
The year 2007 can be dubbed “the year of online-world fraud” or perhaps “the year of exploiting poor gamers”. And with good reason: the evolution of malicious programs targeting online game players made a giant leap forward during the year. In terms of diversity and the extent to which they have spread, such programs already rival worms and viruses that cause epidemics (see Online Scanner Top Twenty for November 2007). In terms of complexity they are on a par with the most sophisticated malware designed to build zombie networks (see Online Games and Fraud).
In 2007, the number of malicious programs which only target online game players increased by 145% from 2006, continuing the existing trend for exponential growth. This is in line with the overall situation with theft of virtual online property.

Number of malicious programs that steal online game passwords, by year
A more detailed analysis of the increase in the number of malicious programs targeting online games can be provided by dividing all such malicious programs into TrojWare and VirWare categories.
TrojWare: gaming Trojans
Among malicious programs targeting online game players, the share of Trojans (i.e. malicious programs which are solely designed to steal passwords) is as high as 96%.
The most prominent representatives include:
- Trojan-PSW.Win32.OnlineGames,
- Trojan-PSW.Win32.Lmir,
- Trojan-PSW.Win32.Nilage,
- Trojan-PSW.Win32.WOW,
- Trojan-PSW.Win32.Magania,
- Trojan-PSW.Win32.Gamec,
- Trojan-PSW.Win32.Tibia,
- Trojan-PSW.Win32.Hangame.
Among new Trojan programs designed to steal confidential information (i.e. PSW Trojans), the share of gaming Trojans was 69.8% for the entire year. Significantly, gaming Trojans keep increasing their share: while in January it was about 65%, in September it exceeded 75% and rose above 80% by the year’s end. It can be concluded with certainty that online game passwords are of much greater interest to cybercriminals than email, instant messaging or online banking passwords.

Proportion of Trojans targeting online games to all Trojans that steal confidential data (Trojan-PSW) (by month 2007)
Comparing the code of different gaming Trojans leads to the conclusion that 2006 and the first half of 2007 were a period for testing new technologies for stealing passwords, keys and other data that enable cybercriminals to perform any operation with other people’s virtual property. In the second half of 2007, these technologies, already tried and tested, were further developed in response to new patches released by online game developers or modified to prevent detection by antivirus programs.
The rapid growth in the number of new Trojans in the beginning of 2007 and the slowdown at the end of the year, combined with the absence of new technologies, also confirms that the methods for stealing game characters and virtual property had reached an appropriate level of sophistication by the second half of the year.

Number of malicious programs (TrojWare)
stealing online game passwords (by month 2007)
The decline in the number of new gaming Trojans in July can be attributed to the traditional summer vacation period and to the reduced frequency of updates provided to online game customers. Under such conditions, cybercriminals do not need a large number of new Trojans, since the effective life of the old ones is extended.
As for which direction gaming Trojans are developing in, 2007 was a year of transition – from Trojans targeting individual games to malware designed to steal passwords to several games at once.

Number of Trojans designed to steal passwords to several games, compared to the number of Trojans targeting individual games (by months of 2007)
In terms of the number of new programs, the most numerous family of 2007 was Trojan-PSW.Win32.OnlineGames, whose members hunt for passwords for several online games at once (the number of targeted games varies between two and ten).

Most numerous gaming Trojan families in 2007
It can be determined how popular different online games are among authors of Trojan programs by estimating the share of each Trojan targeting a specific online game among all gaming Trojans.

Share of Trojans targeting specific online games among all gaming Trojans (by months of 2007)
The diagram above shows that the popularity of Lineage 2 (targeted by Trojan-PSW.Win32.Nilage) among authors of Trojan programs declined throughout the year, while Gamania (targeted by Trojan-PSW.Win32.Magania) gained popularity in the second half of 2007. World of Warcraft demonstrated an enviable stability, with a surge of popularity in August (seemingly in connection with the Blizzcon convention).
We can use google.com/trends to assess the popularity of Lineage2 and World of Warcraft among online game players (the diagrams below show the number of links found by Google for the relevant queries).
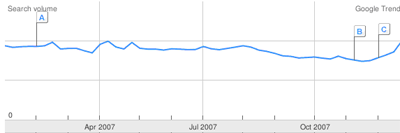
Results produced by google.com/trends for the query “lineage”
[http://www.google.com/trends?q=lineage&ctab=0]

Results produced by google.com/trends for the query “wow”
[http://www.google.com/trends?q=wow&ctab=0]
It can be seen from the diagrams that user interest in Lineage2 declined during the year, while World of Warcraft kept its ground. This demonstrates that there is a correlation between the popularity of online games among authors of Trojan programs and their popularity among users.
VirWare
Among all the malicious programs targeting online game players, the share of VirWare (i.e., self-propagating malware) is as small as 4%, but this category includes some infamous malicious programs:
- Worm.Win32.Viking,
- Worm.Win32.Fujack,
- Virus.Win32.Alman,
- Virus.Win32.Hala,
- Worm.Win32.AutoRun.
The share of gaming malware among all programs classified as VirWare changed over the course of the year.


Share of self-propagating malicious programs in all VirWare
which target online games (by month 2007)
The figure above demonstrates that in winter, when gamer activity is at its highest, approximately every fifth self-propagating malicious program is one designed to steal online game passwords.
Virus writers were active in developing new game-oriented VirWare at the beginning and the end of 2007, as is shown below:

Number of self-propagating malicious programs (VirWare) that steal online game passwords (by month 2007)
The activity of developers of new gaming VirWare peaked again in July. The reason for this peak was one of the most effective gaming worms, Worm.Win32.AutoRun, which appeared that month. (Conversely, as was shown above, the number of new gaming Trojans sharply declined in July.)
The effectiveness of this worm is due to its method of propagation: it spreads via flash cards. Following a successful début, AutoRun has not lost its popularity. December’s peak of popularity reached by new online game-oriented VirWare was largely defined by this worm.
Conclusions
Online games have long since ceased to be something unusual or remarkable. They have become part of everyday life, like ICQ, email and mobile phones.
The evolution of malicious programs targeting online games in 2007 is a result of the evolution of online games and the gaming industry as a whole. Today, the theft of virtual property and game characters is a well-run business. While no universal algorithms for stealing online game passwords existed at the beginning of the year, such algorithms were available by the year’s end.
Currently, 8 to 9 new worms designed to steal online game passwords appear globally every day and 5 to 6 gaming Trojans appear every hour. Significantly, the sophistication of the newest generation of game-oriented malware is comparable to that of multi-purpose Trojans used to build zombie networks.
There is now a mature black market for online game valuables that is evolving according to the laws of economics. And virus writers are closely following its evolution.
The diagram below shows the number of links found by Google (google.com/trends) for the following queries: “sell account” (in blue), “buy account” (in red) and “hack account” (in yellow).

Result produced by google.com/trends for query “sell account, buy account, hack account”
[http://www.google.com/trends?q=sell+account%2C+buy+account%2C+hack+account&ctab=0&geo=all&date=all&sort=0]
This diagram sheds light on the relative popularity of these topics. Since the lion’s share of offers to buy or sell an account is online game-related, it can be concluded that demand exceeds supply in the market for online game valuables. And the fact that the growth in popularity of account sale and purchase queries coincides with that of the account hacking query (with a clear peak in summer on all three curves) demonstrates that this market is highly criminalized.
Since the number of people wishing to buy game characters or virtual currency or property is constantly increasing, the market will continue to expand. This in turn means that virus writers are not going to lose their interest in online games any time soon, and the evolution of malicious programs targeting online game players will continue. Malware writers will pay closer attention to the self-protection of malware targeting online games and will integrate the password-stealing functionality that they have developed into malicious programs with other types of behavior, e.g., backdoors.






















Trend of the year: the evolution of malicious programs targeting players of online games