
Sometimes ransomware developers make mistakes in their code. These mistakes could help victims regain access to their original files after a ransomware infection. This article is a short description of several errors, which were made by the WannaCry ransomware developers.
Errors in file removal logic
When Wannacry encrypts its victim’s files, it reads from the original file, encrypts the content and saves it into the file with extension “.WNCRYT”. After encryption it moves “.WNCRYT” into “.WNCRY” and deletes the original file. This deletion logic may vary depending on the location and properties of the victim’s files.
The files are located on the system drive:
- If the file is in an ‘important’ folder (from the malware developers’ point of view – e.g. Desktop and Documents), then the original file will be overwritten with random data before removal. In this case, unfortunately, there is no way to restore the original file content.
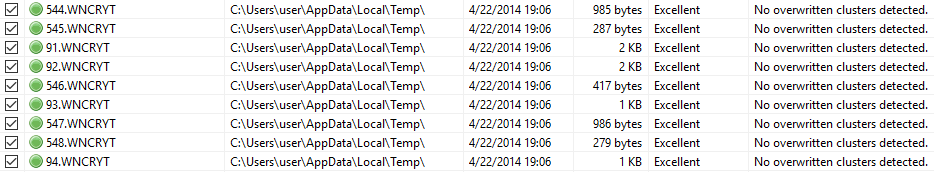
- If the file is stored outside of ‘important’ folders, then the original file will be moved to %TEMP%\%d.WNCRYT (where %d denotes a numeric value). These files contain the original data and are not overwritten, they are simply deleted from the disk, which means there is a high chance it will be possible to restore them using data recovery software.
Renamed original files that can be restored from %TEMP%
The files are located on other (non-system) drives:
- Ransomware creates the “$RECYCLE” folder and sets hidden+system attributes to this folder. This makes this folder invisible in Windows File Explorer if it has a default configuration. The malware intends to move the original files into this directory after encryption.
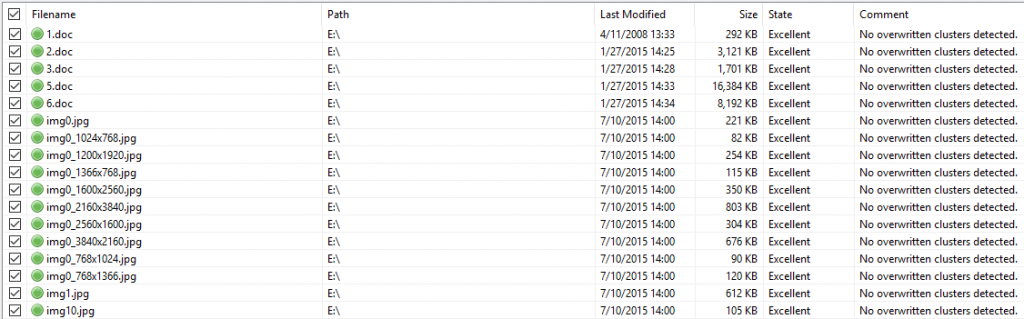
- However, because of synchronization errors in the ransomware code in many cases the original files stay in the same directory and are not moved into $RECYCLE.
- The original files are deleted in an unsecure way. This fact makes it possible to restore the deleted files using data recovery software.
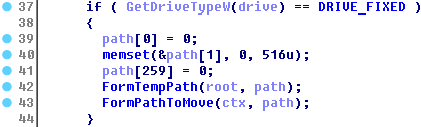
The procedure that determines the temporary directory to store original files before removal
Original files that can be restored the from a non-system drive
The procedure that constructs the temporary path for an original file
The piece of code calling the above procedures
Read-only files processing error
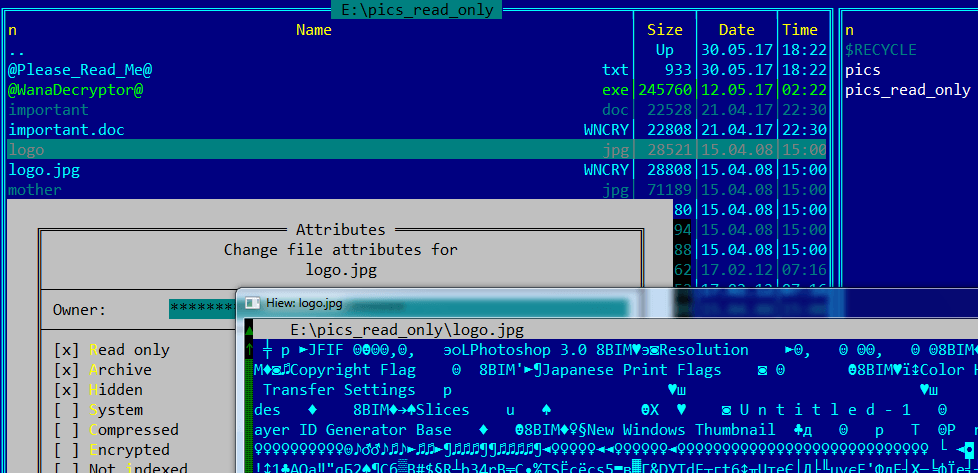
While analysing WannaCry, we also discovered that this ransomware has a bug in its read-only file processing. If there are such files on the infected machine, then the ransomware won’t encrypt them at all. It will only create an encrypted copy of each original file, while the original files themselves only get the “hidden” attribute. When this happens, it is simple to find them and restore their normal attributes.
Original read-only files are not encrypted and stay in the same place
Conclusions
From our in depth research into this ransomware, it is clear that the ransomware developers have made a lot of mistakes and, as we pointed out, the code quality is very low.
If you were infected with WannaCry ransomware there is a good possibility that you will be able to restore a lot of the files on the affected computer. To restore files, you can use the free utilities available for file recovery. We advise organizations share this article with their system administrators – as they can use the file recovery utilities on affected machines in their network.
WannaCry mistakes that can help you restore files after infection























Wunna Kyaw
Thankyou for your security.I Love Kaspersky Anti-Virus.
Gnaneshwar
nice tips.. thanks a lot for this interesting article.
peritam
is it realy possible to decrypt the wannacry encrypted files? i have lost almost 250000 files because f the attack of this dangerous malware
Erhard
fantastic…perfect
Shyam
Very informative
Chema
We published in Telefonica time ago to restore files using this tricks
http://blog.elevenpaths.com/2017/05/telefonica-wannacry-file-restorer-como.html