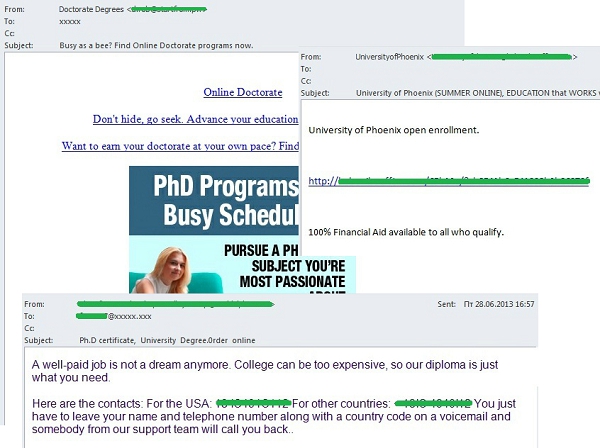
Summer is not only vacation time, it’s also the season for final school exams and university entrance exams. In June, we recorded a significant increase in spam mailings offering fake school leaving certificates and university diplomas for sale. Addresses for these mailings often came from public sources, different databases or were generated automatically by an electronic dictionary.
In June, we registered mass mailings containing offers of admission to US universities as well as offers of online education at the user’s convenience. These emails often included links to pages with application forms for the course. Interestingly, the addresses of the web pages vary from email to email and are often created on the day the mailing is sent. Probably this is how the authors of the mass mailing collect personal user data. We also saw messages selling degrees and diplomas for those who couldn’t – or didn’t want to – spend time studying.
Tutoring is another educational service commonly advertised in spam. Spammers’ clients may include both teachers and specialized agencies which offer qualified staff to help children improve their performance at school.
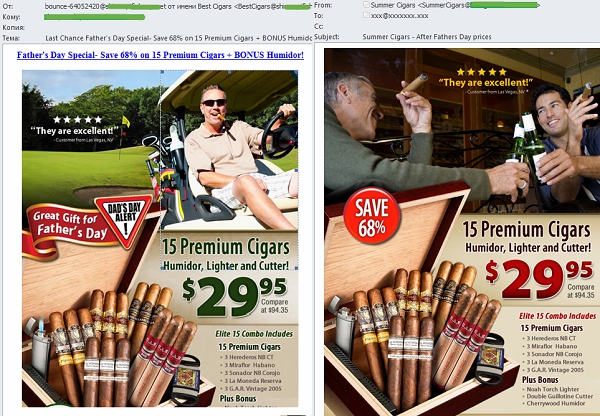
Cigars for the holiday
As expected, in June, spammers continued to spread adverts dedicated to Father’s Day, a holiday celebrated in the U.S. in mid-June. But after last year dad apparently dreamed of an expensive watch, in 2013 cigars were the gift of choice. There was little new here: the same patterns appeared in email traffic several months ago and has been seen again and again. Only the pictures and the text color changed; the general design remained almost the same.
Spammer methods and tricks
In June, spammers continued to use familiar tricks. In particular, we recorded several mass mailings advertising both conventional and electronic cigarettes where the organizers used the Google Translate service to process spam links. Moreover, the spammers added a randomly generated set of letters and names of Google domains in different languages to the end of links. For feedback the message contained an email address registered on a free mail service – spammers create such addresses by the dozen and keep changing them in their emails to bypass spam filtering.
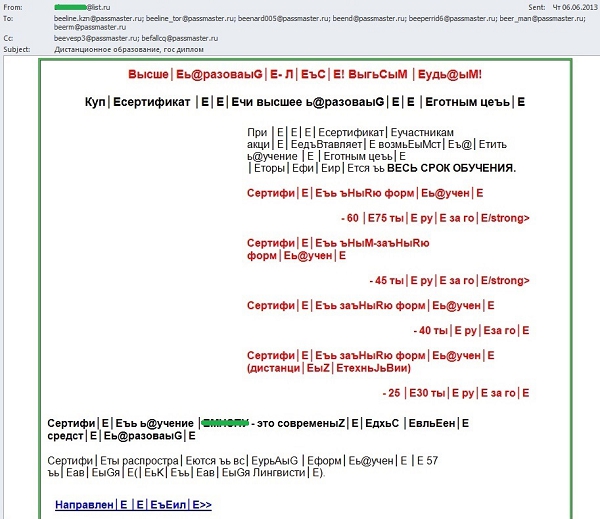
Spammers were also keen to use background noise to disrupt their texts. Typically, the authors of “educational” spam mailings used a random set of symbols to divide the phrases into parts, thus making them difficult to read. However key phrases such as the name of the training course, the university or the faculty, and the cost of the course and the contact details could easily be distinguished.
Spammers offering Apple products at bargain prices used yet another well-known trick. To obfuscate the content of the mass mailing and to evade spam filters they added some real news about Apple and a link to a news agency website to the email text.
Spammers advertising holidays in Russia and abroad in their mass mailings could simultaneously use the Cyrillic and Latin alphabets within a single word. The same technique was utilized by the authors of the property sale ads: the numbers in the text were replaced by the characters which looked similar to the figures, any spaces were deliberately ignored and additional characters were inserted.
The geographical distribution of spam sources
In June the Top 3 leading sources of worldwide spam remained unchanged. However the share of spam stemming from each country increased. China (23.9%) remained in 1st place, up 2 percentage points from May.
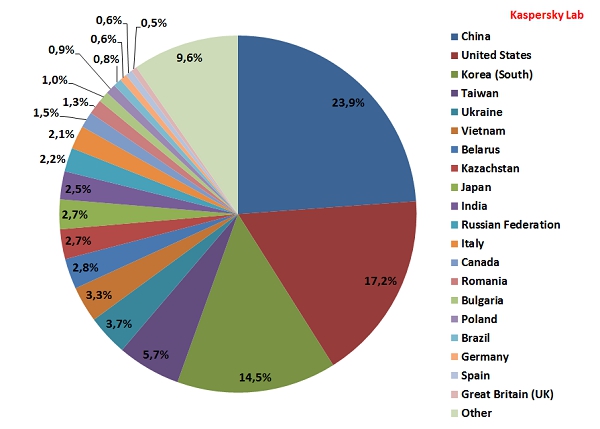
Sources of spam around the world by country
The amount of spam sent from the US was up 0.9 percentage points (17.2%) compared with the previous month leaving this country 2nd in the rating. South Korea was 3rd after a small increase took its contribution to 14.5% in June.
Taiwan remained in 4th place (5.8%) with almost no change from May. Meanwhile Vietnam (3.3%) dropped one place to 6th as its share fell by 1.7 percentage points.
In June, Belarus (2.8%) and Kazakhstan (2.7%) were in 7th and 8th places with spam flows declining by 0.6 and 1.6 percentage points respectively.
Russia’s contribution (2.1%) fell by 0.1 percentage points which saw it in 11th place in the rating. It is followed by Italy (2.1%) which gained 1 percentage point from the previous month.
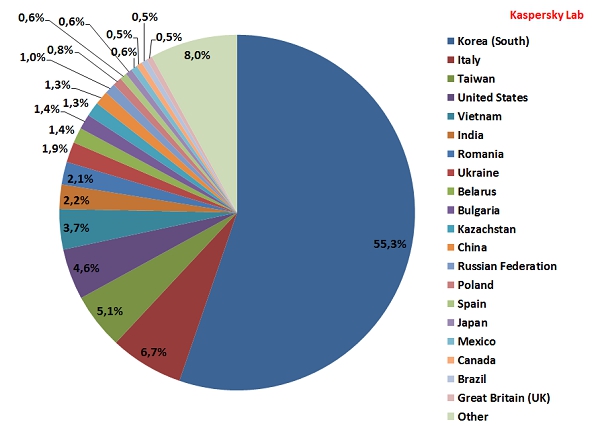
Sources of spam in Europe, by country
In June, South Korea remained the leading source of spam sent to European users (53.3%): its share grew by 9.6 percentage points. The US (4.6%) and Vietnam (3.7%) moved down to 4th and 5th positions yielding to Italy (6.7%) and Taiwan (5%) respectively. Italy’s figure grew by 3.9 percentage points compared with May when this country was only 7th in the rating. India jumped from 12th to 6th place, sending 2.2% of all spam received in Europe.
Ukraine (1.9%), China (1.3%) and Japan (0.6%) fell several places and in June’s rating they came 8th, 12th and 16th respectively. The share of spam originating from Russia decreased by 1.1 percentage points and averaged 1% moving this country down from 10th to 13th place. Britain’s contribution (0.5%) to spam flows also grew smaller, pushing it down to 20th, 6 spots lower than in May.
Asia (57.3%) remained the leading source of spam by region: its share increased by 1.2 percentage points from May. As in the previous month, the Top 3 also included North America (18.7%) and Eastern Europe (13.2%). It should be noted, though, that North America’s figure grew by 0.6 percentage points while Eastern Europe produced 1.4 percentage points less spam than in May
Malicious attachments in email
In June, malicious attachments were detected in 1.8% of emails, a decrease of 1 percentage point from May.
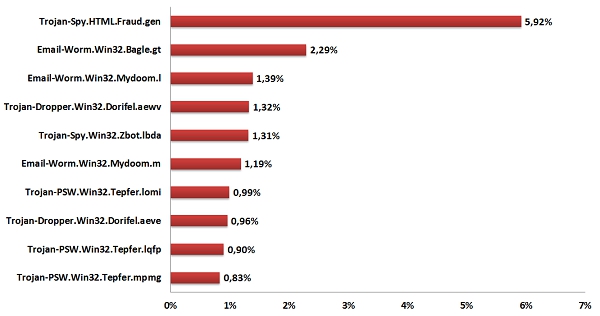
TOP 10 malicious programs spread via email in June 2013
In June, Trojan-Spy.html.Fraud.gen remained the most widespread malicious program. This malicious program appears in the form of HTML pages which imitate the registration forms of well-known banks or e-pay systems and are used by phishers to steal user credentials for online banking systems.
Email-Worm.Win32.Bagle.gt. came 2nd. This mail worm’s functionality is to self-proliferate to addresses in the victim’s address book, which is typical for this type of malware. It can also contact a command center and download other malicious programs onto a user’s computer.
In third place is Email-Worm.Win32.Mydoom.I. Like all worms, its main functionality is to harvest email addresses from infected computers and send itself to these addresses in the form of an attachment (files with .doc, .htm, .html and .txt extensions). In this case the sender’s address imitates one of the addresses found on the computer.
Mydoom.m is yet another representative of the Mydoom family, and it took 6th position in June. In addition to self-proliferation it sends hidden search requests to search engines as such as Google, Yahoo, Altavista and Lycos. The worm compares the addresses of the sites displayed on the first page of the search results with the addresses which it has downloaded from the fraudsters’ servers. Having found the match, it opens the link on the search engine page thus increasing the site traffic and sites’ ratings in search results.
Trojan-Dropper.Win32.Dorifel.aewv was in 4th position. Its main functionality is to fulfill commands from a remote server as well as downloading and running other malicious programs.
A representative of the ZeuS/Zbot family Trojan-Spy.Win32.Zbot.Ibda completed the Top 5. This Trojan was designed to steal users’ confidential information including their credit card credentials. In June, we registered over 1,300 ZeuS/Zbot modifications with a combined total of about 7% of all malicious programs spread via email.
The Top 10 also included the Tepfer family spyware which has been quite popular this year.
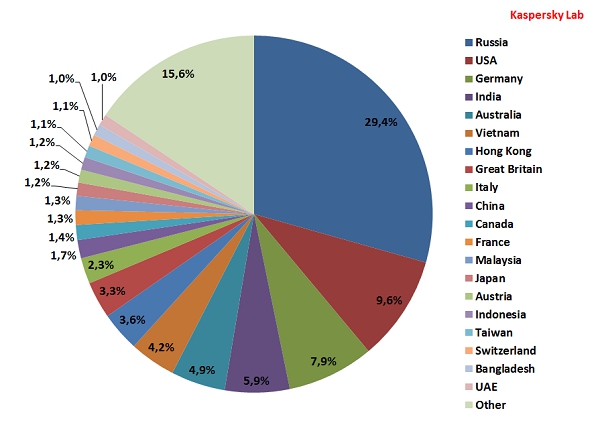
Distribution of email antivirus detections by country
In June, Russia was the country most heavily targeted by malicious emails. It saw a 13-fold increase in its share of the malicious market, rising to 29.4% from May’s 2.2% tally. Such striking growth came from an increase in the number of emails infected with email worms, particularly Net-Worm.Win32.Kido.ih, Worm.Win32.AutoRun.dtbv and IM-Worm.Win32.Sohanad.bm.
Russia’s rise pushed the US into 2nd position with 9.6% of all antivirus detections, a decrease of 4.7 percentage points. Germany came 3rd (7.9%): its contribution falling by 1.6 percentage points. It was followed by India (5.9%) and Australia (4.9%) which occupied 4th and 5th places respectively.
The number of antivirus detections in the UK declined by 2.7 percentage points and averaged 3.3% which placed this country on 8th position in the rating. Italy (2.4%) came 9th with a drop of 2.8 percentage points from May.
China (1.7%) replaced Canada in 10th position in June’s Top 10.
Special features of malicious spam
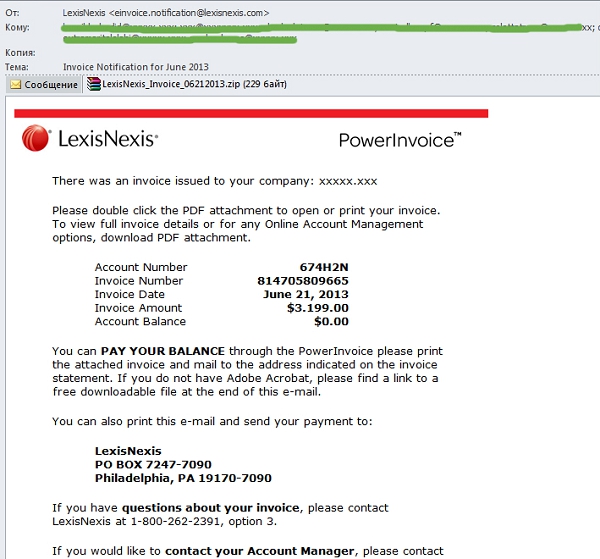
In June, we registered a big mass mailing which targeted the partners of LexisNexis, an American company. The mailing offered online access to different databases. The fake email, which arrived from the seemingly legitimate address einvoice.notification@lexisnexis.com, informed the recipient of an invoice for LexisNexis services. The message explained that more details of the invoice and the payment were available in the PDF archive attached. In fact, the LexisNexis_Invoice_06212013.zip archive contained a Tepfer Trojan program used by fraudsters to steal users’ passwords and logins.
The scammers worked hard to make the fake message look like an official notification: they used the LexisNexis logo and the company’s real contact information. However the senders were excessively persistent – urging readers to open the attachment at three separate points in the email – which would put a cautious recipient on guard.
Phishing
The percentage of phishing emails increased very slightly compared with May, reaching 0.0032%.
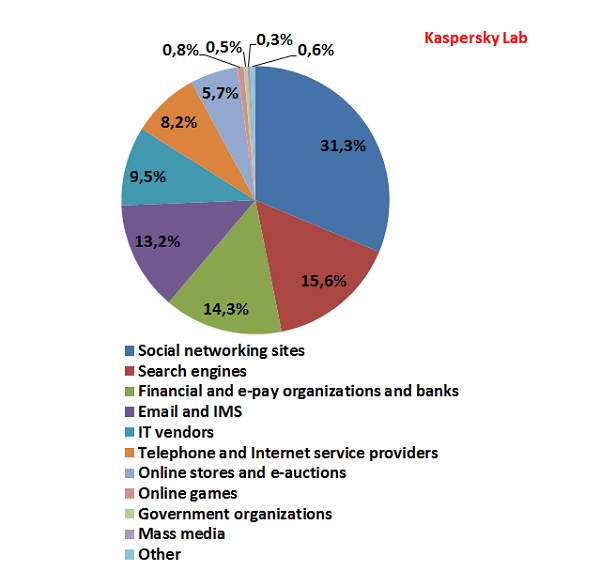
The distribution of the Top 100 organizations targeted by phishers, by category*
This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
Users of social networking sites continued to be the most attractive target for phishing attacks although their share fell 4.6 percentage points and averaged 31.3%.
In June, Search Engines (15.6%) and Financial and E-pay Services (14.3%) came 2nd and 3rd respectively. Their figures in May were almost equal. This month the share of Search Engines increased by 0.61 percentage points while the contribution of Financial and e-pay organizations dropped by the same amount.
The figure for Email and Instant Messaging Services increased threefold and accounted for 13.2%, pushing this category up to 4th position. IT vendors (9.5%) moved down to 5th place. Internet providers (8.2%) remained in 6th position in the rating. They were followed by Online Stores and Auctions (5.7%) which dropped two points from May and settled in 7th place.
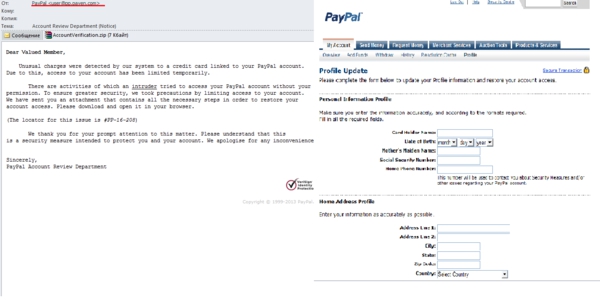
In June, we recorded several mass mailings which included fake notifications sent on behalf of the well-known e-payment system PayPal. One of these emails informed the recipient that the system had blocked access to the user’s account after registered suspicious credit card payments. To unblock the account the user was required to open the file contained in the attached archive AccountVerification.zip. This file named Verify Account.html opened in the browser and showed a fake page with the user’s updated PayPal profile. The plan was to encourage the user to enter credit card credentials, PayPal account data and other personal information – enough to give the fraudsters access to the victim’s PayPal account and credit card.
Conclusion
As expected, summer brought an increase in the volume of “educational” spam. Scammers also continued to exploit the names of famous people to advertise goods and services this month. The on-going excitement around Apple products was used to advertise accessories and discounts on popular electronic gadgets.
In June, more than half of the world’s spam was distributed from three countries – China, the US and South Korea. Noticeably, the contribution of each leader continued to grow. South Korea remained the main source of spam sent to European users. It was followed by Italy and Taiwan in 2nd and 3rd. The US and Vietnam moved down to 4th and 5th positions respectively.
Contrary to our forecasts the number of phishing attacks on social networking sites fell in June. However these sites remain the most attractive target for phishers. At the same time, the amount of attacks targeting Email and IMS increased drastically, because in the summer holidays the number of e-mail users and the users of such programs as ICQ, Jabber, Skype, etc grows. There is substantial demand for accounts of this type on the black market, which encourages phishers to try to grab login details for them.























Spam in June 2013