
On 14 January, my colleague Vyacheslav Zakorzhevsky published a blog on the dangers of using cracks and keygens.
The malware in question was primarily for stealing registration keys for popular software.
A few days ago, we found a new malicious application that disguises itself as a Kaspersky Trial Resetter (an application that can be used to reset a software evaluation period that has expired).
The new malware is detected as Trojan-PSW.MSIL.Agent.wx and only two vendors, including Kaspersky Lab, currently detect it.
The twist here is that instead of re-setting your trial period, it steals information saved on the computer, be it browser-saved passwords, or passwords saved by an application.
According to the PE header, the malicious software was created on 31 January 2011, although the first infection reports appeared on 6 February. One can only wonder how successful such an application can be? Read below to find out:

In 23 days, a total number of 1109 computers were infected with this password-stealing Trojan, with an average of 48 infections per day.
The top 5 targeted countries were:
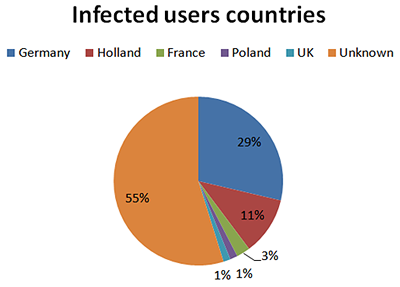
What about the type of stolen accounts?
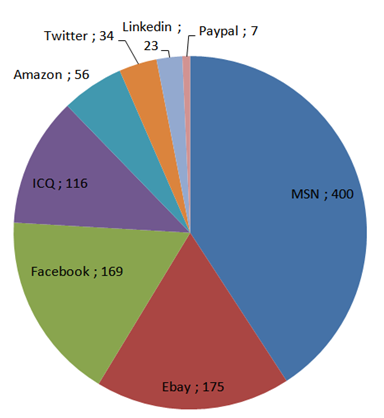
Among the stolen data, hundreds of website credentials were found, such as data for: web hosting, online stores, internet/mobile provider, social networks (LinkedIn, Twitter, Facebook, MySpace etc.), webmail, blogs, banking, instant messaging, online gaming etc.
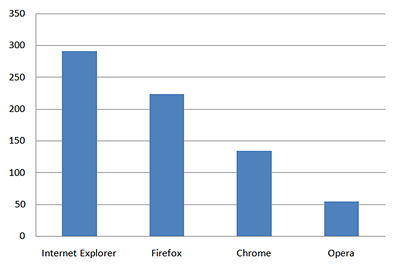
Here is a list of the browsers targeted by the malicious program, as well as the number of users whose data were stolen:
Kaspersky Lab contacted the hosting provider of the drop zone who closed and deleted the accounts.
I hope these statistics will convince you that downloading pirated software is not a good idea.
1109 users who thought they were downloading a crack for a security solution ended up being infected.
It’s also clear that saving your passwords within your browser isn’t the best idea.
You may want to consider using a Password Management program, such as the Kaspersky Password Manager, which keeps all your passwords encrypted and immune to these sorts of attacks.
We are currently in the process of contacting the victims and informing them about the infection.





















A Keygen with a Twist 2