
A firewall provides security which is additional to that provided by other security solutions and appliances. Additional security is becoming increasingly relevant due to the increase in the number of new malicious programs. Firewalls block undesirable network traffic, both inbound and outbound. Leak tests, which are the subject of this article, evaluate how reliably a firewall controls outbound traffic and protects the computer from data leaks.
What is a firewall?
One function of today’s integrated security systems is enabling the user to control network traffic, i.e. data sent and received over the network by applications that are running on the user’s computer. A component that offers such control is called a firewall. There are software and hardware firewalls (http://en.wikipedia.org/wiki/Personal_firewall). This article only examines software firewalls.
There are a great many software firewalls available; some are commercial and some are free of charge. A firewall installed on a gateway (a server that transfers traffic between different networks) is called a server or network-level firewall. Firewalls installed on a user’s computer are called personal firewalls, as they only protect the computers on which they are installed. Personal firewalls are often incorporated in integrated security systems that protect personal computers. One example is the personal firewall in Kaspersky Internet Security 7.0.
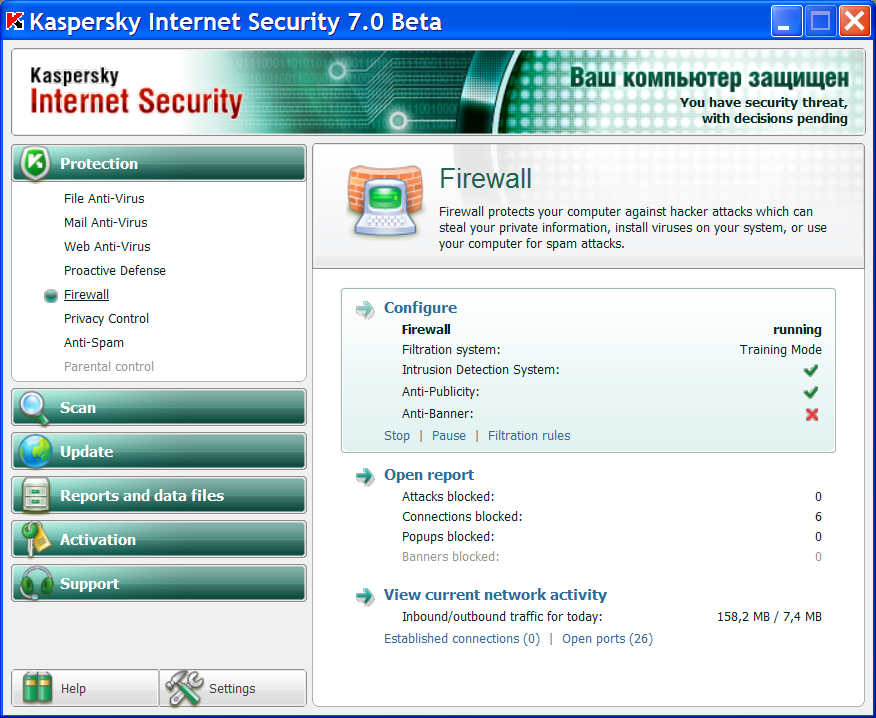
Figure 1. The firewall component in Kaspersky Internet Security 7.0
In order to perform their main function, i.e. control network activity, firewalls use lists of rules that define allowed or forbidden network activity for different applications. A rule can include a number of parameters, such as the direction of data transfer, data transfer protocol (IP, TCP, UDP, ICMP etc.), IP addresses and ports for local and remote computers that exchange data.
Any single rule for controlling network activity can apply to all applications in the system. In such cases case, it will be called a packet rule.
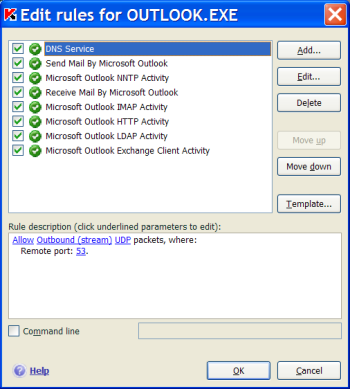
Figure 2. Examples of rules for Microsoft Outlook in Kaspersky Internet Security 7.0
Firewalls have two modes: interactive, (where user is prompted for action) or non-interactive. In non-interactive mode a firewall can:
- allow any activity that is not forbidden by the rules;
- block any activity that is not allowed by the rules; or
- block any network activity.
The basic operating mode for a firewall is interactive mode, which is also called training mode. In this mode, whenever the firewall detects network activity that is not covered by any of the previously defined rules, it displays a dialog window which prompts the user either to allow or block the activity on a one-off basis, or to create a rule for this type of network activity.

Figure 3. Dialog window displayed by Kaspersky Internet Security 7.0 firewall in training mode
Since the average user’s computer has dozens of applications which exhibit different types of network activity during operation, manually creating a list of rules to cover application network activity is a complex and lengthy task. Because of this, firewalls come with preinstalled rule databases for known network applications such as Internet Explorer, Microsoft Outlook, Generic Host Process for Win32 Services (svchost.exe), Microsoft Application Error Reporting (dwwin.exe) and many other applications.
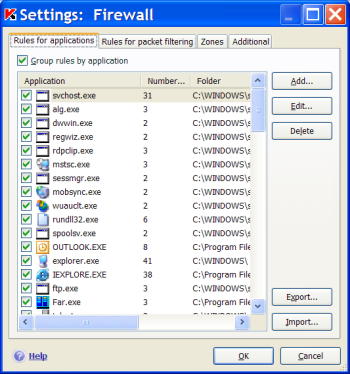
Figure 4. List of preinstalled application rules for the Kaspersky Internet Security 7.0 firewall
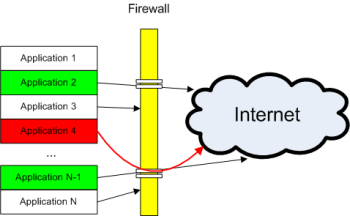
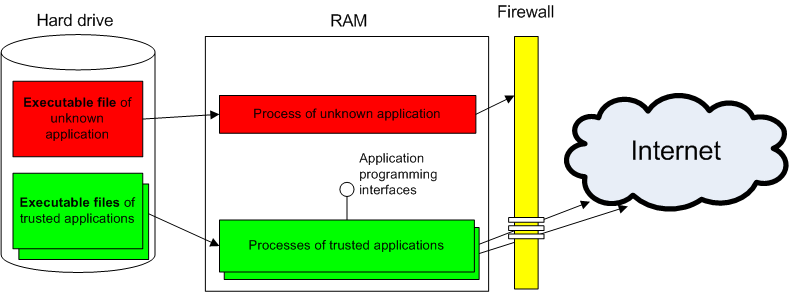
The diagram below shows how a firewall monitors outbound data and protects against data leakage:

Figure 5. How a firewall functions
A firewall establishes a ‘wall’ that separates applications on the user’s computer from other computers on the local network and on the Internet. For known (trusted) applications (shown in green on Figure 5), there are permission rules (‘holes’ in the ‘wall’) that allow these applications to transmit data to the outside world through the firewall. When any other application attempts to engage in network activity, this activity will be blocked (‘hit the wall’) and the application will not be able to transmit data to the outside world (or receive data from beyond the firewall). However, at any time the user can create new permission rules (make new ‘holes’ in the ‘wall’) to enable the application to exchange data over the network.
It should be noted that some firewalls also include an intrusion protection component, which provides protection from network attacks. This component scans inbound and outbound network traffic for network packets that match known network attack templates contained in a database. A future article will examine such components in detail.
How firewalls enhance security
Firewalls provide an additional layer of protection, which can help block malicious programs that are not detected by the antivirus component of an integrated security system. A malicious program may not be detected if it has not yet been added to the antivirus database (so it can’t be detected by traditional signature-based methods) and if the program does not exhibit clearly malicious or even suspicious behavior (so the behavior analysis component will not detect it, either).
What type of malicious programs can a firewall protect against? Virtually any malicious program that is currently in circulation. This may sound a very sweeping statement, but it is true: most of today’s malicious programs have functions which are linked to network activity and consequently they can be blocked by a firewall. For instance:
Network worms distribute copies of themselves via local networks/ the Internet.
Trojans, which currently make up 91.4% of all malicious programs, also exchange data via networks. Trojan programs include:
- Backdoors – these are utilities designed to provide remote administration of networked computers on the network. Backdoors are controlled remotely and a firewall can easily block all functionality of these malicious programs.
- PSW Trojans – these programs steal a variety of information from infected computers. After data has been stolen, the Trojan program needs to transmit the information to a cybercriminal. It’s at this stage that a firewall can block the program’s attempts to send data and in doing so, protect the user’s information.
- Trojan-Downloader programs – these programs download new versions of other malicious programs (Trojans and adware) and install them on the victim machine. Programs in this class exchange data over networks, and this can be easily blocked by a firewall.
- Trojan-Proxy programs – these programs gain anonymous access to various Internet resources without the user’s knowledge or consent. Such programs are mostly used to send spam. Like Trojan-Downloader programs, the network activity generated by Trojan-Proxy programs is easily blocked by a firewall.
- Trojan-Spy programs- as the name suggests, these programs can be used to spy on users of infected computers. Data, including information entered via the keyboard, screenshots, lists of active applications and user actions relating to these applications, is saved in a file on the hard drive and regularly sent to the cybercriminal. At this stage, the firewall can block attempts to send data which are made by an unknown program. This prevents user data stolen by the Trojan from reaching the remote malicious user.
It should be noted that firewalls cannot be used to combat classic viruses. This is because, unlike worms, viruses do not use network resources to penetrate other computers and, unlike Trojans, viruses do not need to send data or receive commands.
A firewall is a security system that is difficult to bypass. In order to circumvent antivirus and behavior blocker protection, the authors of malicious programs test their creations and modify them until both protection components fail to detect the malicious code. It is very difficult to bypass a firewall using this method. If a program generates some kind of network activity, it is very hard to hide this activity from the firewall. The only way of doing this is by using leaks.
What are leaks and leak tests?
Leaks are a technology for bypassing a firewall’s network activity control mechanisms, which enables applications that do not have permission rules in the firewall’s rule list to send data to recipients outside the network. The firewall does not prevent this data from being sent and does not inform the user of this network activity in training mode.
A well-designed firewall should not allow any leaks. It should be able to detect all attempted inbound and outbound network activity. This is why two criteria are used when analyzing the quality of protection provided by a firewall: the quality of inbound protection, i.e. protection against penetration from outside the network and the quality of outbound protection, i.e. protection against data leaks sent from the computer.
Various open port scanners (e.g., ShieldsUP! http://www.grc.com/default.htm, Quick test http://www.pcflank.com/test.htm etc.) are used to test the quality of protection against penetration from outside which the firewall provides.
In order to analyze how well a firewall protects against data leaks, leak tests are used. These are small non-malicious programs that implement one or more leaks. Such programs are mostly developed by security researchers and experts.
Clearly, the only way to set up a leak is to use existing ‘holes’ (i.e. permission rules) for known applications. However, this requires ‘persuading’ the firewall that the network activity has been initiated by a trusted application. There are a number of methods that can be used to achieve this. Before discussing these methods, let’s look at the basic principles of application execution in today’s operating systems.
Executing applications in contemporary operating systems
A computer’s CPU executes sets of instructions that are stored in the computer’s random-access memory (RAM). Sets of instructions are grouped into execution threads that belong to processes currently running in RAM.
Executable files contain sets of processor instructions, and when an executable file is launched, a new process appears in the system. A process can also be created programmatically by another process. The operating system maintains a process tree in RAM.
It should be noted that the address space of most processes in the system includes not only the code of the application’s executable file, but also the code of numerous dynamic-link libraries (DLL). Such libraries are used to store certain shared functions that are used by several applications. This allows developers to avoid duplicating the same program code in different executable files. The same library can be loaded in the address space of different processes.

Figure 7. Application execution
Classifying leak technologies
Setting up leaks
This section examines the technologies that a malicious application can use to ‘fool’ a firewall. Figure 8 illustrates the basic idea, with processes of trusted applications in RAM that are known to the firewall, as well as the process of an unknown (malicious) application.
An attempt by the unknown application to initiate network activity on its own behalf will be blocked by the firewall or cause the firewall to display a dialog window asking the user what action should be taken.
There are 3 main approaches to bypassing firewall protection:
- Deceive the firewall, i.e. ‘persuade’ it that the network activity is initiated by a trusted application. This is achieved by replacing the executable file of a trusted application on the hard drive or by substituting a trusted process’s data in RAM for the unknown process’s data.
- Execute code on behalf of a trusted application by injecting a DLL or a small part of the unknown application’s code into a trusted application’s address space. The firewall will not be able to distinguish between the network activity of such injected elements and the normal network activity of the trusted application.
- Use documented interfaces provided by trusted applications. When using such interfaces, the network activity will be initiated by trusted applications. However, it will be controlled by the untrusted application, allowing the application to transmit data via the interfaces to recipients outside the network without triggering firewall alerts.
There are six leak technologies that implement the three approaches described above:
| №№ | Idea 1 (deception) | Idea 2 (code execution on behalf of a trusted application) | Idea 3 (using documented interfaces) |
| 1 | Substitution | ||
| 2 | Launching | ||
| 3 | DLL injection | ||
| 4 | Code injection | ||
| 5 | Browser services | ||
| 6 | System services |
More detailed descriptions of these technologies and their possible implementations are given below.
Leak technologies
Substitution
Replacing the executable file of a trusted application on the hard drive or substituting a trusted process’s data in RAM for an unknown process’s data. The idea behind this method is to ‘persuade’ the firewall that the network activity was initiated by a trusted process.
There are three substitution methods:
- replacing the executable file of a trusted processes on the hard drive (implemented in the Runner leak test, see the Leak tests section);
- renaming an unknown application’s file with a trusted application’s file name (Leak test);
- substituting a trusted process’s data for the unknown process’s data in a process image loaded in RAM (Coat).
The diagram below illustrates the first type of substitution:

Figure 9. Substituting a trusted process file on the hard drive
Launching
Launching a trusted application with command line parameters. This method is based on the fact that most browsers accept the address of the web page to be opened as a command line parameter. If the web page includes a server side script (e.g. cgi), the address line can also include parameters that will be used by the script as input. These parameters can include confidential information, e.g. data stolen by a spyware program. Importantly, all network activity is generated by the browser as usual, so it will always be allowed in accordance with the firewall rules.
To prevent the user from noticing the browser window, the browser is usually launched in hidden mode (Ghost, TooLeaky, Wallbreaker [1]).
Malicious code can also launch the browser using other processes rather than launching it directly. For example:
- launch the browser using the shell process Windows Explorer.exe (Wallbreaker [2]);
- launch the browser using the shell process Windows Explorer.exe, which itself is launched using the command interpreter cmd.exe (Wallbreaker [3]);
- launch the browser using the Windows task scheduling mechanism (Wallbreaker[4]). In this case, the processes will be launched in the following sequence: AT.exe -> Svchost.exe-> Cmd.exe->Explorer.exe-> IExplore.exe.
This method is illustrated below:

Figure 10. Launching a trusted application with command line parameters
DLL injection
Injecting a dynamic link library into the address space of a trusted process. This method loads a malicious program’s dynamic link library into the address space of a trusted process. There are several ways of achieving this, but the principal methods are:
- installing a global hook. The hook code is located in the dynamic link library (CPILSuite [2,3], FireHole, pcAudit, pcAudit2);
- modifying the system registry value to add a dynamic link library to the list of DLLs that are automatically loaded by the system into each new process – the AppInit_DLLs key (Jumper).
It should be noted that both methods are documented and do have legitimate uses.
This method is illustrated below:

Figure 11. Injecting a dynamic link library into a trusted process
Code injection
Injecting code into the address space of a trusted process without using a dynamic link library. This method injects executable code into the address space of a trusted process. After injection, this code can initiate any network activity, since the firewall will regard it as activity by the trusted application. Unlike the DLL injection method, the legitimacy of this operation is doubtful, although documented methods for injecting code into other applications’ processes do exist. Such code injection is sometimes used by legitimate programs (e.g. debuggers), but is mostly used by malicious software.
There are numerous methods for injecting code into other applications’ processes. A number of examples are given below:
- loading a trusted process into RAM and patching the process’s memory (AWFT [1], CPIL, DNStest). This can be preceded by an attempt to avoid detection of this operation by the firewall by disabling firewall hooks (CPILSuite[1]);
- locating a trusted process in RAM and injecting code into it (Thermite);
- loading a trusted process into RAM and creating a remote thread in it (AWFT [2,3]);
- loading a trusted process into RAM, creating a remote thread in it, loading one more trusted process from this thread and patching its memory prior to execution (AWFT [4,5,6]);
- using the SetThreadContext function to gain control over a thread in a trusted process (CopyCat).
The processes most often attacked are those of Internet browsers (Internet Explorer etc. – AWFT [1,2,4], CopyCat and Thermite tests), the operating system shell (explorer.exe – AWFT [3,4], CPIL and CPILSuite [1]) and the svchost.exe process, which is the main process for Windows services loaded from dynamic link libraries (the DNStest test).
This method is shown in the diagram below:

Figure 12. Injecting malicious code into a trusted process
Browser Services
Using program interfaces to control an Internet browser. This method exploits various mechanisms in Windows designed to facilitate interaction between the processes of different components / applications. These mechanisms include:
- sending Windows messages to the Internet browser window. This changes the value in the browser’s address line, and pressing the Go button redirects the browser to the address inserted (Breakout);
- using the browser’s DDE interface, i.e., the Dynamic Data Exchange mechanism (http://en.wikipedia.org/wiki/Dynamic_Data_Exchange). The DDE library was developed to extend the capabilities of the Windows messages system, enabling two applications to dynamically exchange data during execution (DDE support in different versions of Internet Explorer is described in an article at http://support.microsoft.com/kb/q160957) (Surfer, ZAbypass, WB [1,3,4]; CPILSuite [3]);
- using the browser as an automation server (the OLE automation mechanism based on the COM model, http://en.wikipedia.org/wiki/Object_Linking_and_Embedding, http://en.wikipedia.org/wiki/Component_object_model). OLE automation is an extension of the DDE technology. Any modern browser provides a COM interface (http://en.wikipedia.org/wiki/Component_object_model) that can be used by other programs as an automation server. There are two Microsoft Internet Explorer COM components in external applications (http://msdn2.microsoft.com/en-us/library/aa741313.aspx):
- WebBrowser Control, implemented in shdocvw.dll (OSfwbypass),
- the MSHTML interface implemented in mshtml.dll (PCFlank).
This method is shown in the diagram below:

Figure 13. Using program interfaces to control the browserSystem services
Using program interfaces provided by system services. This method is similar to the method discussed above. The difference is that the program interfaces that are used are provided by operating system components rather than an Internet browser. Windows XP and Windows Vista have at least three such interfaces:
- BITS (Background Intelligent Transfer Service, http://msdn2.microsoft.com/en-us/library/Aa362827.aspx) – this is an intelligent file downloading service is used by Windows Update and Windows Server Update Services. It allows patches and updates to be downloaded in the background, without overloading communications channels. It also automatically resumes downloads if the connection is lost (BITSTester);
- Windows DNS API functions (http://msdn2.microsoft.com/en-us/library/ms682100.aspx) can be used to make a recursive DNS query to an Internet name server. Additional data, including confidential user data, can be sent as part of a DNS packet. A cybercriminal controlling a name server that processes DNS queries can obtain this information by processing this specially crafted DNS packet (DNStester);
- the interface for managing Windows desktop elements and wallpaper (IActiveDesktop, http://msdn2.microsoft.com/en-us/library/ms647199.aspx) can be used to set an HTML page as desktop wallpaper once Windows Active Desktop has been activated. The HTML page can include elements that link to external resources, resulting in these resources being loaded when new desktop wallpaper is activated (Breakout2).
Variations in existing leak classifications
It should be noted that the classification above differs slightly from leak technology classifications on dedicated leak analysis websites.
To our knowledge, the first website to publish systematic research of leaks was http://www.firewallleaktester.com. The classification is available at http://www.firewallleaktester.com/categories.htm.
In 2006, another site, http://www.matousec.com, appeared. One major project is Windows Personal Firewall Analysis (http://www.matousec.com/projects/windows-personal-firewall-analysis/introduction-firewall-leak-testing.php). The classification of leaks used in this research is similar to that used on http://www.firewallleaktester.com, but there are some differences.
The variation in classifications is examined below. The classification used in this article does not include the following methods:
№№ Method according to www.firewallleaktester.com Method according to www.matousec.com 1 Hidden rules Default Rules 2 Direct network interface use Own Protocol Driver 3 Timing attack 4 Recursive requests 5 Registry injection 6 Methodensammlung Windows Messaging + OLE Windows Messages und OLE Automation, DDE 7 Unhooking These methods are not included in our classification for the following reasons:
- The hidden rules method is not, in itself, a leak (see the definition of a leak above), since it does not implement any technology which bypasses the firewall’s mechanism for controlling network activity. It checks the set of packet rules (applied to all the applications in the system) that is used by the firewall by default. If one of the network ports is open for all applications, it can also be used by a malicious application to send data to recipients outside the network.
- The Direct network interface use method bypasses the network traffic filtration mechanisms at a ‘low’ level. This method creates an alternative stack of network drivers that processes packets coming from the network adapter in parallel with system stacks (TCP/IP etc.) This method is not included in our classification because there are currently no implementations (leak tests) that run under contemporary operating systems, i.e. Windows XP/Vista. Furthermore, it is unlikely that new leak tests (or, for that matter, malicious programs) utilizing this method will appear in the future, since it is much more complex than any other method which can be used to set up leak attacks. It should be noted, however, that there are three leak tests which work under the now obsolete Windows 9x and which use this leak method:
- MbTest (author: “mbcx8nlp”, 2003), uses the Winpcap library,
- Outbound (author: HackBusters, 2001),
- YALTA [2] (author: Soft4ever, 2001).
- The timing attack method is not categorized as a separate method in our classification. This is because at the moment virtually no firewall can be bypassed using the technology on which it is based (restarting its own process in order to change the PID, i.e. process identifier).
- In our classification, the recursive requests method falls under the System Services group.
- In our classification, the registry injection method is categorized as a variant of the DLL injection method, since the essence of this method is not in modifying the registry, but in injecting a dynamic link library into trusted processes. One way this can be achieved is by using a special registry key.
- In our classification, methods grouped under the Windows Messaging + OLE heading are placed in the Browser services and System services groups. We believe this to be more logical, since instead of describing the technical implementation (sending messages etc.), it reflects the essence of the leak technology at a higher level – using program interfaces to control the browser or using the operating system’s network services.
- Unhooking. This method is based on the following idea: in order to ensure protection from some leak technologies, firewalls use so-called hooks to intercept system functions. If these hooks are disabled (‘unhooked’), the firewall will be unable to combat leaks. This description clearly shows that this method is not a leak per se, and it is therefore not included in our leak classification. However, when used in combination with any ‘true’ leak method, it helps to verify how effectively the firewall protects from that leak method in difficult conditions, by simulating a situation in which malicious code actively blocks the firewall functionality.
The use of leaks in malicious programs
As recently as a few years ago, firewalls were rarely used to protect personal computers. Consequently, only a small number of malicious programs used leaks to bypass firewall protection. However, lately, malware writers have started using automation tools in order to create new variants of their malicious programs more quickly. Consequently, the number of malicious programs has been growing at an ever-increasing rate. As a result, tools that provide additional security for personal computers have gained in importance, with firewalls becoming increasingly popular.
Given that firewalls are becoming increasingly widespread, malware writers are now using leaks more actively to evade firewall protection. The table below gives examples of real malicious programs that use each of the 6 main leak methods.
№№ Method Malicious program Detection date Description 1 Substitution Backdoor.Win32.Bifrose.aer March 26, 2007 Replaces MSN Messenger (C:\Program Files\MSN Messenger\msnmsgr.exe) with a copy of itself 2 Trojan-Spy.Win32.Agent.se July 26, 2007 Launches Internet Explorer in a hidden window with the path to an HTML file in the command line 3 DLL injection Trojan-Spy.Win32.Goldun.pq June 11, 2007 Registers a DLL in the AppInit_DLLs registry key and uses it to intercept Internet traffic 4 Code injection Trojan-Spy.Win32.Delf.uc January 19, 2007 Creates a thread in the winlogon.exe process and uses this thread to send data to the Internet 5 Browser services Trojan-PSW.Win32.LdPinch.bix January 4, 2007 Uses the IWebBrowser2 COM interface to send harvested data 6 System services Trojan-Downloader.Win32.Nurech.br June 8, 2007 Uses the BITS system service to send user identification data (disk serial number) over the Internet It should be noted that different types of leak are suited for different purposes and are used in malicious programs to achieve different objectives. Specifically:
- Only a limited range of data can be sent using browser command-line parameters, while a malicious program can use the BITS technology to upload very large files from the user’s computer.
- Methods based on injecting a DLL or code into trusted processes are also employed for purposes other than getting round firewalls, since they can be used not only to send data on behalf of a trusted process without the user’s knowledge, but also to perform a range of other operations.
- Browser control interfaces (e.g., WebBrowser control) can be used not only to send data on behalf of Internet Explorer, but also to control the running copy of the browser (e.g. close all windows in which the page address does not satisfy certain conditions), modify the document loaded in the browser, display message windows in the browser, etc.
Leak tests
The table below lists current leak tests and the leak methods which they test. Most of the tests listed can be downloaded from http://www.matousec.com/projects/windows-personal-firewall-analysis/introduction-firewall-leak-testing.php or http://www.firewallleaktester.com.
№№ Name Author Method Year 1 AWFT [6] Jos Pascoa Code injection 2005 2 BITSTester Tim Fish System services 2006 3 Breakout Volker Birk Browser services keine Angabe 4 Breakout2 Volker Birk System services keine Angabe 5 Coat David Matoušek Substitution 2006 6 CopyCat “Bugsbunny” Code injection keine Angabe 7 CPIL Comodo Code injection 2006 8.1 CPILSuite [1] Comodo Code injection + Launching 2006 8.2 CPILSuite [2] Comodo DLL injection + Launching 2006 8.3 CPILSuite [3] Comodo DLL injection + Browser services 2006 9 DNStest Jarkko Turkulainen Code injection 2004 10 DNStest Jarkko Turkulainen System services 2004 11 FireHole Robin Keir DLL injection 2002 12 FPR (38) David Matoušek [unhooking] keine Angabe 13 Ghost Guillaume Kaddouch Launching keine Angabe 14 Jumper Guillaume Kaddouch DLL injection 2006 15 LeakTest Steve Gibson Substitution 2002 16 OSfwbypass Debasis Mohanty Browser services 2005 17 pcAudit Internet Security Alliance DLL injection 2002 18 pcAudit2 Internet Security Alliance DLL injection keine Angabe 19 PCFlank www.pcflank.com Browser services 2006 20 Runner David Matoušek Substitution 2006 21 Surfer Jarkko Turkulainen Browser services 2004 22 Thermite Oliver Lavery Code injection 2003 23 TooLeaky Bob Sundling Launching 2001 24 Wallbreaker [4] Guillaume Kaddouch Launching 2004 25 YALTA Soft4ever [default rules] 2001 26 ZAbypass Debasis Mohanty Browser services 2005 The table below categorizes leak tests according to our classification:
№№ Technology Leak tests 1 Substitution Coat, LeakTest, Runner 2 Launching Ghost, TooLeaky, Wallbreaker 3 DLL injection CPILSuite [2, 3], FireHole, Jumper, pcAudit, pcAudit2 4 Code injection AWFT, CopyCat, CPIL, CPILSuite [1], DNStest, Thermite 5 Browser services Breakout, OSfwbypass, PCFlank, Surfer, ZAbypass 6 System services BITSTester, Breakout2, DNStester The significance of leak test results
What are the benefits of comparative tests of firewalls which use leak tests? First and foremost, such testing helps to determine the integral quality of protection and the results can make choosing an integrated system to protect a computer easier.
When selecting protection, users often focus purely on characteristics such as detection rates and the speed of response to new threats (e.g. using test results such as those provided by http://www.av-comparatives.org and http://www.av-test.de). However, such parameters do not provide a comprehensive definition of the quality of protection. The quality of the proactive component included in antivirus solutions, the effectiveness with which infected computers are treated, the ability to combat active rootkits and the quality of self-protection provided by each product are other characteristics that are equally important, but authors of comparative tests do not give sufficient weight to such factors. When selecting an integrated security product, additional components, such as an anti-spam system and a firewall, should also be analyzed.
As mentioned above, there are two criteria when assessing the quality of protection provided by a firewall: the control of inbound data and control of outbound data. Good performance in outbound data control tests means that the firewall is not simply a ‘makeweight’ component in an antivirus product but that it does provide an additional level of protection which can prevent the user’s confidential data from being sent to cybercriminals, even if the antivirus components fail to block a Trojan program.
We believe that the products which received Very Good and Excellent ratings in the leak tests conducted by http://www.matousec.com/projects/windows-personal-firewall-analysis/leak-tests-results.php provide users with sufficient protection. If protection provided by a product is rated Good or, even worse, Poor or Very Poor, it means that malicious program writers will be able to bypass the firewall included in the product using virtually any method.
Conclusion
Today, a firewall is an indispensable component in integrated IT security systems. Even the latest operating systems, such as Windows Vista, cannot block all types of leaks on their own (although, from Windows XP SP2 onwards, Windows has included a firewall. Firewall functionality was significantly expanded in Windows Vista).
According to the results of testing conducted in March 2007 by Guillaume Kaddouch (http://www.firewallleaktester.com/articles/vista_and_leaktests.html), Windows Vista Ultimate 64-bit using default settings blocked only 9 leak tests (the leak tests blocked are shown in green in the results table).
№№ Name Notes 1 Substitution Coat, LeakTest, Runner 2 Launching Ghost, TooLeaky, Wallbreaker 3 DLL injection CPILSuite [2, 3], FireHole, Jumper, pcAudit, pcAudit2 4 Code injection AWFT, CopyCat, CPIL, CPILSuite [1], DNStest, Thermite 5 Browser services Breakout, OSfwbypass, PCFlank, Surfer, ZAbypass 6 System services BITSTester, Breakout2, DNStester The new operating system is clearly better protected than previous versions thanks to numerous improvements, including UAC, IE protected mode, Service hardening and Kernel Patch Protection (Vista x64). However, even Windows Vista requires third-party protection programs to provide the necessary level of protection from leaks.
In the future, malicious programs will implement new methods in order to bypass protection mechanisms in the new operating system as well as existing protection mechanisms. This is why the importance of the firewall as an additional level of protection will only increase. Clearly, malware writers will increasingly use leak technologies to bypass firewalls. This means that leak tests will become a crucial method for testing the reliability of a computer’s protection.




















Using leak tests to evaluate firewall effectiveness