
Regular readers of this blog and our analytical articles may remember that in summer last year we wrote about a new variant of Bancos.aam designed to steal data from users of QUIK, a Russian Internet trading system.
Russian reports on the ongoing investigation say the suspect, one Evgeny Simonov from Yoshkar-Ola, is currently not permitted to leave the city. He used the Trojan to steal a broker’s log-in and password and then illegally made at least 2.5 million roubles (around a hundred thousand dollars) on fraudulent trades.
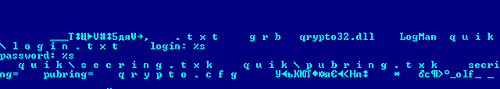
Simonov clearly saw the opportunity to turn a quick buck. But he slipped by making deals via his mobile: the investigators checked when the fraudulent deals were made, and the originating IP address, and traced Simonov via his mobile operator.
The whole case throws up an interesting point: new technologies and increased connectivity provide malware writers with increased opportunities, but the same technologies can also be used against them.






















Turning a QUIK buck