
There are only two weeks to go before the start of the massive soccer event — FIFA World Cup. This championship has already attracted the attention of millions worldwide, including a fair few cybercriminals. Long before kick-off, email accounts began bulging with soccer-related spam, and scammers started exploiting the topic in mailings and creating World Cup-themed phishing pages.
Our statistics show spikes in the number of phishing pages during match ticket sales. Every time tickets went on sale, fraudsters mailed out spam and activated clones of official FIFA pages and sites offering fake giveaways allegedly from partner companies. But as the event draws nearer, cyber scams are reaching fever pitch. We present our observations below.
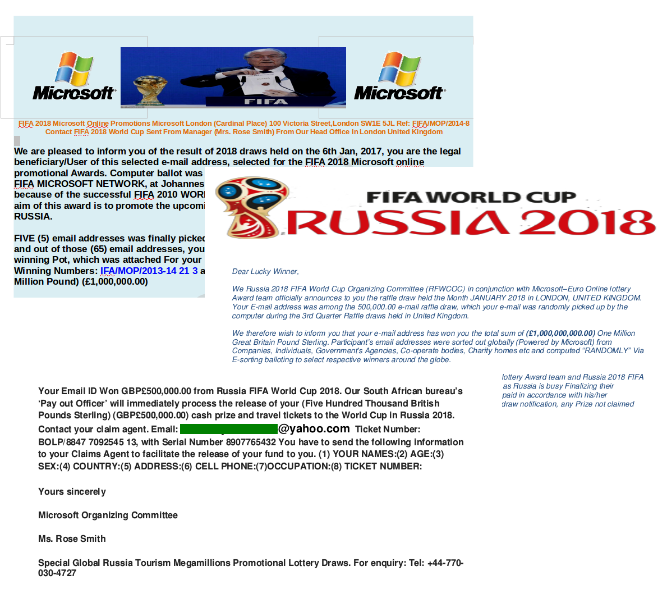
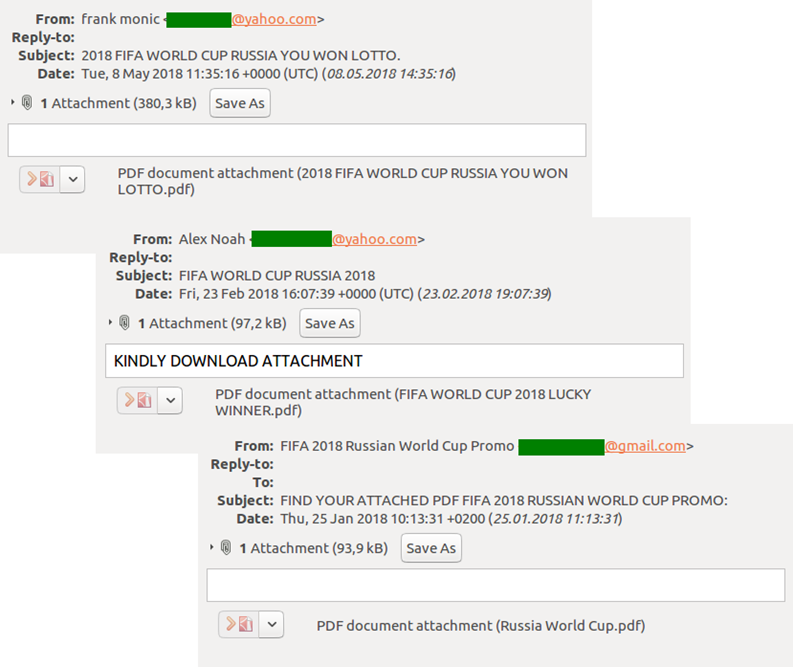
Fake lottery win notifications
One of the main types of World Cup-related email fraud is spam informing recipients of cash winnings in lotteries supposedly held by official partners and sponsors (Visa, Coca-Cola, Microsoft, etc.), as well as FIFA itself.
Such messages contain attachments (usually PDF or DOCX documents) in which the “winner” is congratulated and told to forward detailed contact details (name, date of birth, address, email, telephone no.) in order to receive the prize. Sometimes recipients are asked to pay a part of the postage or bank transfer fees.
Such mailouts are aimed primarily at harvesting user data (including financial), plus picking up a small money transfer. Such messages can also contain malicious attachments, for example, Trojan-Banker programs.
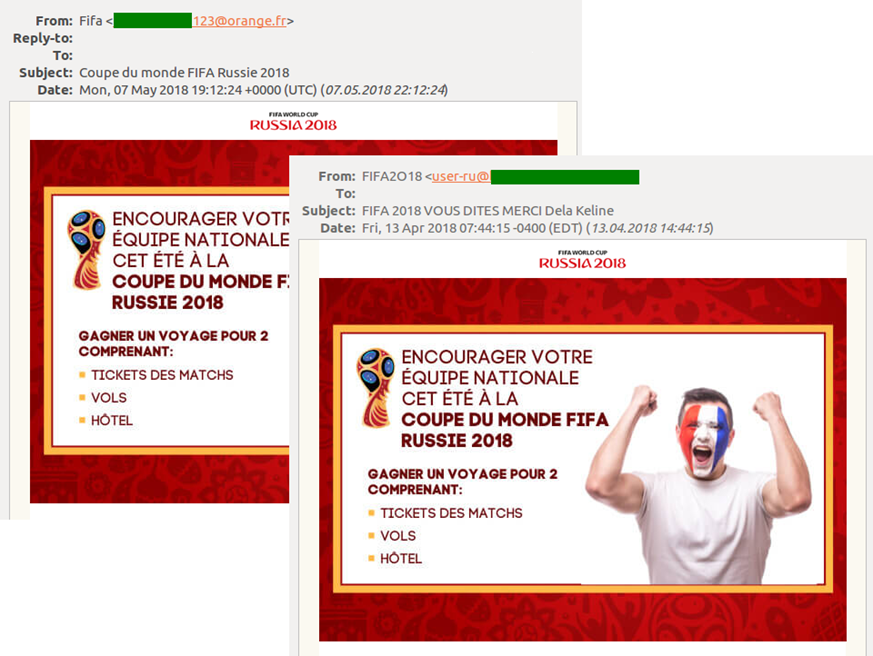
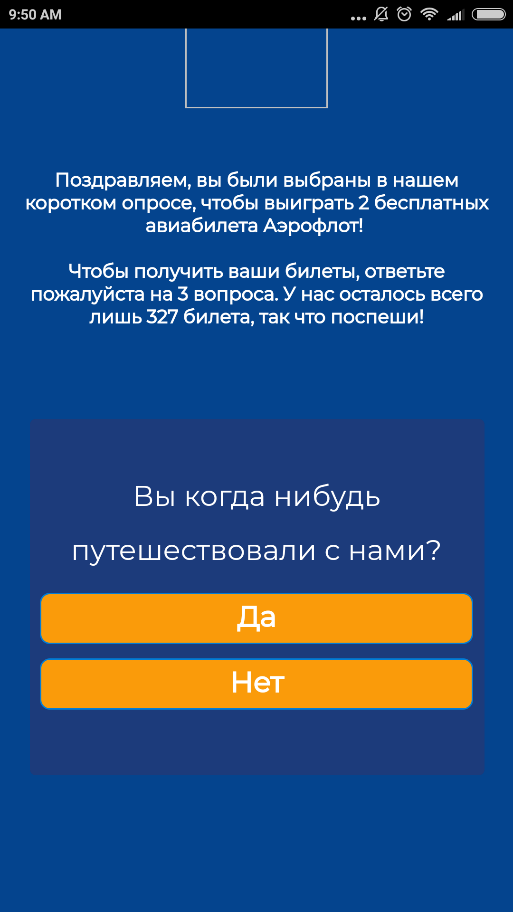
Another type of common spam fraud is an offer to take part in a ticket giveaway or win a trip to a match. Victims are required either to register on a fake promotion page and provide an email address, or, as in the case of lottery emails, to send the “organizers” their contact details. Such messages are sent in the name of FIFA, usually from addresses on recently registered domains. The purpose of such schemes is mainly to update email databases so as to distribute yet more spam.
Advertising spam
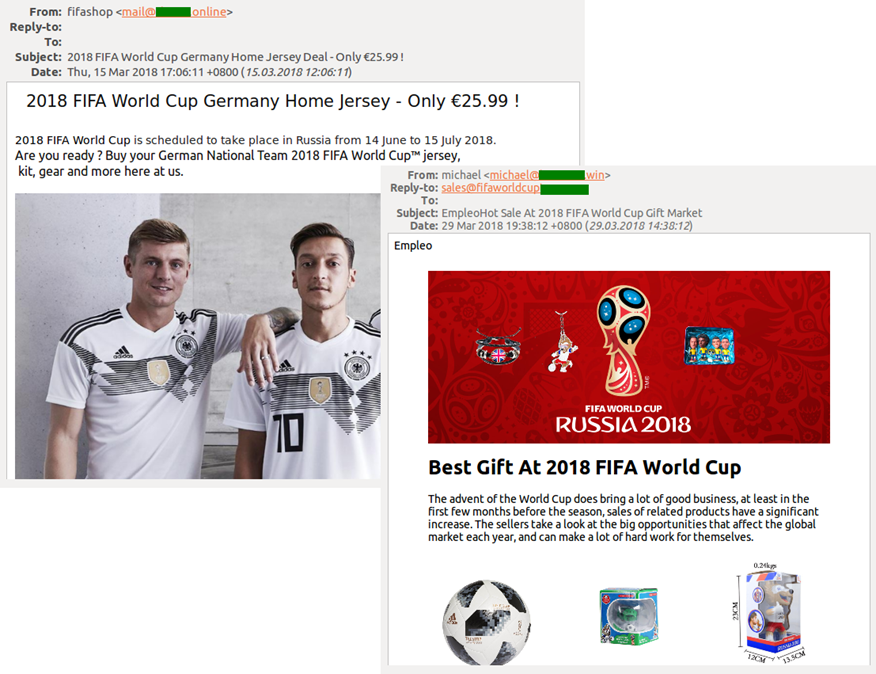
In the runup to the championship, we registered a lot of advertising spam with offers for soccer merchandise, transport/accommodation services, and travel packages from various tour operators. Merchandise was generally offered by small online retailers and included toys, souvenirs, and stationery marked with official logos, as well as soccer jerseys for all teams taking part. Some messages even resemble mailings from the official FIFA store.
There were also spammings unrelated to soccer. For example, traditional spam offering medical products, but using the World Cup to attract attention. Interestingly, the message subject referred to the 2006 World Cup final. Perhaps the spammers used an old template and forgot to change the date.
Ticket sales
Besides online stores selling merchandise, there are plenty of sites offering match tickets, both fake and real. But real doesn’t necessarily mean bona fide: they are often sold by ticket scalpers exploiting various loopholes in the FIFA rules.
However, official tickets can only be bought on the official FIFA website, and large fines are imposed for their illegal sale or resale. Those who use the services of speculators risk being turned away at the stadium: tickets are personalized, and if the bearer fails to show ID matching the information in the ticket, FIFA staff have the right to refuse entry.
Fake sites and messages from partners
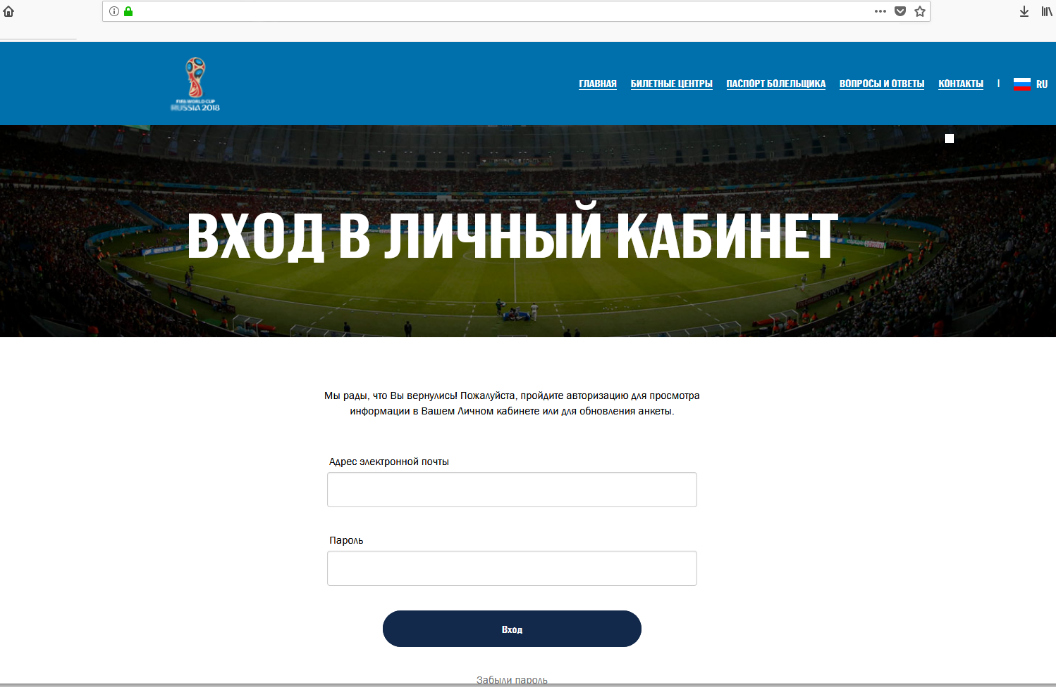
One of the most popular ways to steal credentials for bank and other accounts is to create counterfeit imitations of official partner websites. Partner organizations quite often arrange ticket giveaways for clients, and this is what attackers exploit to lure users onto fake promotion sites. Such pages look very convincing: well-designed with a working interface, hard to tell from the real thing.
Scammers also try to extract data by mimicking official FIFA notifications. The victim is informed that the security system has been updated and all personal data must be re-entered to avoid lockout. The link in the message takes the victim far away from FIFA to a fake personal account. Naturally, all data entered flows straight to the scammers.
Cybercriminals are particularly keen to target clients of Visa, the tournament’s commercial sponsor, and offer prize giveaways in the name of this international payment heavyweight. To take part, users need to follow a link that unsurprisingly points to a phishing site (the domain was registered a couple of months ago and has nothing to do with the payment system), where they are asked to enter their bank card details, including the CVV/CVC code.
Fraud allsorts
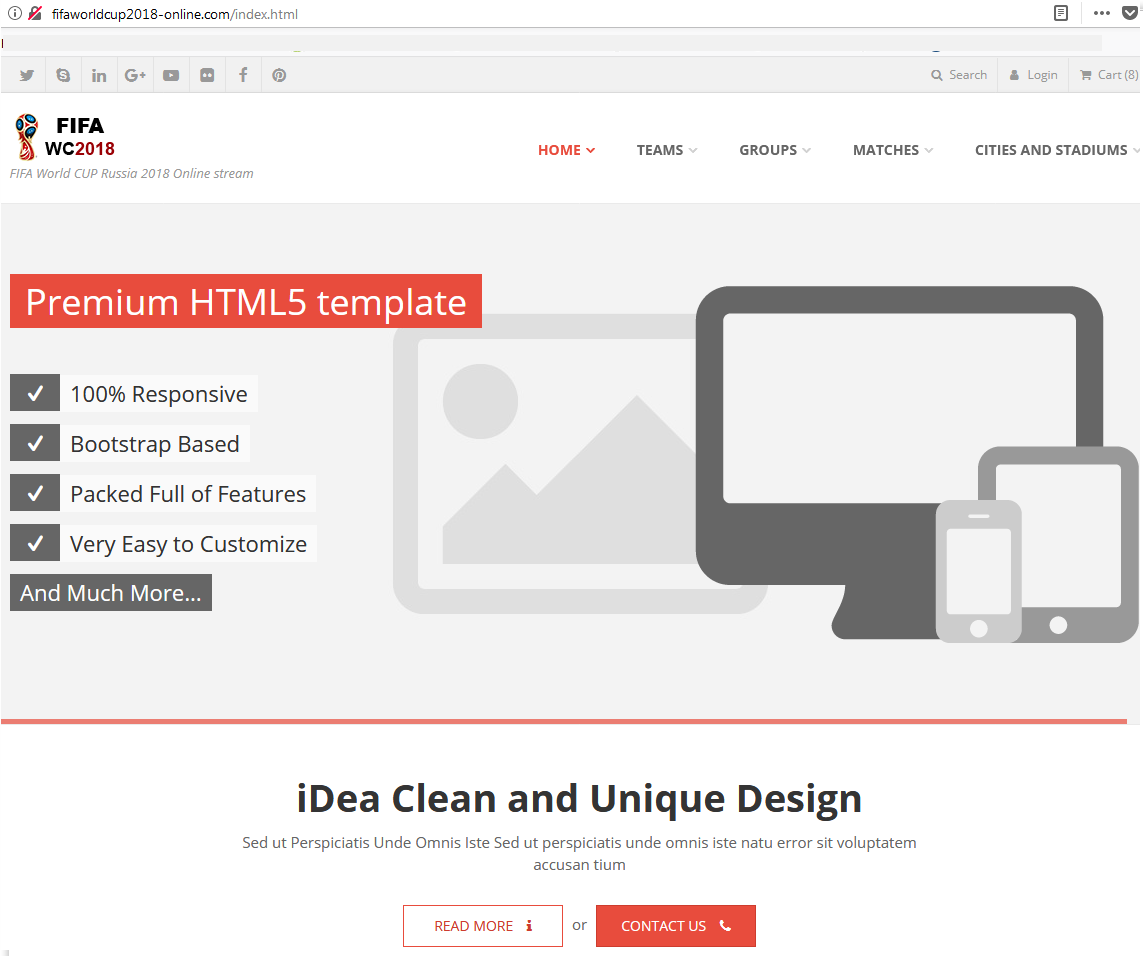
Alongside social engineering, phishers deploy malicious programs in the pursuit of users’ personal data and cash. For example, a fake site offering online broadcasts can plant malware on the victim’s computer under the guise of a Flash Player update required to view the match.
In some cases, phishers have no interest at all in bank accounts and payment details. For instance, under the pretext of receiving a World Cup-themed update for the video game FIFA Soccer, users are prompted to enter their account credentials for the Origin platform on a fake login page. If there are games of interest under the victim’s profile, the cybercriminals change the login/password and link the account to a new email address for subsequent resale.
In late May, a few weeks before the start of the championship, phishing emails offering cheap flights from the major airlines were all the rage. In addition to fake soccer ticket giveaways, there were draws seemingly on behalf of airlines offering free plane tickets.
Tricks of the trade
To make their sites seem credible, cybercriminals register domain names combining the words “world,” “worldcup,” “FIFA,” “Russia,” etc. (for example: worldcup2018, russia2018, fifarussia). Normally, though not always, such domains look unnatural (for instance, fifa.ucozx.site) and have a non-standard domain extension. So in most cases, a close look at the link in the email or the URL after opening the site should be enough to avoid the bait.
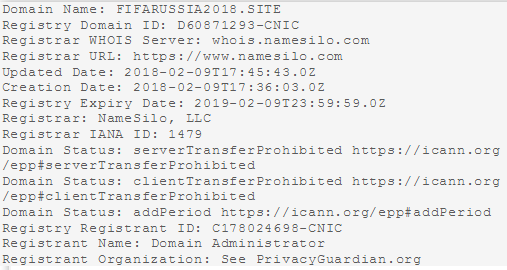
Likewise with a view to lulling user vigilance, cybercriminals acquire the cheapest SSL certificates available: relevant authorities often fail to verify the existence of the entity acquiring the certificate, meaning that the scammers get the all-important HTTPS in front of their address. To spot a fake, it is enough to look at the domain’s WHOIS data. Scam websites tend to have been registered quite recently and for a short time, and their owners are usually private individuals. What’s more, detailed information about the owner is often hidden.
Besides active domain names, we logged a large number of “sleepers”: on them you might find a placeholder page, if that. Cybercriminals use them as a backup: if one domain is blocked, the site moves to the next.
Conclusion
The above describes only the most popular scams exploiting the World Cup theme. Nevertheless, it provides a fairly complete picture of how cybercriminals operate and what they want. In addition to the above, we expect shortly to see an explosion of phishing sites offering cheap airline tickets to World Cup host cities, as well as fake mailings supposedly from popular accommodation services with “special offers.”
To avoid being duped, follow these simple rules:
- Buy tickets only on the official FIFA website or at official ticket offices.
- For online purchases (not only during the tournament), get a separate bank card and set a spending limit.
- Do not open links or attachments in emails from unknown senders, even if they seem legitimate.
- Check the addresses of links in notifications from known services; at the slightest suspicion, do not click, but open the site manually in the browser.
- To preserve your money and nerves, never buy products advertised in spam.
- Use the latest security solutions to protect against cyberthreats, and keep the databases up-to-date.
2018 Fraud World Cup





























j.vijay
We viewers expect Argentina to win this 2018 world cup. But you organizers have shown a wrong way. That Croatia team should not win the 2018 FIFA World cup. Nor even Germany or that Brazil should win this 2018 World cup.