
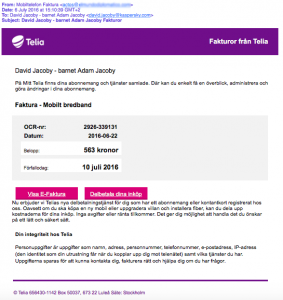
Whilst sitting and working in the South African office I receive an email from my Swedish ISP. I quickly look at it and there is something that doesn’t add up. The email states that I need to pay my invoice, but I never receive electronic invoices from this company.
Like everyone else I receive a lot of spam and phishing emails, but this one is different from any other phishing email I have ever seen before. To be honest, it’s probably the most sophisticated phishing campaign that I’ve ever encountered. It’s not the technical setup that makes it sophisticated it is a very simple factor that has been added to the email that just makes the email look very authentic.
The phishing campaign has the usual mistakes, the sender of the email is not related to the company, and the domains used in the links don’t point to a domain that is registered by the ISP.
There has been a huge increase in these kind of phishing emails lately but it’s the first time I have seen these emails. What makes this campaign so interesting is that they have not just addressed the email to me, but also included my child’s name. This is something I have never seen before. How they got access to my child´s name is not sure, one speculation is that they compromised a Swedish governmental agency, but this has to be left unconfirmed.
What happens when you click on the link is it will redirect you to a website. This website will enumerate from your country of residence to make sure that you are actually a Swedish victim. Additional to this, it will enumerate your browser by analysing the User-Agent string.
Why they check the Operating System is because the next step in the campaign is to trick you into downloading a Windows executable. We are currently investigating what the malware is doing, but from our previous research it seems that it’s some kind of Cryptolocker.
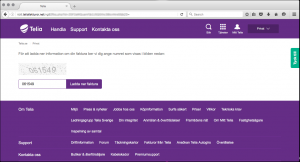
The download page looks very authentic, it even uses the domain teliafakturor.net (translated to teliainvoices.net), with a little captcha. When you click on the download button you will be offered a ZIP-file.
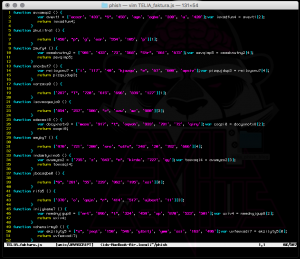
This archive contains an obfuscated JavaScript which will then download the actual Windows executable. Even though the JavaScript is obfuscated the download URL is not, so it’s very easy for any researcher to get hold of the malware, and block it. Below is a script of the obfuscated JavaScript.
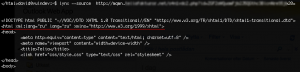
When analysing the landing pages and the source code i found something that was quite interesting. The language of the HTML editor that was used is Russian, and some of the domains are registered to an email address, which has registered other domains in Russia. This might be an indicator that the persons behind this scam has Russian origin.
An increase of sophisticated phishing attacks in Sweden




















Nick Griffin
This is TorrentLocker (aka Crypt0L0cker). They’ve targeted the Nordics in the past with things like PostNord themes.