
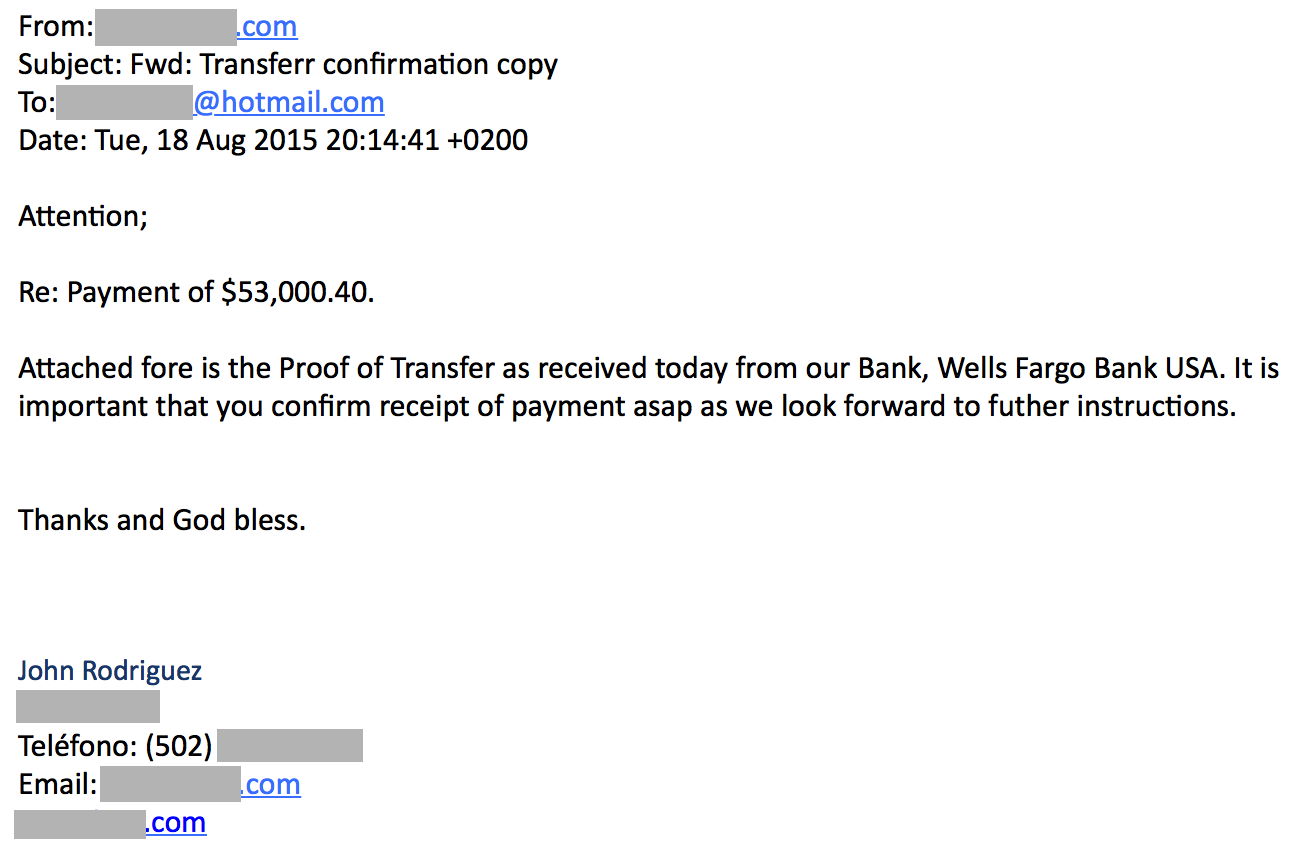
Today I ran into a typical fraud email claiming to come from a U.S. bank but with a twist! Analyzing the attachment, it turns out that there’s no malware inside but instead a new middle step to fool lesser security software.
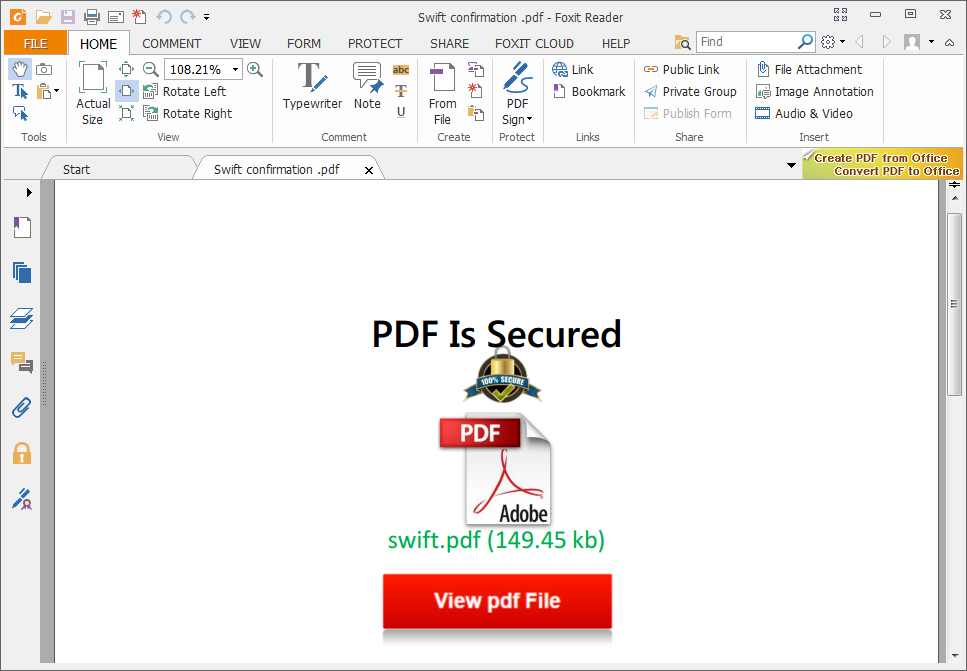
The original file name is “Swift confirmation .pdf” and it was created using Microsoft Word 2010.
So, if it is not malware then what’s the catch?
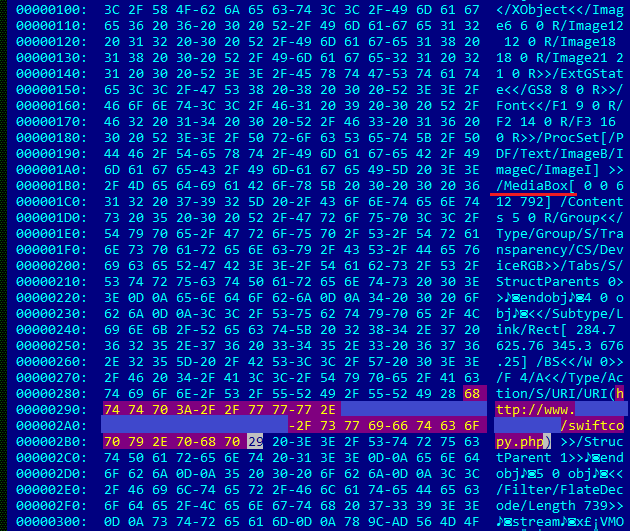
Well, this is a ‘Mediabox’-clickable document file used to redirect victims to a phishing website.
If the victim clicks on ‘View pdf File’ then it first opens a redirector website and then finally makes the jump to a server located in Chile that actually hosts the phishing attempt.
This is an interesting technique that would fool some Anti-Phishing filters based on analysis of the URLs in the embedded email messages themselves.






















A Phishing Trampoline – embedding redirects in PDF documents