
Recently, we’ve seen SMS Trojans starting to appear in more and more countries. One prominent example is Trojan-SMS.AndroidOS.Stealer.a: this Trojan came top in Kaspersky Lab’s recent mobile malware ТОР 20. It can currently send short messages to premium-rate numbers in 14 countries around the world.
But this is not all. Another Trojan, Trojan-SMS.AndroidOS.FakeInst.ef, targets users in 66 countries, including the US. This is the first case we have found involving an active SMS Trojan in the United States.
FakeInst was detected by Kaspersky Lab back in February 2013; since then, 14 various versions of it have emerged. The earlier versions were only capable of sending messages to premium-rate numbers in Russia. But by mid-2013 other countries appeared on the “support list”:
| USA | Kazakhstan | Latvia | Czech Republic |
| Germany | Ukraine | Spain | Georgia |
| Lithuania | Belarus | Poland | France |
| France | Moldova | Estonia | Greece |
| Tajikistan | United Kingdom | Kyrgyzstan | Belgium |
| Finland | Malaysia | Israel | Mexico |
| Hong Kong | Sweden | Denmark | Serbia |
| Azerbaijan | Armenia | Chile | Bosnia |
| Nigeria | Hungary | Canada | Netherlands |
| Macedonia | Switzerland | Portugal | Slovakia |
| Norway | South Africa | Egypt | Brazil |
| Montenegro | Cambodia | Ireland | Vietnam |
| Luxembourg | Argentina | Peru | Slovenia |
| Morocco | Indonesia | Colombia | Italy |
| Ecuador | Bolivia | China | New Zealand |
| Albania | Venezuela |
According to our statistics, most Trojan-SMS.AndroidOS.FakeInst.ef infections were in Russia and Canada.
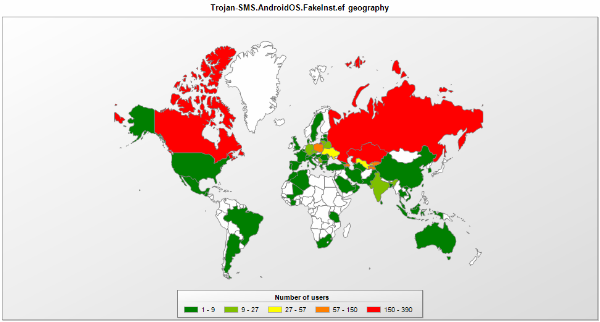
The geographical distribution of Trojan-SMS.AndroidOS.FakeInst.ef infections
FakeInst disguises itself as an application for watching porn videos.
The application asks the user to agree to send a text message to purchase paid content. However, after sending the message the Trojan opens a free-access website.
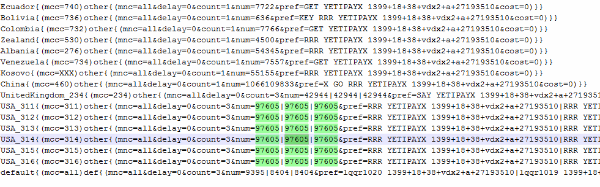
In order to send the message, the Trojan decrypts a configuration file which contains all phone numbers and prefixes:
From this list, FakeInst selects the appropriate numbers and prefixes for the user’s mobile country code (MCC).
For instance, for an MCC within the range 311-316 (which corresponds to the USA), the Trojan would send three messages to the number 97605, each costing about $2.
The Trojan also contacts its C&C server for further instructions. Of all the commands that it can receive and process, we’d like to highlight the ability to send a message with specific content to a number listed in the C&C command, and intercept incoming messages. The Trojan can do various things with incoming messages – steal all of them, delete them, or even respond to them.
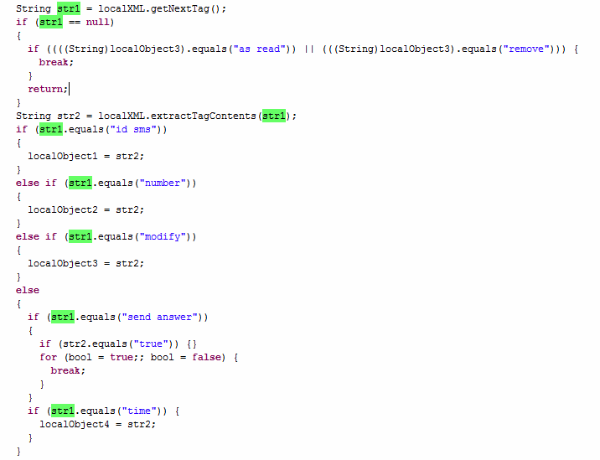
Processing C&C commands to intercept SMS messages
We believe that FakeInst was created by Russian-speaking cybercriminals. Firstly, its early versions were only designed to operate in Russia. Secondly, all its C&C servers are registered with and hosted at Russian providers. Virtually all versions of the Trojan use the following two C&C servers:
x-bt.in
y-bt.in
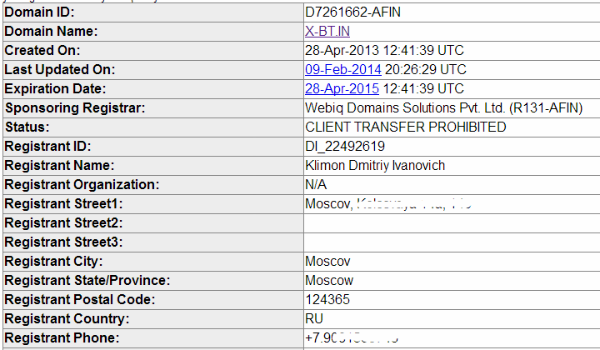
These URLs were registered in the name of Klimon Dmitriy Ivanovich, who gave Moscow as his place of residence and a Russian phone number.
These domains use the DNS servers of the FASTVPS.RU company.
The following sites are located on the same IP with these C&C servers:
botmgr.net
anid.in
icemob.net
ftop.org
midex.org
wapon.org
Judging by their responses and their structures, these sites are also used to manage bots. They are also registered with the personal data shown above.

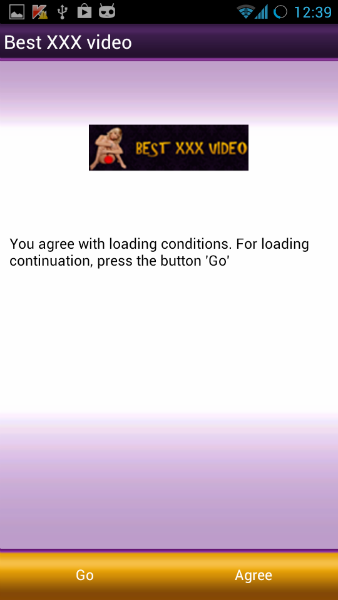





















An SMS Trojan with Global Ambitions