
Over the last two years, deep in the slums of the Internet, a different kind of underground market has flourished.
The short, cryptic name perhaps doesn’t say much about it: xDedic. However, on this obscure marketplace anyone can purchase more than 70,000 hacked servers from all around the Internet.
xDedic forum login
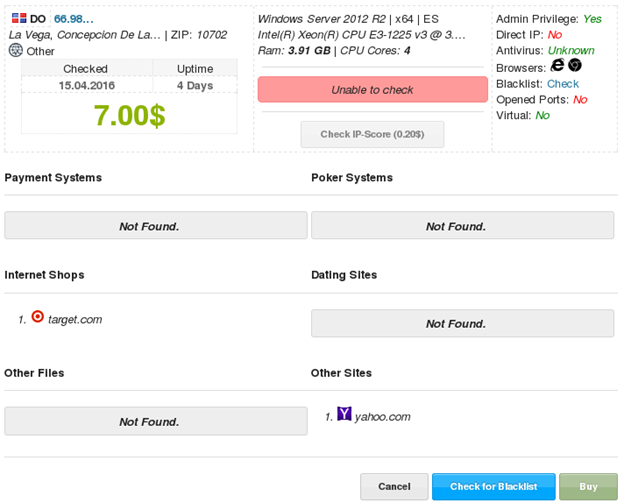
From government networks to corporations, from web servers to databases, xDedic provides a marketplace for buyers to find anything. And the best thing about it – it’s cheap! Purchasing access to a server located in a European Union country government network can cost as little as $6.
The one-time cost gives a malicious buyer access to all the data on the server and the possibility to use this access to launch further attacks. It is a hacker’s dream, simplifying access to victims, making it cheaper and faster, and opening up new possibilities for both cybercriminals and advanced threat actors.
Server purchase forum
To investigate xDedic, Kaspersky Lab teamed up with a European ISP. The research allowed us to collect data about the victims and the way the marketplace operates.
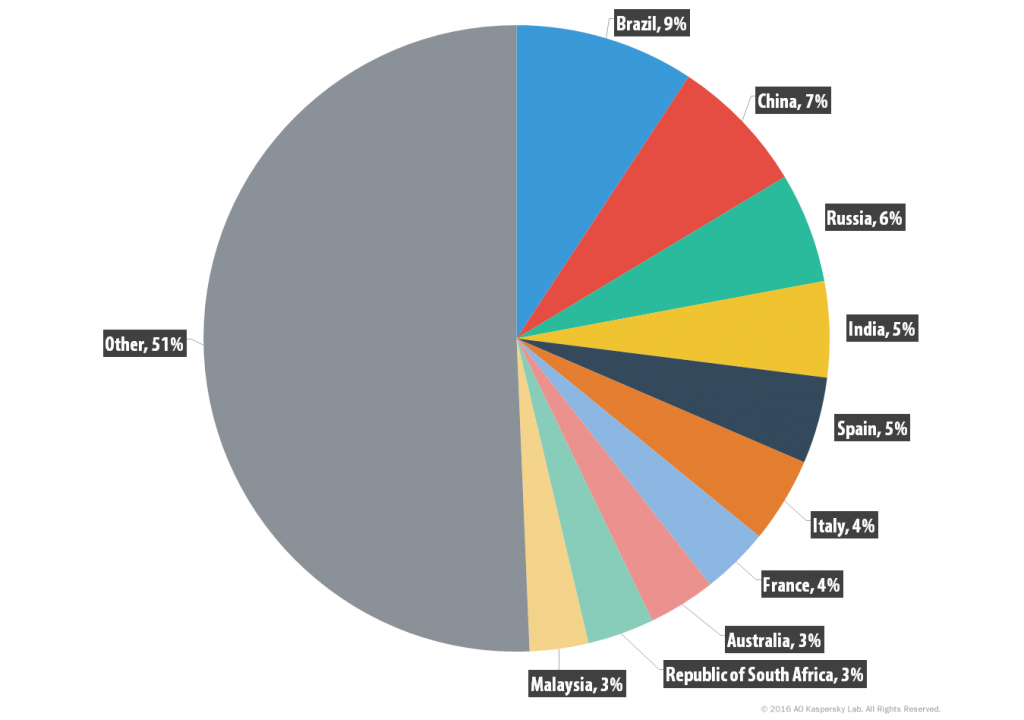
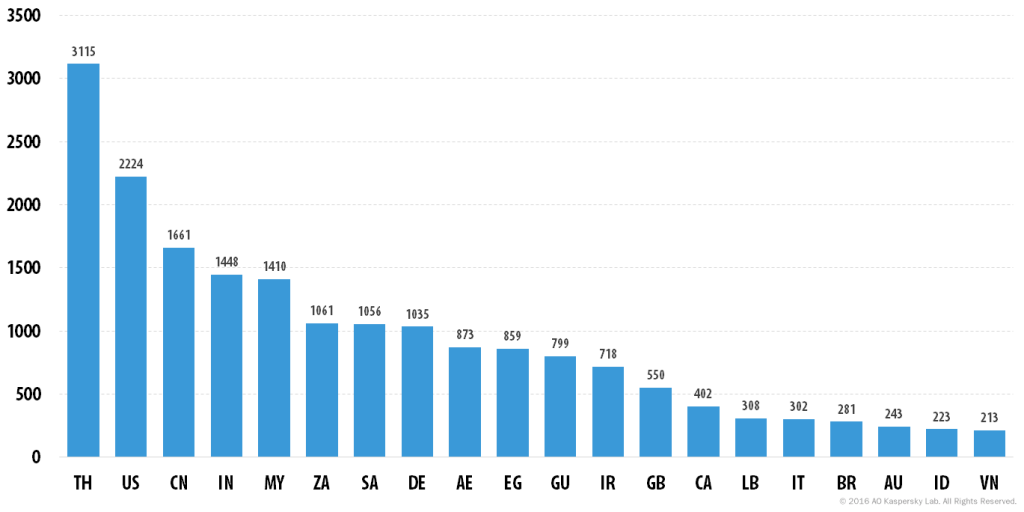
In May 2016, we counted 70,624 servers available for purchase, from 416 unique sellers in 173 affected countries. In March 2016, the number was about 55,000, a clear indication that the database of users and servers is carefully maintained and updated.
Top countries with servers on sale
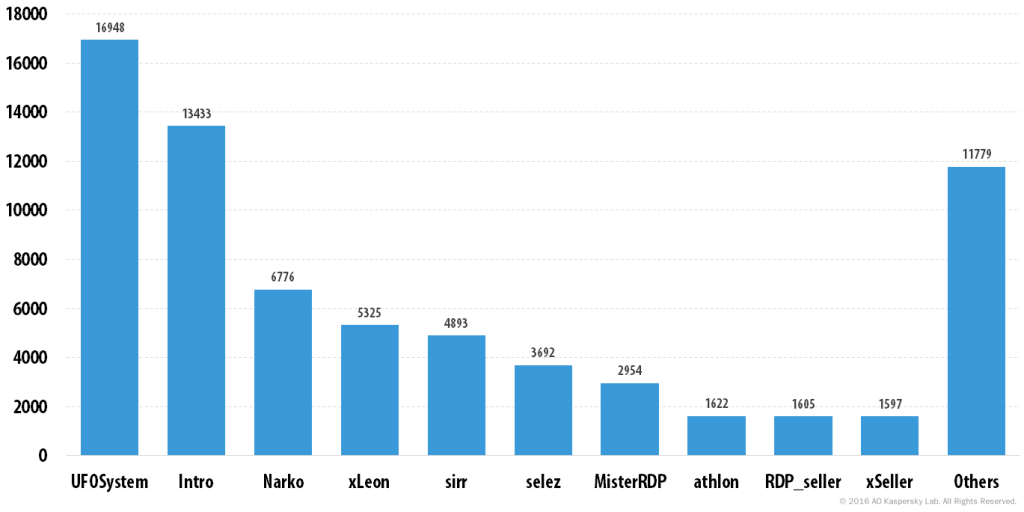
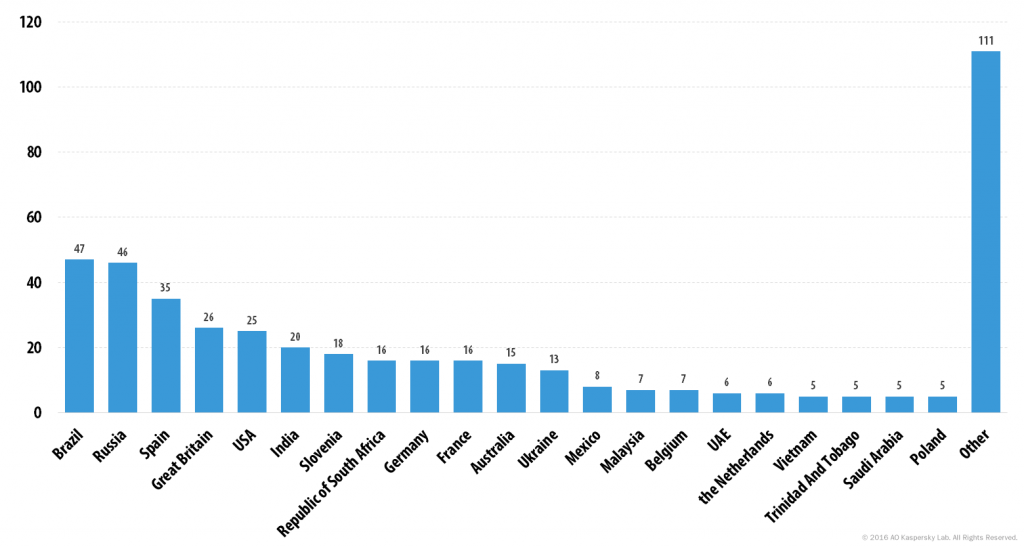
Interestingly, the developers of xDedic are not selling anything themselves – instead, they have created a marketplace where a network of affiliates can sell access to compromised servers. If the truth be told, the people behind xDedic have created what appears to be a “quality” service – the forum even includes live technical support, special tools to patch hacked servers to allow multiple RDP sessions and profiling tools that upload information about the hacked servers into the xDedic database.
Top 10 sellers – May 2016
So who are the xDedic sellers listed above? We have been able to identify a very specific piece of malware (SCCLIENT) which is used by one of them, and to sinkhole its C&Cs. This provided a glimpse into the operations of one of these entities, which, based on the number of victims, we suspect is either Narko, xLeon or sirr.
SCCLIENT Trojan: victims’ information from sinkholing (first 12 hours)
The profiling software created by the xDedic developers also collects information about the software installed on the server, such as online gambling, trading and payments.
Apparently, there is strong interest in accounting, tax reporting and point-of -sale (PoS) software which open up many opportunities for fraudsters:
| Spam and Attacking Tools | Gambling and Financial Software | POS Software |
|
Advanced Mass Sender |
Full Tilt Poker |
PosWindows |
During our research, we counted 453 servers from 67 countries with PoS software installed:
Servers for sale with Point-of-Sale software – May 2016
For instance, a malicious user could go to the xDedic forum, register an account, top it up with Bitcoins and then purchase a number of servers which have PoS software installed. Then, they can install PoS malware, such as Backoff to harvest credit card numbers. The possibilities are truly endless.
Kaspersky Lab has reported this issue with the appropriate law enforcement agencies and is cooperating in an ongoing investigation.
To read our full report on xDedic which includes IOCs, download the xDedic Marketplace Analysis PDF here.
* For more information about Kaspersky Lab Intelligence Services, Threat Reports and custom threat analysis contact intelreports@kaspersky.com
xDedic – the shady world of hacked servers for sale





















SW
This is why ip reputation services such as GetIPIntel need to be a part of your security implementation. You have to take action to prevent these bad ips from connecting to your network.
Jhoy Cristian
You talk too much
anonymous
I tested some random IPs from the pastebin list for Feb 2016, it seems to work well. It looks like most residential IPs score lower but regular hosting networks score high.
Martin
Excuse me if the question is trivial or stupid but I’m not well versed in terms of server security so: Is there an easy way to verify whether or not my company’s server has been affected (and/or access to it is available is for sale) without actually searching for the domain on their website?
AngryBirds
Good work Kaspersky! Our gift to you – hacked servers IP from xDedic. Download
http://pastebin.com/KCNJPDZZ
http://pastebin.com/E5YRNpgP
http://pastebin.com/qse8pTZR
http://pastebin.com/yNg2XCX1
http://pastebin.com/wNpvwW8z
http://pastebin.com/nVJ6r2ha
http://pastebin.com/VQAr9tut
http://pastebin.com/d4jVhs9M
http://pastebin.com/p7qK9pGh
http://pastebin.com/48eZAwCW
S
AngryBirds you are an idiot. You sent IPs in public, and now all will try to hack it. Remove the comments better. If you have some info to send for Kaspersky, do this privately.
CHR
@AngryBirds Can you share how you find true IP without 2 octets hidden? Another RDP/socks shop [redacted]shop.ru have very similar interface. Please mail tlp.ex.chr at gmail
Darlene Delgado
I was hacked. I have screen shots of the, “codes” that were used. You have no idea what I have been through with these guys. Many of the POS.exe and other Linux commands were used on my Android, Galaxy 6, and I sent an email not sure if it got through. Can you help me? (1st comment email address is wrong)
Darlene-
Clarinda Cadet
Informative discussion – I loved the analysis , Does someone know where my company could possibly grab a blank Bankruptcy B6G copy to work with ?