
We spotted an interesting attack from Brazilian bad guys aiming to change the DNS settings of home routers by using a web-based attack, some social engineering, and malicious websites. In these attacks the malicious DNS servers configured in the user’s network device are pointed towards phishing pages of Brazilian Banks, programmed to steal financial credentials.
Attacks targeting home routers aren’t new at all; in 2011, my colleague Marta described malware targeting network devices like these. In Brazil we documented a long and painful series of remote attacks that started in 2011-2012 that affected more than 4.5 million DSL modems, exploiting a remote vulnerability and changing DNS configurations. But this “web-based” approach was something new to Brazilian bad guys until now and we believe it will spread quickly amongst them as the number of victims increases.
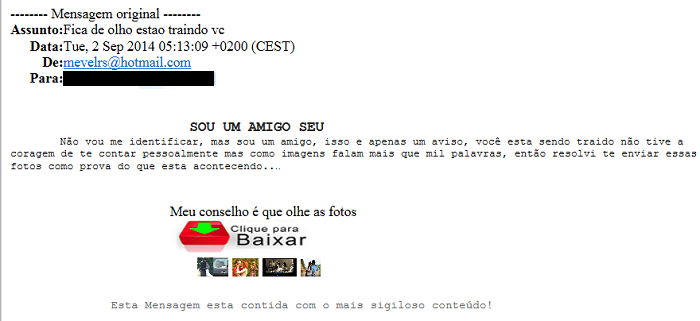
The attack starts with a malicious e-mail and a bit of social engineering, inviting you to click:
“I’m your friend and want to tell you you’re being cheated, look at the pics”
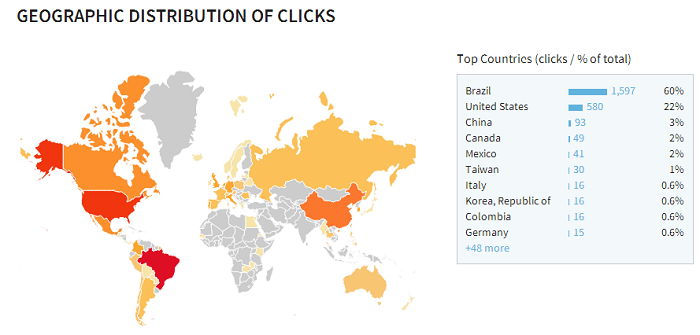
How many people believe in it? Well, many: 3.300 clicks in 3 days, with most of the users located in Brazil, US and China, probably Brazilians living there or people that understand Portuguese:
Shortened URLs are a cheap way for the bad guy measure their ‘performance’
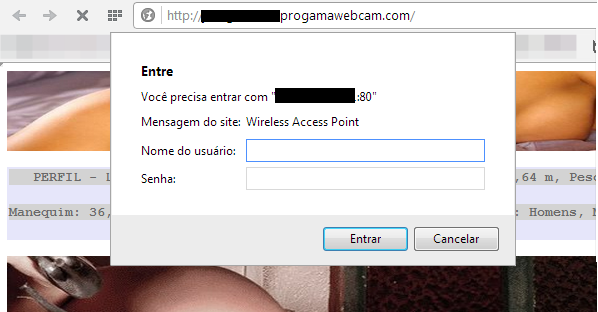
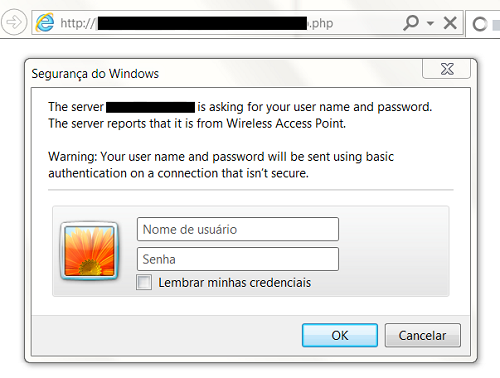
The website linked in the message is full of adult content, porn pics. While in the background it starts running scripts. Depending on your configuration, at some point the website may ask for the username and password of your wireless access point – if it has, this is a good thing. If not, this may be a problem for you:
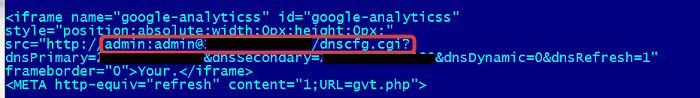
The script located in the website will try to guess the password of your home router. It tries several combinations such as “admin:admin”:
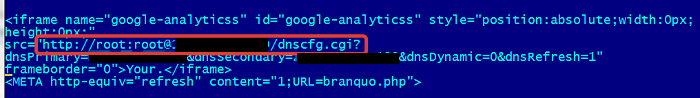
or “root:root”
or “admin:gvt12345” (GVT is a big Brazilian ISP):
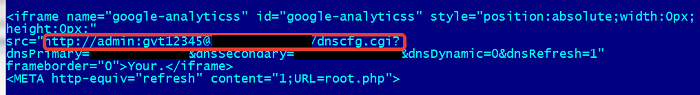
The scripts will continue trying combinations that point to the control panel of your network device such as [your-router-IP].rebootinfo.cgi or [your-router-IP].dnscfg.cgi?. Each script includes the commands to change the primary and secondary DNS servers. If you’re using default credentials in your home router, there won’t be an interaction and you’ll never realize that the attack has occurred. If you’re not using default credentials, then the website will pop up a prompt asking you to enter it manually.
We found Brazilian bad guys actively using 5 domains and 9 DNS servers – all of them hosting phishing pages for the biggest Brazilian Banks. The malicious websites used in the attacks are filtering direct access by using HTTP referrers, thus aiming to prevent direct access from security analysts.
So how do you protect yourself? Make sure you’re not using the default password in your home router and NEVER enter your credentials into any website asking for them. Our Kaspersky Internet Security is also prepared to block such scripts automatically.
Web-based attack targeting home routers, the Brazilian way




















Gerald Mead
I had this window come up on my screen just 4 days ago. My wifi was good but I lost internet service for a few minutes. I did not enter any info on the screen. I just closed the window and went about my business after my internet connection came back on. I have found no problems with my system.