
“Weibo”, a micro blog in Chinese, is really hot and has become fashionable in China lately. The number of users of the largest Weibo site Sina Weibo (www.weibo.com) has already reached 140 million. As usual, where there is popularity, there will be security concerns.
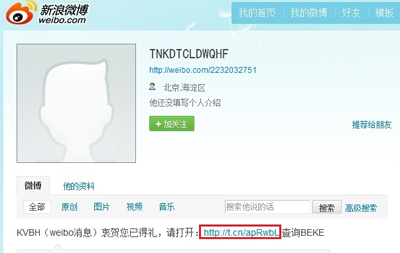
Today I found someone referring to my latest tweet, saying that I had won a big prize and needed to click the link to see the details. The guy’s name only consisted of some random letters, which made me cautious. Apparently this is a phishing URL.
I checked this randomly named user and found that he was newly registered but had already sent phishing URLs to lots of users.
Strange user with the strange name
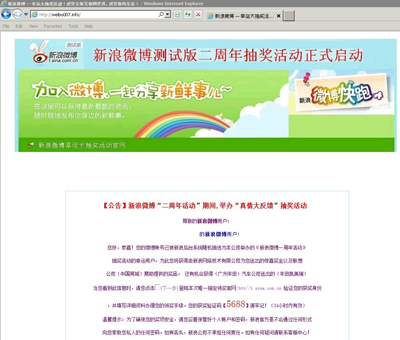
Unfortunately, if you click the URL, you will be redirected to a site called weibo***.info and a page will be displayed saying that you have won a Toyota Camry in a lucky draw held by Sina. But apparently, the hackers didn’t spend much time on the page design.
Poorly designed phishing page
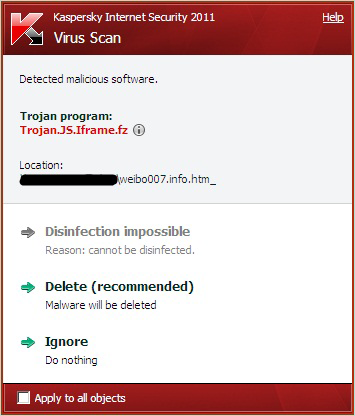
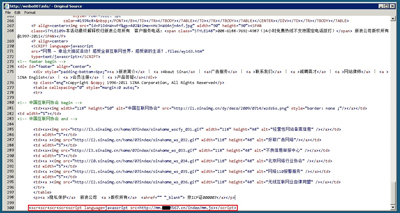
You can tell that it is a phishing page which is good, but it’s too late. At the bottom of the code on the phishing page you can find a special line of code.
Code redirecting you to another piece of malicious code
This line of code is already detected by Kaspersky as Trojan.JS.Iframe.fz. It can redirect you to another piece of malicious code that can exploit the vulnerabilities in your system to download and run malware on your system.
Another reason users click the URL without thinking is that in the micro blog the URLs are shortened and thus it is difficult to tell if it is malicious or suspicious. Therefore, while enjoying the micro blog, please be sure that you are under the protection of a reliable Internet Security product like Kaspersky and keep it updated.
















Yes to tweeting, no to phishing