
H2 2018 in figures
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and regulatory restrictions.
In H2 2018:
- Kaspersky Lab products prevented malicious activity on 40.8% of ICS computers.
- Kaspersky Lab security solutions detected over 19.1 thousand malware modifications from 2.7 thousand different families on industrial automation systems. As before, in the overwhelming majority of cases, attempted infections of ICS computers are random rather than parts of targeted attacks.
- Trojan malware remains the most prevalent among threats that are relevant to ICS computers. Malware of this class was detected on 27.1% of ICS computers. The malicious activity of exploits was prevented on 3.2% of ICS computers,
- backdoors were blocked on 3.1%,
- ransomware – on 2% of ICS computers.

Percentage of ICS computers on which malicious objects of different classes were prevented, 2017 – 2018
- In each month of 2018, the proportion of ICS computers on which malicious activity was prevented was higher than that in the same month of 2017.
- Countries with the highest proportions of ICS computers on which malicious objects were detected during H2 2018 were Vietnam (70.1%), Algeria (69.9%), and Tunisia (64.6%).
- The most secure countries are Ireland (11.7%), Switzerland (14.9%), Denmark (15.2%), Hong Kong (15.3%), the UK (15.7%), and the Netherlands (15.7%).

Percentage of ICS computers on which malicious objects were detected in different countries of the world
- As in the past years, the main sources of threats to computers in the industrial infrastructure of organizations are the internet (26.1%), removable media (8.3%), and email (4.9%).
- The percentage of ICS computers on which malicious email attachments were blocked has increased in nearly all regions of the world. This change probably reflects the growth in the number of phishing attacks on industrial enterprises in H2 2018.

Percentage of ICS computers on which malicious email attachments were blocked in different regions of the world
- Phishing attacks are the main vector of targeted attacks on industrial companies. Malicious attachments from phishing emails pose a danger not only to office computers but also to some of the computers in the industrial infrastructure: Trojan-spy, backdoor and keylogger malware was blocked at least on 4.3% of ICS computers globally. All of these types of malware often show up in the phishing emails sent to industrial enterprises.
- Western Europe (5.1%) is, surprisingly, one of the TOP 3 regions based on the percentage of ICS computers on which malicious email attachments were blocked. This is in large part due to the percentage for Germany nearly doubling (from 3.6% to 6.5%).
Vulnerabilities identified by Kaspersky Lab ICS CERT in 2018
Kaspersky Lab ICS CERT experts continued the previous year’s research on security issues affecting third-party hardware-based and software solutions that are widely used in industrial automation systems. A particular emphasis was placed on open-source products used in various vendors’ solutions. Analyzing car software for vulnerabilities became a new area of research for Kaspersky Lab ICS CERT.
- In 2018, Kaspersky Lab ICS CERT identified 61 vulnerabilities in industrial and IIoT/IoT systems. Vendors closed 29 of these vulnerabilities during the year.
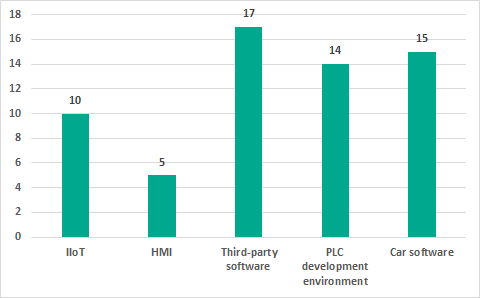
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2018 by types of components analyzed
- 46% of the vulnerabilities identified, if exploited, could lead to remote execution of arbitrary code on the target system or a denial-of-service (DoS) condition. A significant part of the vulnerabilities (21%) could also enable an attacker to bypass authentication.
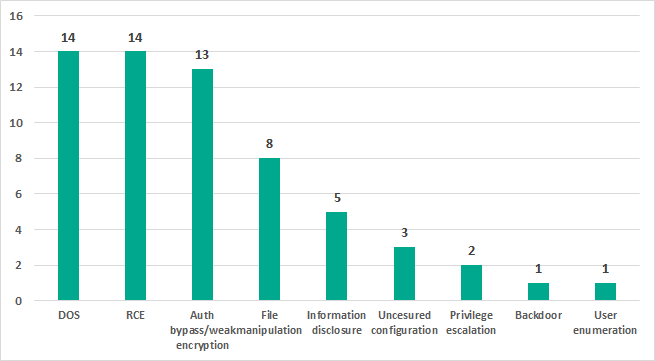
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2018 by possible exploitation consequences
- During 2018, 37 CVE entries were published based on information about vulnerabilities identified by Kaspersky Lab ICS CERT (information on 15 vulnerabilities closed in 2018 had been provided to vendors in 2017).
- The absolute majority of those vulnerabilities identified by Kaspersky Lab ICS CERT for which CVEs were published in 2018 have CVSS v.3 base scores of 7.0 or more, which places them in the most severe group. Seven of these vulnerabilities were assigned the highest possible base score of 10. These include vulnerabilities in third-party software, and LibVNCServer and LibVNCClient cross-platform solutions.
You can find information on the key events of H2 2018, an overview of vulnerabilities published during the year, and detailed statistics in the full version of the report on the Kaspersky Lab ICS CERT website.
Threat Landscape for Industrial Automation Systems in H2 2018























Paul Anthony
It would be interesting to know the method of data collection. Exactly how were these stats compiled? (Survey, scans, customers, etc)
Rafaqat Ali
The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. So I think its provided by customers.
Jason Page
First paragraph
“All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and regulatory restrictions.”