
You might think if you don’t use Internet banking, you’re not going to be targeted by phishers. Or you might have heard about phishing attacks targeting PayPal and eBay users, so you’re careful not to fall for fake emails from these organizations. But even if you’re reasonably security aware, there are phishing messages out there designed to catch you out!
We got a message today which seemed to come from Blizzard:
Of course, this message is designed to get people to give up their account details. Whoever created this email was smart enough not to include any links in the message – after all, lots of people are now on the lookout for signs of a typical phishing message. Looking for other typical signs doesn’t reveal very much: the mail client shows the sender address as wowaccountadmin@blizzard.com, although the email was actually sent from wowaccountadmin@blizzarid.com.
So what should you do if there aren’t any obvious signs that a message is a fake? One simple rule will help you protect yourself: if you get an email asking for your password or other confidential details, assume it’s a fake unless you can verify it by other means.

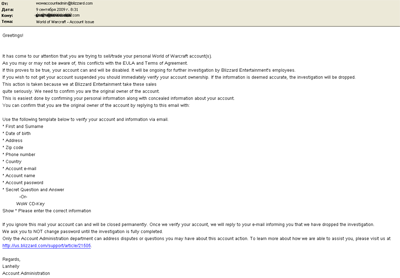













Would you answer this email?