
A year ago we released an article on Bluetooth technology which included data from research we had conducted. This article is a continuation, and includes the results of similar research which was conducted at the beginning of 2007.
I don’t know how many of you remember your first mobile phone. I do; in fact, it’s seven years old and I’ve still got it. It doesn’t have a camera, the display is monochrome, and of course it doesn’t have Bluetooth, but it still works.
It would be difficult to find a phone like that today. Many manufacturers equip even their cheapest models with Bluetooth, and Bluetooth is a standard in modern laptops. Bluetooth can also be found in music centers, home appliances, and even in cars.
The advantage of Bluetooth technology is that it’s cheap, easy to use, and wireless. However, as often happens when new technologies are being developed, not enough attention was paid to security issues.
The security of mobile devices is now a real issue. Malicious programs which spread via Bluetooth are no longer a rarity. For instance, worms for mobile devices which run Symbian, such as Cabir, Lasco and Comwar, all spread via Bluetooth. Data provided by Beeline, a leading mobile services provider in the Russian Federation, shows that 43 204 473 MMS messages were sent in the course of a year. Of these, 264 474 messages were infected, with 261 121 of them being infected by a Comwar variant.
It’s because the owners of mobile devices are on the move that malicious programs which propagate by Bluetooth can spread relatively fast. This in spite of the fairly restricted range of Bluetooth connections. The speed of propagation is also limited by the fact that specific types of malware are coded to infect specific types of mobile devices – if there’s no such device within range, then the malicious program will be unable to spread effectively.
Bluetooth security is also something which computer owners need to take seriously: Worm.OSX.Inqtana.a, a proof of concept worm for Mac OS X, also spreads via Bluetooth.
Further details about Bluetooth technology, potential threats, and types of attacks on Bluetooth enabled devices can be found in this article published last year. The article also includes research into vulnerable devices.
Last year’s research was repeated in order to find out if users of mobile devices have started taking the issue of Bluetooth security more seriously.
Equipment
Last time a Sony vaio fxa 53 laptop, with Linux SuSE 10.0 OSS, a PCMCIA Bluetooth adapter and btscanner 2.1 was used. This year, different equipment was used, but this did not impact on the final results.
This time scanning was conducted using a PDA (Zaurus 3200) with Linux installed. Varying distributions were tried, and finally pdaXrom was chosen. Of course, software is needed to scan for Bluetooth devices and btscanner 2.1 was used, as in the previous experiment.

A bluetooth scanner makes it possible to detect devices which are in ‘discoverable’ mode. Detecting devices which are not in discoverable mode is possible, but requires a different approach and different software.
I encountered a couple of problems: firstly, the btscanner version which comes with the 1.0 Linux distribution does not save the scan results, which is clearly no good for this type of research. This mean it was necessary to use a newer version. However, although everything could be compiled without problems, some errors came up due to linking. I fixed the first problem by adding the necessary sdp library to Makefile. It took a little longer to fix the second error; the new libraries meant new functions, and due to this, a newer version of the Bluetooth library was necessary.
Finally everything was working, and it was time to go. I tried to ensure that the conditions were the same as during last year’s research. The location was the same – one of Moscow’s large shopping malls – as well as the time spent scanning.
Results
The time put into choosing the equipment was repaid by ease of use: I had a mobile device which I could put in my pocket and carry around while I was doing other things. After a few hours I already had information about more than 200 devices. I repeated the experiment the following day; the result was data on approximately 500 devices.
The next task was to process the data. As all data was stored in standard text files, the use of a shell command was enough was enough to process them.
All in all mobile devices from 32 different manufacturers were found. However, the majority of devices could not be identified, which was somewhat disappointing. Additional steps had to be taken in order to identify them, and this was done using a file located at http://standards.ieee.org/regauth/oui/oui.txt.
Every Bluetooth device has a unique identifying address (BT_ADDR) which is composed of 6 bytes and which is usually in the MM:MM:MM:XX:XX:XX format, similar to MAC addresses. The first three bytes, designated by an M, contain information about the manufacturer of the microchip. The remaining three bytes contain information about the device model. Analyzing unique identifiers make it possible to determine the manufacturer. Unfortunately, the last three bytes aren’t so easy to analyze, and it’s impossible to determine the model 100%.
Manufacturers which were detected only a few times were united into a single category called ‘other’. This category contains devices which were detected four times or less in the course of the research.
Readers should remember that only devices that had Bluetooth enabled in discoverable mode were detected. (Because of this there are relatively few Motorola devices included in the results – even if in discoverable mode, such devices are only detectable for a short period of time). A device in discoverable mode means that the device can be detected, making it an easy target for remote malicious users. It is also possible to detect a device which is not in discoverable mode, but this is only possible by performing an exhaustive search, which will take significantly longer.
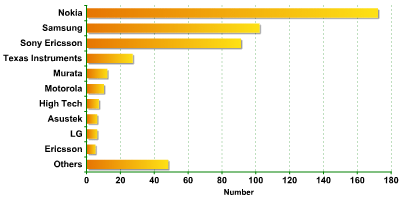
Mobile devices according to manufacturer
If we compare this year’s data with last year’s, two points stand out. The first is that Nokia, the leading device manufacturer last year, remains in the lead. However, Samsung is now in second place, having pushed Sony Ericsson into third place. Bluetooth headsets were detected in appreciable numbers this year, including headsets for cars. Additionally, PDAs and laptops have increased in number.
One useful figure when talking about security issues is the number of devices which are vulnerable to snarfing. Snarf is probably the best known Bluetooth attack. A successful snarf attack will enable a remote malicious user to get any file s/he wants from the victim device, includes the address book, the note book, photos, etc.
In 2007, the number of devices vulnerable to snarfing was noticeably fewer than in 2006: 25% (48 devices) and 4% (21 devices) respectively.
This decrease can partly be explained by the fact that developers are releasing new versions of software, and either they do not contain this vulnerability, or the vulnerability has not yet been identified. It should be noted that it’s the most popular devices, as previously, which are more vulnerable.
However, the results of our research show that users are still taking a laid-back approach to security, leaving their devices in discoverable mode, which could cause them to be targeted by malicious users.
Conclusions
-
- Bluetooth technology is becoming every more popular. Both the number of manufacturers using Bluetooth, and the number of models with Bluetooth increased over the course of a year.
- Security for mobile devices which use Bluetooth remains an issue. The growing popularity of this technology naturally attracts the attention of malicious users. Malicious programs can be spread via Bluetooth, and malicious users can exploit vulnerabilities to gain access to user data, and to conduct denial of service attacks.
- Unfortunately, the most popular devices also happen to be those which are most vulnerable.
- Manufacturers appear to be paying more attention to security issues.
- The number of devices detected increased in comparison to last year.
This leads us to the conclusion that users are not taking the issue of security seriously; devices retain their default configuration. The default configuration of discoverable mode and default PIN is less than ideal in terms of security.
There are a few simple recommendations which can make using Bluetooth equipped mobile devices more secure: installing antivirus protection, set the device in non discoverable mode, and enable authentification using a PIN code.





















War-nibbling 2007