
Several media reported the news on January 7th, 2014, that a PC associated with “Monju” (the Fast Breeder Reactor of the Japan Atomic Energy Agency) was infected by malware and there was a suspicion of information leaks. Some pointed out that the infection had possibly been led by the abuse of the legitimate update of “GOM Player”, which made it big news. GOM Player is a free media player with popular video/audio codecs built-in, favored by many Japanese people. It is different from similar free media players in some notable points: it supports major file formats such as AVI, DAT, DivX, MPEG, WMV to name just some; and it officially deploys a Japanese version. Its users are said to be more than 6 million in Japan.
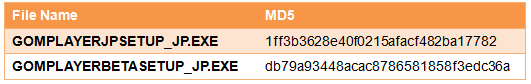
We received the sample file named “GoMPLAYER_JPSETUP.EXE”:
The sample is an executable file compressed in RAR format. When it is executed, it unpacks itself and runs the executable file included in the archive. Fig1 shows the files included in the RAR archive:
Fig1: Files within “GoMPLAYER_JPSETUP.EXE”
Two files are included in the archive:
“GOMPLAYERJPSETUP_JP.EXE” is a legitimate update file of the GOM Player. “GOMPLAYERBETASETUP_JP.EXE” is another executable file in RAR format. Fig2 shows the files included in”GOMPLAYERBETASETUP_JP.EXE”.
Fig2: Files within “GOMPLAYERBETASETUP_JP.EXE”
“GOMPLAYERBETASETUP_JP.EXE” has five files which include malicious code. Among them is “install.exe”, which runs from “GOMPLAYERBETASETUP_JP.EXE”.
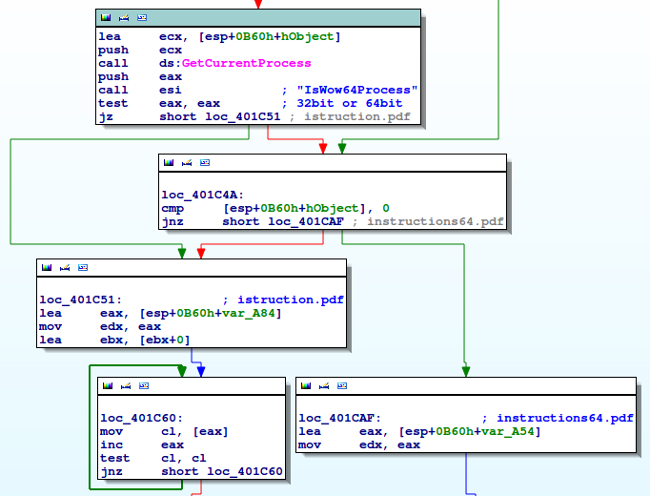
The “install.exe” checks which environment it is running in, 32bit or 64bit, using IsWow64Process function (Fig3):
Fig3: Estimation process by the “install.exe”
Based on the result of the estimation process, it reads “dll.tmp /dll64.tmp” (based on the environment) and xor-decrypts it with “x14”, then generates “install.ocx” in “%windir%temp”. Fig4 shows the xor decryption process.
Fig4: xor decryption process of “dll.tmp/dll64.tmp” using “x14”
Then it copies “instructions.pdf /instructions64.pdf” (based on the environment) to the same folder as “install.ocx”.
It creates two values “Default”=”%windir%install.ocx” and “ThreadingModel”=”Apartment” in the following parts of the registry:
“HKEY_CLASSES_ROOTCLSID{ECD4FC4D-521C-11D0-B792-00A0C90312E1}InProcServer32” “HKEY_CURRENT_USERSoftwareClassesCLSID{ECD4FC4D-521C-11D0-B792-00A0C90312E1}InProcServer32” “HKEY_USERS2S-1-5-21-1439904799-1247934098-3846997294-1000SoftwareClassesCLSID{ECD4FC4D-521C-11D0-B792-00A0C90312E1}InProcServer32” “HKEY_USERSS-1-5-21-1439904799-1247934098-3846997294-1000_ClassesCLSID{ECD4FC4D-521-11D0-B792-00A0C90312E1}InProcServer32”
After registration, it restarts “explorer.exe” to load “install.ocx” into the process of “explorer.exe” to infect it. The “install.ocx” loads “instrucsion.pdf/instructions64.pdf” in memory, xor-decrypts it with “x14”. Then it jumps to the decrypted entry point to execute the malware.
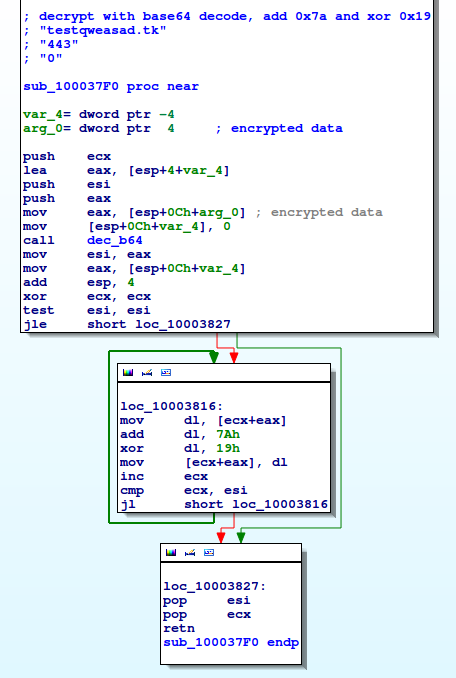
In the memory of the decrypted “instruction.pdf/instruction64.pdf”, it reads the 0x400byte data at the foot of the file. It searches strings such as “AAAAAAAA”, “PPPPPPPP”, and “BBBBBBBB” from the data, then extracts the data which follows them. Finally, it decodes base64 and calculates “add x7a” and “xor x19″(Fig5).
Fig5: Decryption process
The table below shows the name of the data before/after decryption:
These strings are used in the domain name and the connection port for the C and C server.
Kaspersky products detect the malware as “Backdoor.Win32.Miancha.*” (Fig6).
Fig6:Kaspersky products detected “Backdoor.Win32.Miancha.b” in the sample
The reason why this free software has been installed in Monju remains unclear. The details remain hidden since its investigation by the law enforcement is ongoing. We will keep a close eye on the situation.





























Abused Update of GOM Player Poses a Threat