
Cybercriminals are very actively targeting web sites which are not well-managed, so as to abuse them for their malicious activities. Damage to web sites in Japan has increased since last year, which is alarming to Japanese Internet users. Kaspersky Labs Japan has observed more than 2,800 compromised web sites between January and March 2014.
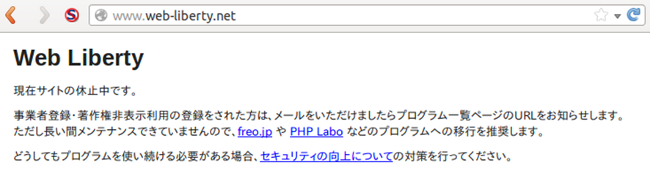
WordPress is a popular blogging tool worldwide, but it is often plagued by vulnerabilities which can result in compromised web sites . A similar Japanese-made tool, “Web Diary Professional” (WDP), also experiences such problems. WDP is widely used in Japan, with its Japanese user interface and tutorials.However, it is no longer supported.
Official EOS announcement of WDP:
A new tool has already been introduced as its successor, and the developers have recommended that people migrate. However, a significant number of web site administrators are still using the obsolete WDP, exposing themselves to the threats of cybercriminals.
I tried a Google search using specific keywords that indicate the possibility that WDP is being used, and found approximately 500,000 web sites (as of April 2014). Of course, not all these web sites are vulnerable, and some may be duplicates. However, from a check of the results (web sites at the top of the search results), most of them used WDP and there were only a few duplicates.
On investigation, almost 80% of the live WDP-based web sites were found to have a problem. Specifically, a file which contains a hash of the password for user authentication could be viewed from the outside. If the password was a simple one, it is very easy to decrypt it using a password cracking tool.
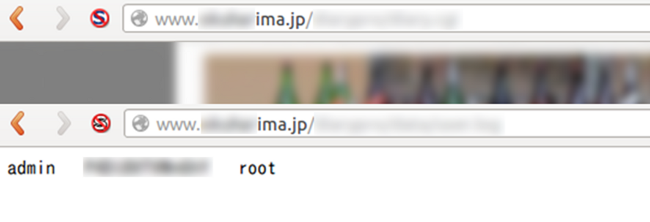
Some web sites with the problem:
The WDP package has a file which contains user account information (user account, password hash and permission). The problem is: anybody can see the file by default.
List of URLs with the hash of administrator passwords:
- ak*********ra.ne.jp : J1wmEoM.bkL**
- ho********el.co.jp : M8E16gZ2Ewb**
- ku***********ou.com : I17D74cikmT**
- sp******ft.co.jp/sh************bu/blog/ : aS1WTP.kHtM2**
- ts*******mi.net : N5S6jTCx/jm**
- www.by***in.or.jp : M5KnJS9KBGr**
- www.ed*************ma.jp : L9axf8TE5Vz**
- www.su*****rt.co.jp : X4YGGUaW3gz**
- www.ta*****ai.or.jp : J7EnglocxcP**
- www.te****46.com : B3bgZ6bilnO**
With a password cracking tool, a simple password can be cracked in a very short time.
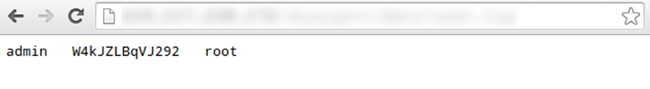
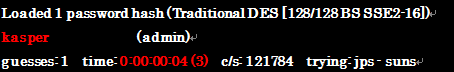
To see how easy it is to do, let’s take a look at a sample hash produced in my test environment:
Result of password cracking tool shows:
An attacker could get web administrator permission this way.
As the result of an attempt to decrypt the list of password hashes with the tool, 26.61% of the hashes were decrypted into the original passwords in a short time.(3 hours)
- 1234 (www.so*****ma.org)
- 1234 (www.cl******ir.com)
- 6636 (ts*******mi.net)
- 0123 (www.uc*****or.com)
- 0123 (www.yo*********ai.jp)
- mayu (gc**************rq.or.jp)
- 12345 (www.pa***********te.com)
- 1122go (www.os*******se.com)
- n24w17 (www.se****-h.com)
- kurosaki (ku***********ou.com)
Once the attacker knows the administrator’s password, he is able to edit the web site as he wishes. Actually, I found several web sites being manipulated. On such web sites, there were spamming tools, files that show messages of attackers, DDoS tools, backdoors, etc. It is easy to assume that these web sites have been abused by someone with malicious intent.
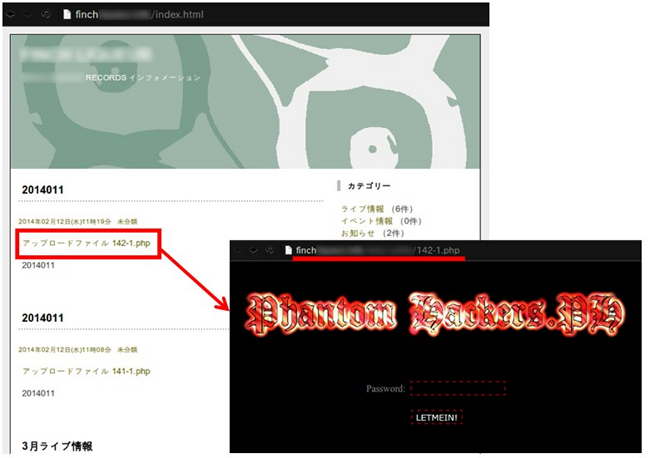
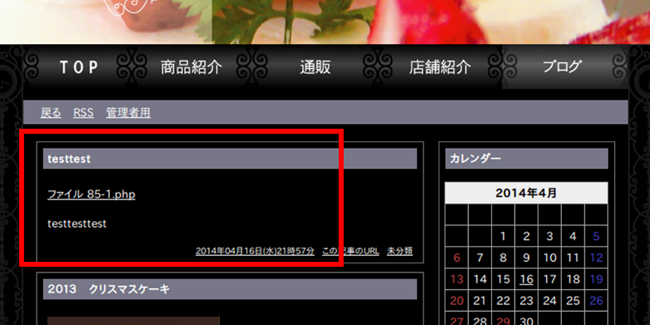
An example of a tampered web site:
An attacker’s message:
DDoS attacking tool:
Backdoor Web shell:
The worst case observed was a sample of a cloud service. Hundreds of web sites seemed to be hosted and were operating on a single server with this service, and a backdoor was installed on one of the web sites. Using this backdoor, an attacker can manipulate other clean web sites on the same server, possibly tampering with them or stealing important data.
Once again, the support for WDP has already been terminated, and the developer has been recommending that its users migrate to the new tool. For those who have some reason to keep using WDP, the developer has kindly introduced a method of enhancing security. In case you are still using the obsolete WDP with your web site or service, it is highly recommended to take measures as soon as possible in order not to become a victim or an unwitting perpetrator.
Kaspersky Lab products detect the set of malicious tools (backdoors, etc.) found in this research as:
- Backdoor.PHP.PhpShell.*
- Trojan-Spy.PHP.PhPen.*
- Backdoor.PHP.C99Shell.*






















Cybercriminals targeting obsolete Japanese blogging tool