
On Monday we were among the first to announce the appearance of Gpcode.ai, the latest variant of the notorious ransomware Trojan.
All major antivirus vendors are now aware of this nasty program, covering it in news items and providing detailed descriptions. This can only be good.
However, reading the information issued by the different vendors is more entertaining than usual. My attention was piqued by the fact that av companies, in an effort not to disclose potentially dangerous information, ended up doing themselves and others a disservice. The industry is lacking a unified standard on what information should be published.
Let’s take a look at some examples.
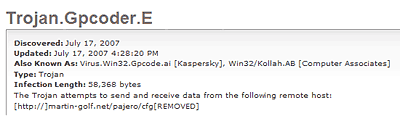
Symantec’s description includes information about a certain site that Gpcode uses for data exchange.
Why isn’t the complete URL shown? There’s a good reason for this. Av companies never give full links to sites which might contain malicious programs or which might include confidential data. This is why links in descriptions are partial, with [REMOVED] being used as a substitute for the deleted part of the link.
Now let’s take a look at Trend Micro’s description.
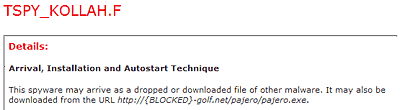
Trend analysts decided not to publish the full URL, which is great. But unfortunately they deleted one part of the link, and Symantec deleted another.
So – two different companies wanted to ensure this information was withheld, for the very best of reasons. But working together, they managed to make the information public…
A case, no doubt, of the road to hell being paved with good intentions, caused by the lack of a single, industry wide standard.
If we take a look at other examples, we’ll see what sort of data some antivirus companies try to mask, while others, apparently, aren’t bothered.
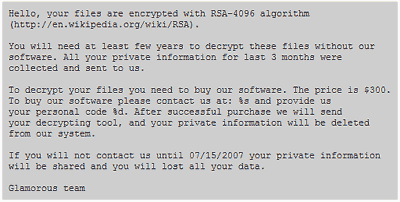
Here’s Trend again, with text from Gpcode’s “read_me.txt” file, which the Trojan drops to the victim machine. The author’s email address and victim’s personal code were replaced with %s and %d.
This is exactly what we did when we compiled our description of Gpcode.ai:
Clearly, in this case, Trend Micro and Kaspersky Lab were thinking along the same lines: not to publish this data.
So what did Panda Software decide to do?
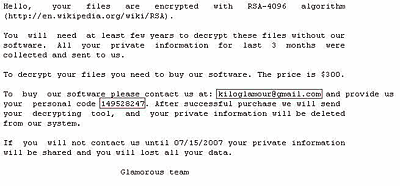
Not only did this company decide not to delete the crucial data, but actually highlighted it!
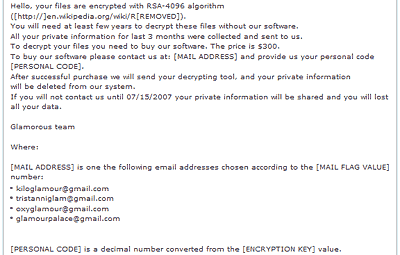
Symantec, having decided to mask data by substituting [MAIL ADDRESS] and [PERSONAL CODE] then decides to publish this information further down: 4 email addresses given for victims to contact…
In other words, it’s a real mess. And the crowning moment is also shown in the screenshot above, where Symantec analysts decided, for some reason, that the link to the Wikipedia article on RSA should be snipped!
No comment.





















Virus Descriptions 101