
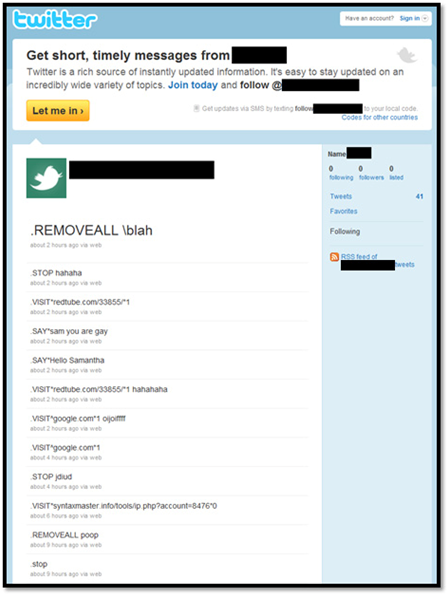
Today i found a new tool which will allow anyone to create a malicious program with just a few simple mouse clicks. When the malicious program is executed the infected computer is connected to a botnet which communicates via Twitter and is used for various illegal purposes.
The tool, which is publically available, is called TwitterNET Builder. It only requires two mouse clicks to create a malicious program which will turn a normal computer into a node in a botnet. TwitterNET Builder will create a profile on Twitter which the infected computer will contact to receive commands and instructions.
This malicious code does not contain any distribution mechanism and must be manually run on the victim computer, but these tools can be executed when combined with a drive-by attack or a worm that spreads via a new-found vulnerability, for instance.
At the time of writing, the tool has been released in two versions; Sunbelt describes the first version (http://sunbeltblog.blogspot.com/2010/05/diy-twitter-botnet-creator.html) as a tool with a handful of hard coded commands with static names which can execute functions such as downloading and executing files, performing distributed denial of service attacks, opening websites but also controlling the communication between the infected computer and Twitter. A detailed description of the available commands is mentioned in their original blog post.
The new version of the TwitterNET Builder allows the attacker to specify the names of the command making it much harder to identify which accounts are being used for controlling these botnets.
How do I protect myself against this?
Since this tool does not have its own distribution mechanisms it needs to be manually downloaded and executed – for example, it might arrive as an attachment in an email, or as a file sent via a instant messaging client. You need to be careful executing email attachments or files sent to you in a chat conversation. You also need to be careful that you do not get infected through a drive-by attack, which may exploit vulnerability in for example your browser.
Most of these malicious tools re-use functions and code which is easy to identify by effective antivirus software. Make sure that your anti-virus software is updated and that you have installed all security patches from all third party vendors




















New tool allows script kiddies to build botnets via Twitter!