
I’m sure you’ve read or heard about the malware attacking boletos – the popular Brazilian payment system – and how lots of malicious code is able to modify it, redirecting the amount paid to an account owned by criminals. Despite the fact that some numbers were overestimated by some companies and media outlets, these attacks are of particular interest and the Brazilian bad guys are quickly developing and adopting new techniques. Trust me: everything you read about boleto malware was only the tip of the iceberg; our complete research into this topic will be presented at the next Virus Bulletin conference.
The boleto malware campaigns combine several new tricks to infect and steal from more users. One of the most recent is the use of non-executable and encrypted malware payloads XORed with a 32-bit key and compressed by ZLIB. It’s no coincidence that a very similar technique was used by ZeuS GameOver some months ago, but this time the files are using extensions such as .BCK and .JMP, instead of .ENC.
We have evidence of Brazilian criminals cooperating with western European gangs involved with ZeuS and its variants; it’s not unusual to find them on underground forums looking for samples, buying new crimeware and ATM/PoS malware. The first results of this cooperation can be seen in the development of new attacks such the one affecting boletos payments in Brazil.
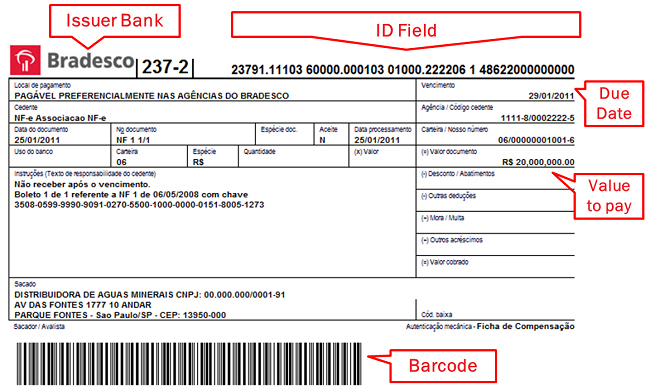
A typical Brazilian boleto: using web-injection to change the numbers in the ID field is enough to redirect the payment
In February, security expert Gary Warner wrote about a new version of ZeuS campaign that downloads some strange and non-executable .ENC files to the infected machine. Our colleagues at CrySys did a very detailed analysis showing how this is an effective technique for passing through your firewall, webfilters, network intrusion detection systems and many other defenses you may have in place, as a tiny Trojan downloads these encrypted (.ENC) files and decrypts them to complete the infection.
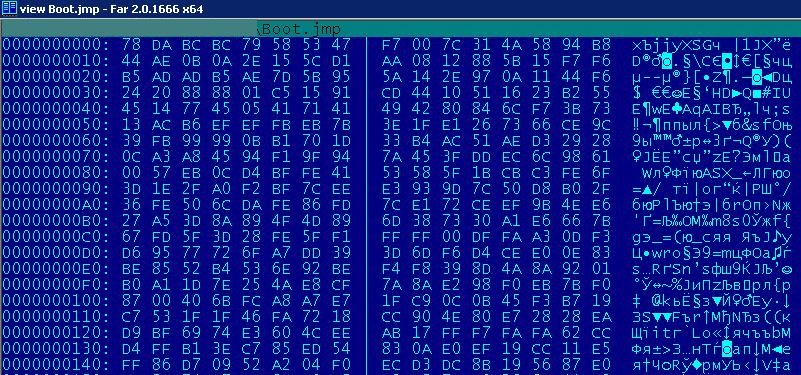
Brazilian cybercriminals decided to use the .JMP extension in files encrypted in the same way, and downloaded by several small Trojans used in boletos and Trojan banker campaigns. This is what an encrypted file looks in the beginning:
After removing the encryption we can see it as a normal PE executable:
The criminals tend to encrypt the big payload files using this technique, as well as some removal tools such as Partizan and big Delphi Trojan bankers that include images of Internet banking pages. The aim is always to encrypt the payload and make it undetectable, so that it’s not recognized as a normal portable executable.
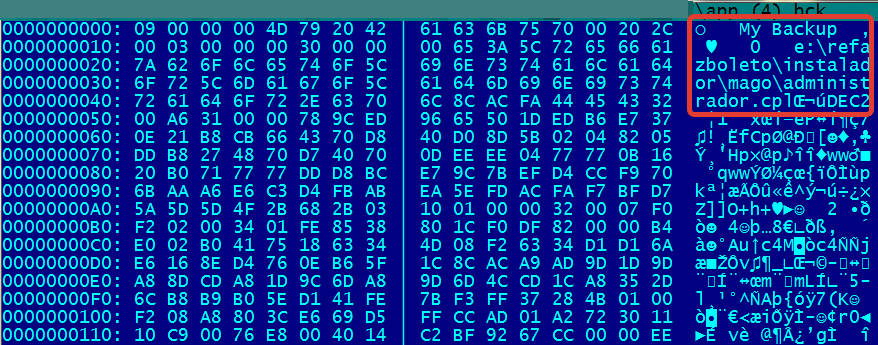
Other files of interest are those with .BCK extensions – they are packed with an as yet unknown application that appears to be a commercial backup app. Just checking the head of the encrypted file is enough to see what’s inside – in this case it is a malicious CPL file used in the boletos campaigns:
“refazboleto” is Portuguese for “rebuild boleto”. It points to a CPL file
Our antivirus engines are prepared to unpack and detect .JMP and .BCK files like these. These facts show how Brazilian cybercriminals are adopting new techniques as a result of the collaboration with their European counterparts.
Thanks to my colleague Alexander Liskin for help with the analysis.
ZeuS GameOver, Brazilian Trojans and Boletos: an explosive combination




















Joanthan E. PIlling
This simply must be contained DATA engineering protocol has advanced beyond sectors of security and these advanced operation protocols needs to be contained immediately. Obvious this cyber warfare has developed beyond the Scope of human intelect itself and needs to be shut down with absolution. DATA storage containment units must assist in the decryption profiles and secure servers must reunite UN resolution stoppage. We must end this immediately. This is an Ordered statement. There is a serious intent to harm Damascus Syria and it must be contained before Muslim operatives are able to intercept and control this future.