
“Ido, we will address this compromise with Miss. XXXX directly. Thank you for notifying us,” said the last email received from Miss. Patricia Falcon, Information Security Policy & Awareness Specialist at the University of Brown, Rhode Island. Suspected spear phishing campaign attempting to steal users’ credentials by sending phishing emails masquerading as Google recovery.
From the beginning:
When the first email arrived in one of my Gmail inboxes I thought it was just another phishing scam – report it and toss it into the trash. But then I thought, hold on… it made its way through all the Gmail spam filters, so why not take a quick look.
That was on 5 October, an email with a “NO REPLY.” alias in the Sender field was marked as unread and after clicking it, a Google recovery email opened. Next to its subject was a profile picture of a person I didn’t know. Well, I thought, hackers don’t tend to post their pictures on their own phishing emails. So I checked the details and it was an email from Brown University, located in Rhode Island, United States.
Could it be a spear phishing campaign against the university?
On second thoughts, it was only one email. Maybe the person was lured by some appealing content into clicking a link where he simply entered his username and password to a fake form that hijacked his credentials.
First incident: Yet another phishing email
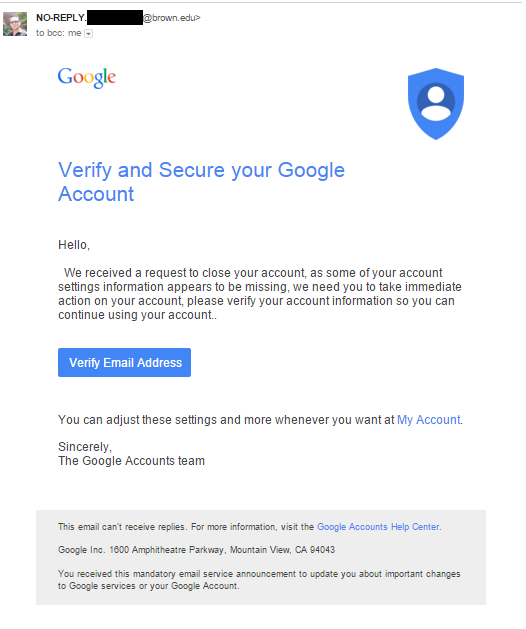
Browsing through the body of the email, I got the impression that it was very well written and was not some first-timer’s attempt. Not many obvious mistakes. Can you spot any?
Fake email from Brown University compromised account
- Funny – the old Google logo is used.
- First line after “Hello” has a space before the first sentence starts.
- “The Google Accounts team“? Who are they? And a capital ‘T’, surely?
- Close my account because info is missing and then verify existing info to continue using it? Where’s the logic in that?
- The button should say “Verify Account Details” not “Verify Email Address”, right?
We could spot some more, but that’s enough for now.
With all that in mind, the picture is the first thing that immediately draws your attention. It’s because this is a valid Gmail account of a person named Ph****p P**g. This person works for Brown University and brown.edu email servers are actually hosted by Google. That means that the compromised account can initially send phishing emails to any Gmail user account without them hitting the spam folder – not until it’s being reported as spam.
After trying to notify Mr. P**g in every possible medium he existed in online, I finally gave up. We reported the phishing attempt registered as an ow.ly short link that redirects to a domain named after a song by a Nigerian rapper, and hosted on GoDaddy.
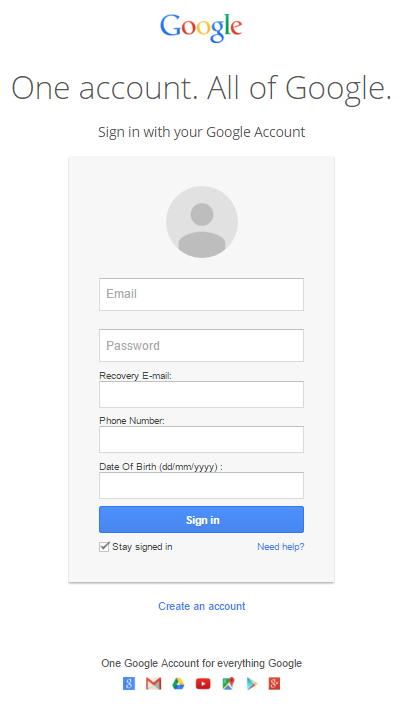
Two domain names have been identified so far; however, the IP address indicates massive use of phishing and even kits available for direct download and use. One of the domains found was the initial redirection URL from the malicious email short link and the other one was embedded in a PHP form action attribute, located within the phishing website’s /index.html page, masquerading as a legitimate Google recovery form.
Fake Google recovery form
Here is the chain of events from the victim’s point of view:
- Compromised Gmail account sends a message to the Gmail victim – Not spam.
- Victim clicks the fake “Verify” button and the embedded short link executes.
- Short link becomes a long link redirecting to hxxp://shokiti-bobo-crew[.]net/<your ip>/index.html. (Fake Gmail Recovery)
- The page sends a fake Javascript alert() that the victim’s Gmail account has been logged out.
- Clicking OK reveals a form similar to the Gmail login page, only with additional fields, such as recovery email, phone and date of birth.
- Submitting the PHP form sends the data to another malicious server – hxxp://owo-ni-boiz[.]net/auth.php
- After submitting the form, the page redirects back to Gmail – which was logged in the whole time – persuading the victim that the fake logout alert() message from step (4) was real.
The second [Co]incident
20 October, 8:00AM, another email arrived. To my surprise, it had the same origin – brown.edu – but a different victim.
It was now a woman. Her name is Q***h T**n, a former employee of the university and a current LinkedIn employee. Her account was immediately deleted after we reported the scam to LinkedIn.
LinkedIn employee account deleted after Gmail account was compromised in the attack
This email was different, suggesting that our threat actors have many templates at their disposal. However, the domains were the same. Since she is a former employee, it might mean her account was taken over while her account was disabled. It’s possible that the attackers took over a server that has modified privileges and they have managed to reactivate the dormant accounts of former employees.
Second fake email to come from a former Brown University employee
Issues spotted:
- No “Hello” this time – straight to the point.
- Non-US spelling: “take a look at the help centre or watch the video“
- Capital ‘R’ in ‘required’ is missing from subject.
- Russian? <img alt=”Логотип (Google Диск)” border=”0″>
- under “to bcc” there is a tiny button that was supposed to display a Google logo. Instead, it is broken and the HTML attributes are in Russian. “Logotip (Google Disk)”, says the alt.
- Lastly, this redirection is using bit.ly, not ow.ly
This time the navigation is the other way around. If the first instance was redirecting to hxxp://shokiti-bobo-crew[.]net/ to submit a form that was sent to hxxp://owo-ni-boiz[.]net/, then this time the address hxxp://owo-ni-boiz[.]net/, redirects to hxxp://shokiti-bobo-crew[.]net/mission/xconactc.php
We were the first to submit the URL to Virus Total, meaning it’s still fresh. No anti-viruses identified the link as malicious.
Conclusions:
OWO NI BOYS and SHOKITI BOBO are both songs by Nigerian rappers. This suggests that the attackers are influenced by rappers such as Olamide and Kida Kudz or are trying to create this false sense for analysts.
The second piece of information was the Russian Google Drive logo found in second incident. Both creates assumptions about threat actors way of thinking, either by injecting false information or by making terrible mistakes.
One thing is for sure – Brown University is suffering from a few compromised accounts and this attack is still active.
0xHACKED: Brown University Accounts Distributing Phishing Emails





















Linda
Our second e-address (also thankfully protected by Kaspersky) has received numerous emails, purporting to be from many different legitimate entities (Fingerhut, Medicare, etc.) with the extensions: eku.edu (Eastern Kentucky U), mt.gov (state of Montana), and at least one other.
I wasn’t sure who to report this to so have done nothing yet. Your report on Brown U was an “aha” moment. Thanks.
Ido Naor
Hi Linda,
Thank you for contacting Kaspersky Lab. We will be happy to help.
Please find my Twitter account handle at the top of the page. Contact me and we can engage to remediate the incident you’re experiencing.
Regards,
Ido