
Today I got a ‘Anti-virus notification message’ from our mail server (protected by kav4lms) so naturally I was interested in what the content was. Examining the quarantined mail on the server revealed some interesting details starting from the mail header itself:
“X-PHP-Script: .com/templates/beez/woolf2.php for 41.248.
The message had come from a compromised host and a php mailer was used
directly from there to send phishing mails.
A quick trip to the location mentioned in the header showed a mass mailer GUI containing a link to a spammer site which is currently offline. But a little digging around showed the site had been hosting ‘phish kits’ – collections of malicious files which can be downloaded ‘for free’.
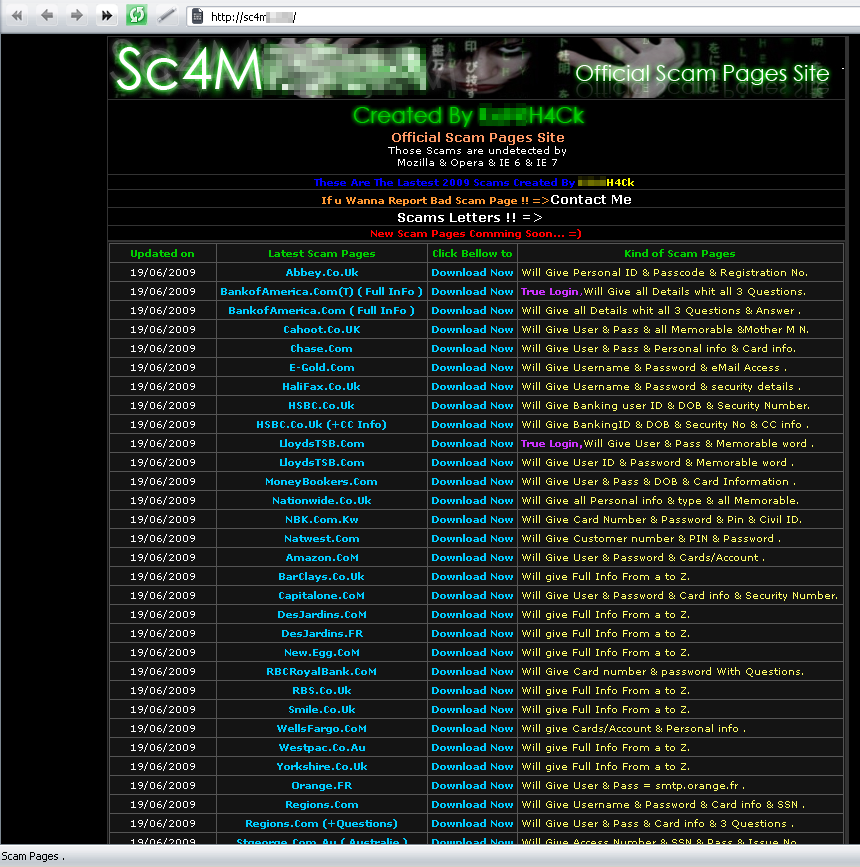
These ‘phish kits’ are archives which just need to be extracted to a compromised server. All a cybercriminal needs to do (apart from finding a compromised server) is edit one of the files in that package and input a mail address where harvested information should be sent to. The twist is – not only does the information get sent to the designated email address, but to another cybercriminal as well.
This scam is nothing new, but less experienced bad guys might not realize that they’re sharing their ill-gotten gains with other, more technically savvy, blackhats.




















All your phish are belong to me