
While intercepting traffic from a number of infected machines that showed signs of Remote Admin Tool malware known as HawkEye, we stumbled upon an interesting domain. It was registered to a command and control server (C2) which held stolen keylog data from HawkEye RAT victims, but was also being used as a one-stop-shop for purchasing hacking goods.
WhiteHats on the prowl?
Before diving into an analysis of the server, it is worth pointing out some interesting behavior spotted in several of the victims’ stolen accounts. A group of WhiteHat hackers who call themselves Group Demóstenes were found to be working around the clock, trawling the internet and looking to exfiltrate stolen data from C2 servers. When such a server was found, the group looked for a backdoor that would give them control over the filesystem. They would then monitor the incoming, stolen data. Either manually or automatically, they would collect the stolen credentials and send emails to the victims’ accounts. These emails contained an attachment with proof that the user’s machine has been compromised. In addition, they advise the user to change passwords immediately and offer to help.
|
Hi *********** Our SERVERS detected information from a server on the US, we don’t even know goverment or another sourse …. we send a file with all your logins and passwords of all your accounts from hxxp://www.p******op[.]biz/******* Name PC USER-PC have a keylogger harm report All That You write, messages, passwords or more. ¿Why we do it? PLEASE WRITE ME AT THIS MAIL FOR KNOW IF YOU KNOW ABOUT THIS |
The email above appears in two languages, English and Spanish. The name of the group appears to be of Portuguese origin, though it is not certain.
The shopfront: the command and control servers
Scanning for network services which are running on the C2, we discovered that it contains not only a back-end for storing stolen credentials but also a front-end for selling some of them, alongside many other “goods”.
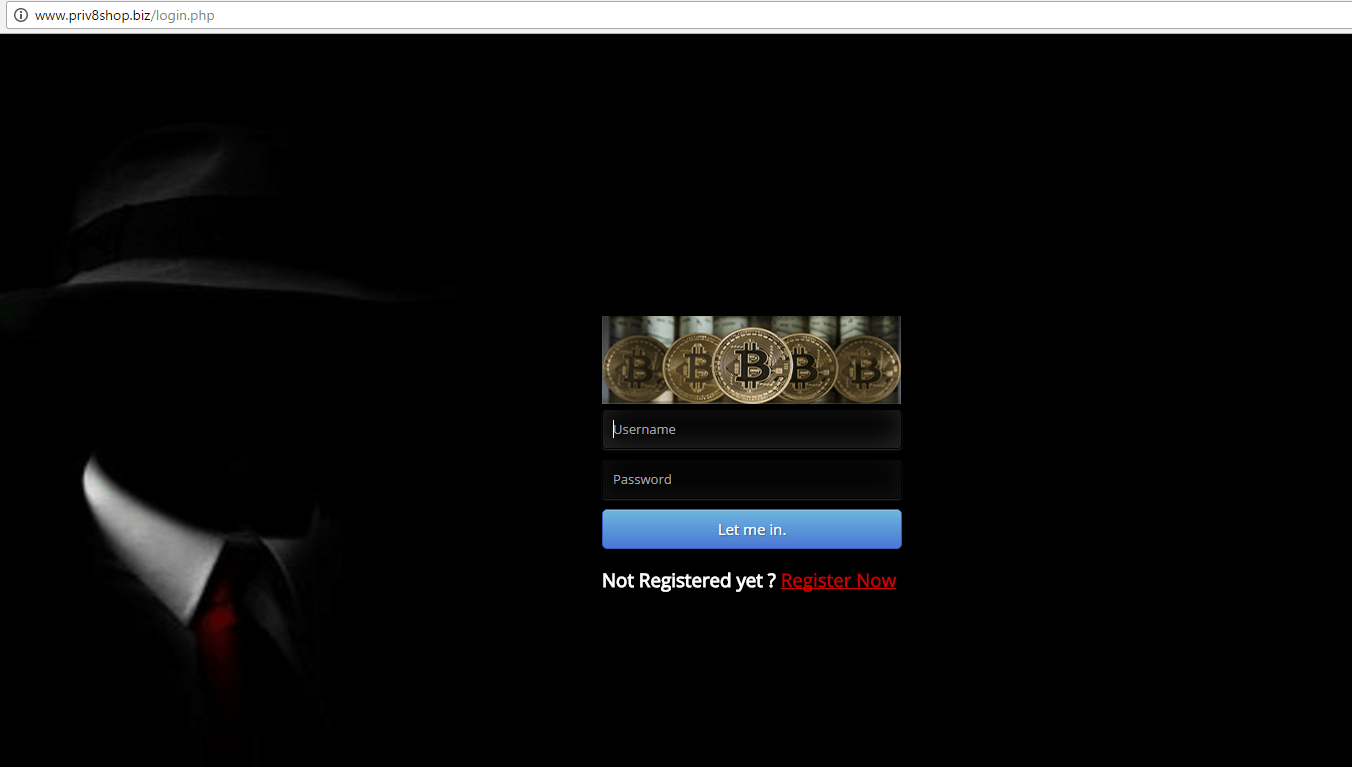
Browsing the domain that communicated with the HawkEye RAT samples disclosed a login page. Given the fact that the server was newly operational, it allowed users to register an account and login to purchase the goods on offer.
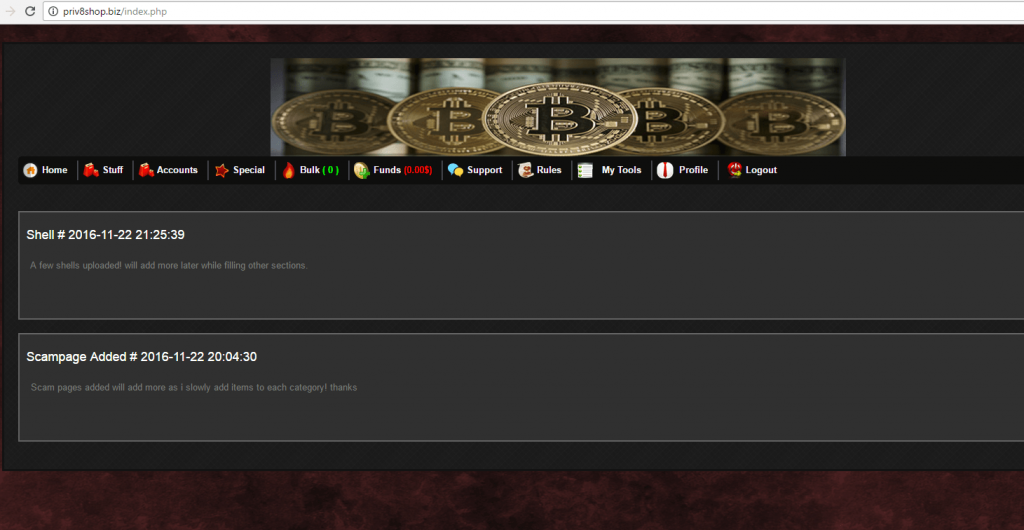
After registering on the C2 web application, there was no sign of the stolen data transferred from compromised machines. A forum-like web page opens up once a successful login is being processed.
The C2 was meant to securely store the stolen data; however, it contained a crucial vulnerability which allowed researchers to download the stolen data.
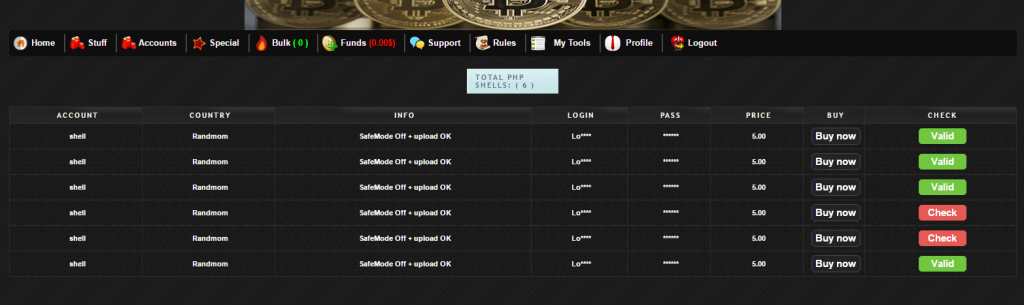
The C2 owners seem to have added six new Shell scripts on 22 November, just a week before the research started – a further indication of how new the operation is.
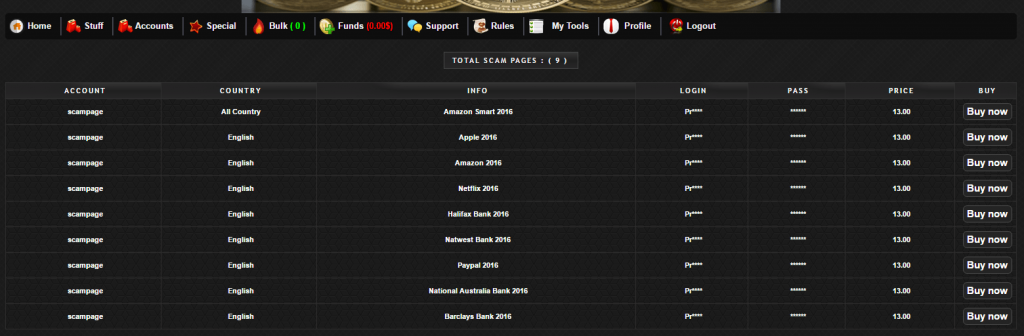
Another item for sale is scam pages, and some are multilingual. The attackers also reveal the scope of their victims, noting those who are registered to Amazon, Apple, Netflix and even National Bank of Australia and Barclays. The listing of the year next to the banking information probably refers to how up-to-date the scam pages are in terms of the bank’s website updates.
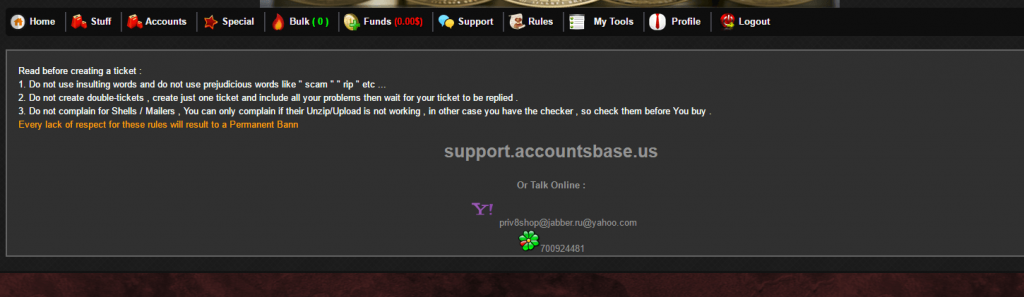
The attackers have spared no details and have added additional information regarding how one should act when using their services, and who to contact in the Support tab.
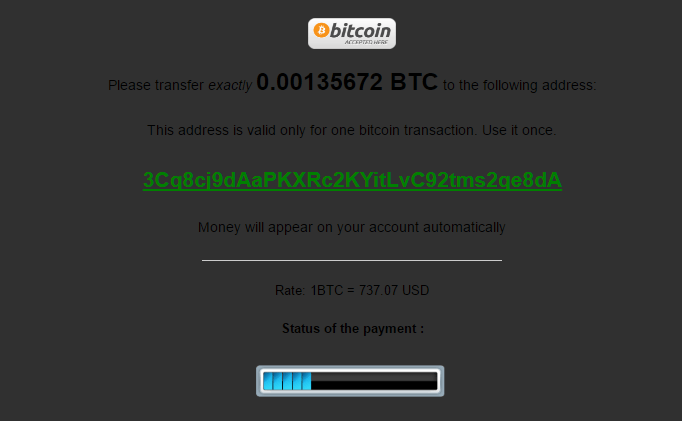
To purchase goods in the private shop you must deposit money into your account on the website. The attackers accept Bitcoins, PerfectMoney and WebMoney.
Back to the stolen data
As we described, HawkEye is a robust keylogger that can hijack keystrokes from any application being opened on the victim’s PC. It can also identify login events and record the destination, username and password. It is, however, limited to two-factor authentication and single sign-on.
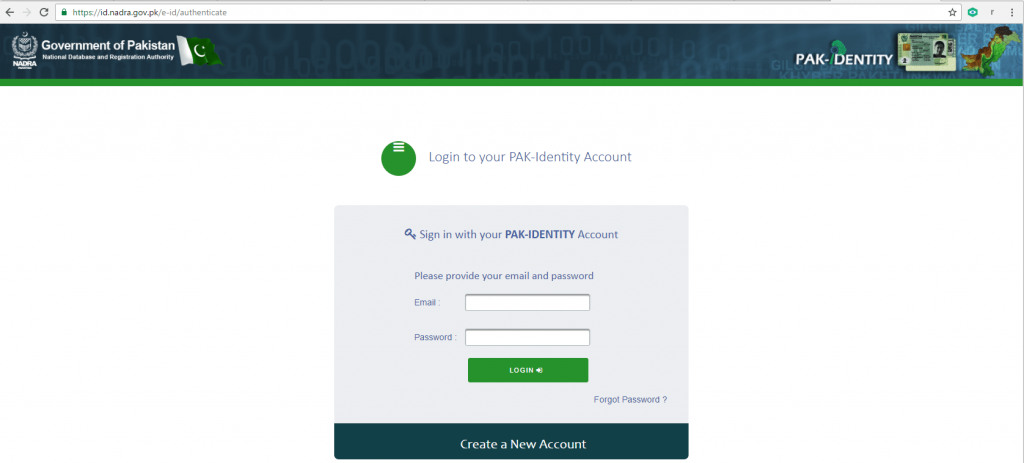
Stolen credentials on the server were found to be holding sensitive access passwords to government, healthcare, banking and payment web applications. Among them is the following web server which belongs to the Pakistani government.
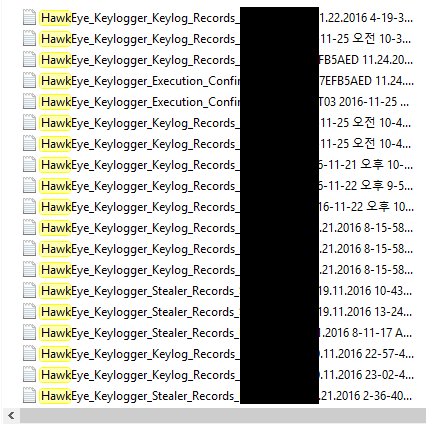
As mentioned, hundreds of machines were found to be compromised by just one C2. The following is a partial list of what was downloaded from the malicious server.
Usually, careless threat actors forget to remove test files which might contain sensitive data. In this case, we were able to obtain the attackers credentials from one very small file that was captured when searching related strings.
Target geography
The research is still ongoing and is currently affecting users located in APAC, such as Japan, Thailand and India, as well as parts of Eastern Europe such as Russia and Ukraine.


















One-stop-shop: Server steals data then offers it for sale