
After going out of fashion for a number of years, malicious macros inside Office files have recently experienced a revival. And why not, especially if they are a lot cheaper than exploits and capable of doing the same job?
Yes, that’s right, cybercriminals are busily recycling this old technique, introducing new obfuscation forms to make it more effective. Let’s look at two examples.
Sample 1
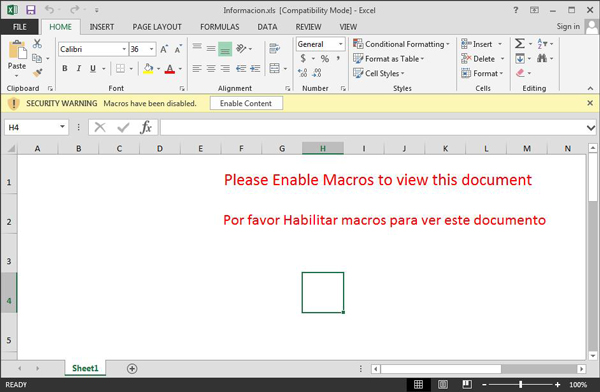
This is an excel file with malicious embedded macros. However if you use standard Office tools to look at the macros, depending on the version, you will not see anything malicious at all or you won’t be allowed to see the macros itself:
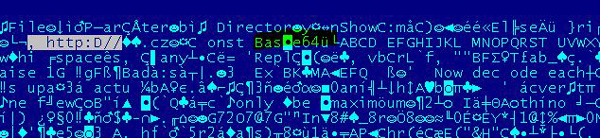
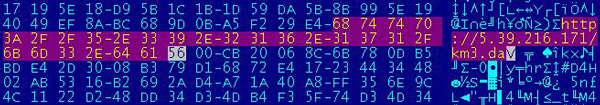
That is because the sample all strings in macros are obfuscated with a base64 encoding technique.
After de-obfuscation you can see clearly the URLs used to download the payloads:
This is a very simple technique but it is effective against simple heuristics that use string analysis of all incoming email attachments, and this is reflected in a very low VT detection https://www.virustotal.com/en/file/c916540dcab796e7c034bfd948c54d9b87665c62334d8fea8d3724d9b1e9cfc9/analysis/1403955807/
This particular sample is also interesting since in some Excel versions it is able to run macros automatically without prompting the user, enabling it. Once it has run, it drops a password-stealing Trojan directly onto the victim’s system.
Sample 2
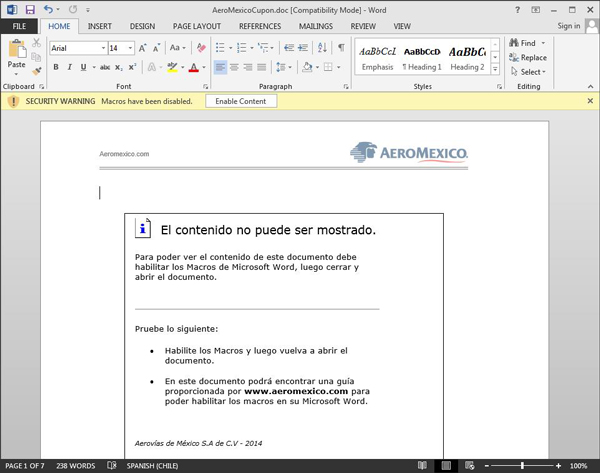
This another example is a fake Aeromexico ticket.
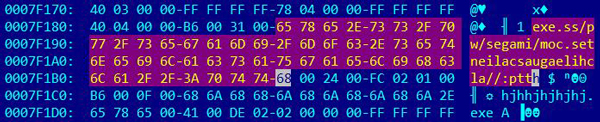
There is no obfuscation but the URL is written from right to left, which again it might be quite useful against simple GREP analysis techniques:
It is interesting to note that the first sample was found in the wild in Venezuela, the second in Mexico and then the third in Brazil:
This one drops a ChePro banker. All three malicious samples drop only Trojans that steal financial data, but the same technique can be easily used to drop any type of malware.
So does it mean that only Latin American cybercriminals use this technique? The answer is no, not really. Our relative user’s infections statistics show that actually the countries with the most attempted infections using this kind of malware are Germany and then Poland.
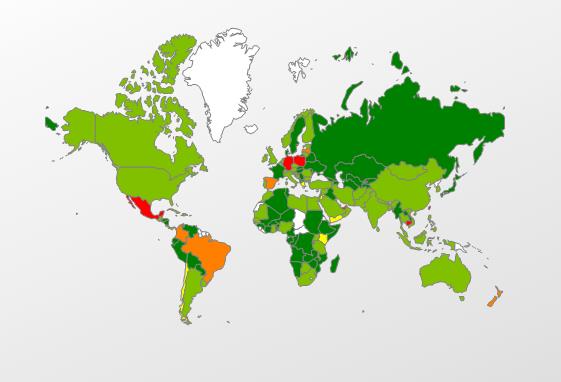
However, the technique is seen elsewhere, including Spain, Mexico, Brazil and others.
While analyzing malicious macro office files, you can see that the original document is created by one user and then somebody else (another criminal) assists in embedding the malicious macros.
The same technique can be easily used to drop any kind of malware in any country since this is all about social engineering and it will easily pass through email gateway security because it is basically an office document, and security email policies allow those.
You may follow me on twitter: @dimitribest






















Obfuscated malicious office documents adopted by cybercriminals around the world