
Year-End Overview
- The average percentage of spam in email traffic amounted to 79%.
- Most spam sent to Russian Internet users originated in Russia, the US and Poland.
- The share of graphical spam declined over the past year.
- Spammers continued to experiment with spam format but these experiments were not very successful.
- The leading spam category in 2007 was advertising for Viagra and other medications, health related goods and services.
- Spammers actively used the Russian Internet for pre-election political advertising.
Kaspersky Lab receives and analyzes approximately 2,000,000 spam messages per day, and sometimes as many as up to 3,000,000. The spam comes from a range of sources, including dedicated spam traps, and it is also submitted by partners and commercial users. This means that spam analysts see a full cross section of varying types of spam. All incoming spam traffic is automatically classified. Some incoming spam is also analyzed manually. Kaspersky Lab’s one-of-a-kind spam classification system helps track spam volume and the different categories of spam.
- Malware evolution in 2007
- Trend of the year: the evolution of malicious programs targeting players of online games
- Spam report
- Malware which spreads via email
Legislation and spam
On 26th January 2007, a law called ‘Concerning Personal Data’ was adopted in Russia. This law, in part, is designed to regulate the sending of advertising material and campaign materials by email. The law includes the following point:
“The processing of personal data for the purpose of the market promotion of goods, work and services by means of making direct contact with a potential consumer with the aid of communication facilities, and for purposes of political campaigning, shall be permitted only on condition of the prior consent of the subject of the personal data. Such processing of personal data shall be deemed to be carried out without the prior consent of the subject of the personal data unless the controller is able to prove that such consent was obtained.”
“Concerning Personal Data”, Article 15, point 1.
This legislation echoes a previously passed law, ‘On Advertising’ (in the version of 1st July 2006):
“The distribution of advertising through telecommunications networks, including through the use of telephone, facsimile and mobile telephone communications, shall be permitted only on condition of the prior consent of the subscriber or addressee to receive the advertising. In this respect, advertising shall be considered to have been distributed without the prior consent of the subscriber or addressee unless the advertising distributor is able to prove that such consent was obtained. The advertising distributor shall be obliged immediately to terminate the distribution of advertising which is targeted at a person who has requested such termination.”
“On Advertising” Article 18, point 1.
In both cases, the law specifies the need to have preliminary agreement from the recipient – in Europe and the USA this is called an opt-in. It should be noted that opt-in is not required by legislation in many European countries; consequently it could be stated that Russia is taking a fairly harsh legislative line on spam. Unfortunately, however, the severity of Russian law is compensated for by the fact that there is no obligation to oblige by the law. This has once again been made clear – the ‘Concerning Personal Data’ law has been in force for nearly a year now, but the volume of spam has not diminished. On the contrary, statistics show that the volume of spam is continuing to increase.
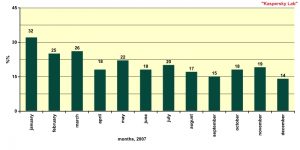
Share of spam in mail traffic
Distribution of spam on the Russian Internet, 2007
Last year spam represented at least 79.2% of all mail traffic. The lowest figure (73.5%) was recorded in May, while the yearly high (86.2%) was recorded in November. The share of spam in mail traffic gradually increased over the year (with a few fluctuations). By autumn it exceeded 80% and in the 4th quarter of 2007 it amounted to 85.7%.
It should be noted that although the share of spam in mail traffic rose from 76% in the first six months to 82% by the end of the year, the volume of spam doubled over the past year. This huge growth was caused by an increase in the number of email users, in the total quantity of messages they sent and also in the number of infected machines used for sending out spam. The more Internet users there are, the more computers will become part of botnets, which in turn leads to more spam being sent.
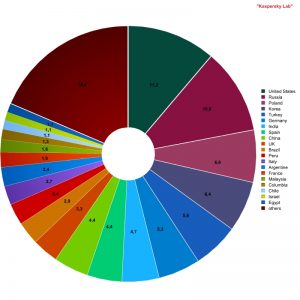
Where does spam come from?
Sources of spam by country
Both the US and Russia are still the world’s leading sources of spam. In 2006 China came third in the rating. But in 2007 it ranked only in ninth place. It seems that Chinese users have begun paying more attention to IT security as it relates to their machines. China was replaced by Poland in third place; this country has been among the top five for several years now.
Interestingly, the lower half of the Top 20 was dominated by Latin American countries.
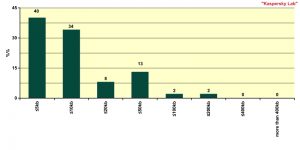
Size of spam emails
Approximately 40% of spam emails do not exceed 5 KB in size. These are emails which contain a short message and a link. Another third of spam emails range from 5KB – 10KB in size, and these contain messages with advertising text or messages with additional random text used to evade spam filters.
Hence, the vast majority of spam emails (70%) contain a short text and a link. Spammers prefer to send emails which are less than 10 KB in size. The reason for this is obvious: the short each individual message, the quicker the mass mailing will reach end users’ machines.
Another peak on the graph (13%) is caused by those spam emails which range from 20KB to 50 KB. This category includes graphical spam and spam messages with attachments (.pdf, .fdf) which was relatively widely used in the middle of the year (see below more information on this).
Spammer Technologies in 2007
Graphical Spam
Graphical spam is spam messages with graphical attachments. At the beginning of 2007, spammers were continuing to experiment with the graphical spam which had been so popular in 2006.
In February spammers again turned to using animated spam: the text of advertisements was split into frames, with each frame displaying 1-2 lines of the advertisement. The frames were then layered over each other, with the end result being a complete text. Spammers perfected the technology used to rotate the elements in each frame at different angles, resulting in even more ‘background noise’. As a result the text (in the form of an image) became extremely difficult to read, once again making animated spam a dead end.
Below are some examples of animated spam containing elements rotated through different angles (the final image is made up of four different frames):

Spam consisting of four separate frames
By spring 2007, anti-spam developers had become well able to filter out graphical spam and spammers had to look for the new ways to deliver the same information in graphical form.
In March a new type of spam appeared. Such messages contained a URL which lead to a free hosting page for images (imageshack.us, imagenerd.com, imgnation.net, hostpic.biz, imgplace.com etc.). Generally, graphical files were not attached to such messages. They were located on an external resource (usually free) and the message contained a link to this resource. When such messages were opened, the image was automatically downloaded. Another tactic was to use an image as background. The URL where the image was located would be placed within a ‘body’ tag with a ‘background’ attribute. As a result, the image would be automatically loaded in certain mail clients, and also via certain web-mail services. In neither case was the graphical spam sent as a message attachment, and consequently, there was nothing for spam filters to analyze. However these tricks were not successful and spammers switched to experimenting with the format of attached files.
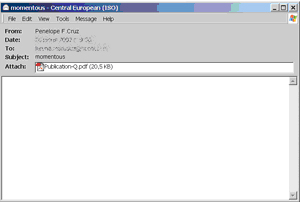
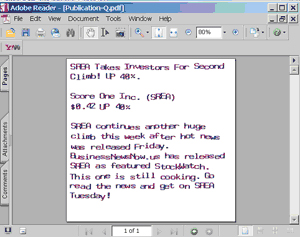
One innovation in May was PDF spam. Users received blank emails with .pdf format (and later .fdf format) attachments. Users did not expect this type of spam, so they opened the attachments and found all too familiar advertising texts.
This is the spam email:
And here is what’s in the attachment:
At first this type of spam successfully evaded spam filters, and it made up a relative high percentage of the overall volume of spam – at its peak this figure was close to 10%. But spam filters quickly learned to detect such attachments. Spammers attempted to change the format of attachments from .pdf to .fdf. But filters successfully recognized the new type of spam and by the end of July this method had come to a dead end.
Spammers also tried to send out messages with archive attachments and Excel files; such messages were designed to target users who are used to Office application files. In both cases this approach failed because the majority of users exercised a measure of caution when receiving unexpected emails and did not open the attachments.
Share of graphical spam in the total amount of spam
As the graph shows, the share of graphical spam in the total amount of spam declined after spammers had experimented with it. However, it is still relatively high. There are certain categories of spam which traditionally use images in their advertising (for example, Viagra and other medications), so spammers will most likely continue experimenting with graphical spam.
Mp3-spam
In 2007 a completely new spam format – mails with attached mp3-files – was introduced. Spammers were sure neither spam filters nor users would be expecting spam in such a format, and that the messages would reach their target.
However the use of this new format turned out not to be a viable tactic. In order to evade spam filters, the spammers changed the content of the sound files. Each file contained several text elements (which were probably automatically generated), which were not always in the same order, and which were recorded at different speeds. As a result, the mp3 files could barely be listened to. Additionally, the files were very small in size and this had an effect on the quality of the recording.
Flash mailings
In August 2007 spammers started speeding up their mass mailings, resulting in flash mailings. Standard mass mailings took about two days, while flash mailings, which used improved spamming software and an increased number of computers to mail messages, resulted in messages reaching millions of users in a mere 15-30 minutes.
This increased speed has cut the time spammers need to get their messages out: now it takes less than 30 minutes. But spam filters have learned to combat this type of spam. Kaspersky Lab for example uses a new technology, SURBL, which responds to spam immediately. Consequently spammers will have to think of some new methods if they wish their messages to reach end users.
Spam and social networks
Given the effective filtration of messages in mail traffic, spammers have had to look for other distribution vectors. They track Internet trends and the interests of their potential clients.
In days gone by, users were members of a range of forums and spam came in the form of forum notifications. Today’s latest fad is social networks and spammers haven’t hesitated to use this for their own ends. Messages containing links to web sites which are probably hosting malware now appear to come from the most well-known social networking sites. One example is the spam allegedly sent by the support service at ‘Odnoklassniki’ (the Russian equivalent of ‘Friends Reunited’), a site which is currently extremely popular in Russia. The email states that a user has tried to friend the recipient, who is asked to respond by clicking on the link in the body of the message.
Social networks will continue to be popular and spammers will actively use them. Spam in the guise of notifications from such sites simulating message notifications will become more realistic and qualitative. In addition spammers will try to spread spam messages from legitimate accounts registered on social networks (the same way they did with forums). Social networks are already making attempts to resist these attacks (for example, some social networks have imposed restrictions on the number of invitations per day), but spammers will no doubt find the way to evade this protection.
Spam by category
Top spam categories in 2007:
| Category | Main subgroups | %% | |
| 1 | Medications and health-related products and services | Viagra, Cialis and other pills | 23.3% |
| 2 | Education | Seminars and training courses | 11.7% |
| 3 | Computers and the Internet | Cheap software and printer cartridges | 8.7% |
| 4 | Travel and tourism | Package holidays etc. | 8.1% |
| 5 | Electronic advertising services | Spam mailings and address databases | 7.2% |

Spam by category on the Russian Internet in 2007

Spam by category in 2006 and 2007
Like last year, in 2007 the leader was “Medications and health-related products and services” category. This category not only maintained its leading position but increased its percentage which by the end of the year amounted to 23.3% (7.3% higher than in 2006). The lion’s share of spam in this category is advertising for Viagra and similar medications. Spammers have been sending such spam for several years and will probably continue to do so.

Share of “Medications and health-related products and services” category
in the total amount of spam
The top five categories include “Education” (11.7%) and “Computers and the Internet” (8.7%) coming second and third respectively. Russian language “Education” spam is mostly represented by advertisements for seminars and training courses, while English-language spam in this category offers higher education diplomas and degrees. The category “Computers and the Internet” is mostly made up of English-language messages advertising fake, ‘grey’ or pirate software. On the Russian Internet, spam in this category also offers consumables, for example printer cartridges.
The “Electronic advertising services” category (spammers’ self-advertisement) ranks fifth. This is not particularly reassuring news; this type of spam on the Russian Internet is represented mainly by Russian-language messages, in relatively large amounts. This means that despite all the Russian antispam legislation, spammers are actively looking for new clients.
One encouraging fact: the “Financial spam” and “Computer fraud” categories have slipped out of the Top Five. This is discussed in more detail below.
Computer fraud
The category “Computer fraud” includes phishing messages and other spam used by cyber criminals to get money out of users, for example, 419 scam emails or spam which informs the recipient that he/she has won a prize in a lottery etc.
At year-end the share of fraud messages in the total amount of spam was 6.9%, almost twice less than in 2007. However, despite these apparently reassuring figures, computer fraud has actually become more of a threat, as cyber criminals hone their skills and increase the frequency of their targeted attacks.
Phishing messages are getting more and more difficult to distinguish from legitimate emails even for those users are who security literate. Addresses containing the links to phishing sites are masked so perfectly that a user cannot always notice that a site is fake, so similar is it to a genuine site.

The link in this example leads not to the site shown the link, but to the phishing site http://www.usbank.com.ebanking-services-id730325379.usertech.md/client.cfm. The links are extremely very similar; only a very careful user will notice that there is a dot after ‘com’ instead of a slash, and that the domain where the user ends up is entirely different.
Russian-language phishers have become more active in 2007. They attacked WebMoney and Yandex-money e-payment systems several times and tried to access users’ mail accounts by sending messages purportedly from the systems’ administrators which requested users to enter their log in and password.
Spammers used sent messages alleging to be from the administrators of various well-known mail portals. Such messages were designed not only to get confidential information but also to steal money directly. The email below suggests that the user should send an sms-message to a short number to activate special protection for his/ her mail box. Sending such a message simply transfers money from the user’s account to that of the spammers.

The security service of Mail.ru would like to inform you that your mail account has been the subject of an attempted hack, or else you have repeatedly tried to log in using an incorrect password. We make every effort to assist with any problems our users may have. If you did not attempt to log in to your account using an incorrect password, then block the hacker attack on your account as quickly as possible by performing the following actions:
1) Find a mobile telephone that supports SMS messaging.
2) Send a free message with the code 00598520982 to the number ****.
This number is unique and has been reserved especially for you. It will be active for 10 minutes from the time you read this message.
After 10 minutes this number will be deleted and you will no longer be able to protect your account, including against hacker attacks.
Yours sincerely, Roman.
Security Department
Mail.Ru]

Share of “Computer fraud” spam in the total amount of spam
As the graph shows, the period from April to September saw a decline in the share of “Computer fraud” spam in the total amount of spam. However in the 4th quarter of 2007, the volume of such spam fluctuated and in December peaked at 9.2%. So next year this category will probably be among the leaders again.
Personal finance
The “Personal finance” category includes offers for competitively priced insurance, loans and investments. But most of the spam in this category consisted of messages urging readers to invest in the stock market (Stock Spam). This type of fraud is not very common in Russia but it has been successfully used in Europe and the US since 2006. Despite the fact that the share of “personal finance” spam does not make up a significant share of the total volume of spam, cyber criminals are managing to make a profit selling stocks at artificially inflated prices.

Share of “Personal Finance” spam in the total volume of spam
The decline in the share of “Personal finance” spam in the spring and summer of 2007 was probably caused by the fact that this type of fraud attracted the attention of Canadian and the US authorities: in the first quarter of 2007 they expressed concern about this type of spam and promised protect investors from this threat. However by autumn such spam had started to increase again.
Financial spam has always held special meaning for spammers. In 2007 they used their latest technologies, distributing this type of spam in .jpeg and .gif graphical formats and as .pdf and .fdf attachments. This is also the only type of spam which was sent in mp3 format. It is not clear why such creativity is focused on sending financial spam; it may be pure chance that this topic is chosen to test new technologies and approaches.
Political spam on the Russian Internet
Political spam has been fairly common on the Russian Internet this year due to elections to the Russian State Duma. The share of this type of spam was not big enough to influence statistics significantly, but it did contain some interesting and varied content.
Political spam on the Russian Internet included:
- Pre-election promises from various political parties:
‘Vote for the Union of Right-Wing forces on the 2nd December and you will be able to rent your own accommodation straight away!’ - Information about local political conflicts and demonstrations.
- The election program of the LDPR.
- Messages inciting patriotic and nationalistic feeling:
‘Everyone who reads this message should understand: the ENEMY HAS ARRIVED. The enemy must be resisted. Otherwise we are doomed’. - PR mailings specially designed to evoke a negative reaction in the recipient. For instance, one mailing which allegedly stemmed from a political party directed the user to a site supposedly belonging to the party. This site contained a multitude of pop-up windows which would cause the user’s browser to hang.
Political spam on the Russian Internet has several peculiarities:
Firstly, when sending political spam, spammers did not use any tricks.
There is no legal definition of spam in Russia. In countries which do have a legal definition (such as the USA), spam is defined as being mass mailed messages of a commercial nature. Nonetheless, Russian legislation relating to spam is stricter than in the USA. Political spam does not fall under the Russian Federation’s law ‘On Advertising’, but it does contravene the law ‘Concerning Personal Data’. This law forbids the sending of any type of unsolicited messages, not just commercial ones.
Secondly, normally spam messages only contain a short text. However, these pre-election messages contain a relatively large amount of text. The longest email was approximately 13 pages. It’s clear that those who are ordering political spam believe that their message is of interest to the recipients.
Finally, in addition to using traditional methods (i.e. botnets) to send spam, political spam is also being sent as chain messages, with the emails including a request to the recipient to forward the email to friends, family and contacts.
Although English-language political spam was detected this year, it was in far smaller volumes than the Russian-language equivalent.
Forecast
2007 showed that spammers are not gaining any particular benefiting from experimenting with a range of formats. Spam filters are able to react quickly to new types of threat, ensuring that users’ computer remain protected. The trends likely to be seen in 2008 are as follows:
- The volume of spam in mail traffic will not decrease.
- The stand-off between spammers and anti-spam developers will continue, with spammers coming up with new methods and anti-spam developers finding ways to combat them.
- It is likely that spammers will continue to increase the speed of their mailings and the number of messages sent per mailing.
- Spammers may continue to develop graphical spam. In spite of the fact that the volume of graphical spam dropped this year, spammers retain their interest in this area. However, major anti-spam developers are capable of combating this type of threat, making the spammers efforts worthless.
- Spammers will continue to track Internet trends, and social networking spam is likely to become widespread.
- Spammers will also make a return to their roots, spreading links to pages on free hosting sites, and sending distorted text or text which is capable of changing.



















Kaspersky Security Bulletin 2007: Spam report