
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and government organizations, banks, telecoms operators, industrial enterprises, and individual users. In this report, Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the findings of its research on the threat landscape for industrial automation systems conducted during the first half of 2018.
The main objective of these publications is to provide information support to global and local incident response teams, enterprise information security staff and researchers in the area of industrial facility security.
Key events
Energetic Bear/Crouching Yeti: attacks on servers
In February, Kaspersky Lab ICS CERT published a report on an investigation into the initial infection tactics used by the notorious APT group Energetic Bear/Crouching Yeti, as well as the results of an analysis of several web servers compromised by the group in 2016 and early 2017, using information provided by the server owners.
Energetic Bear/Crouching Yeti has been active since at least 2010, attacking companies and individuals in various countries. The specialists at CrowdStrike initially noted a strong focus on the energy and industrial sectors, which may explain the name Energetic Bear. Later, when the diversity of the group’s attacks became clearer, the researchers at Kaspersky Lab named it Crouching Yeti. The targets of the attacks are mainly concentrated in Europe and the US. Recently, the number of attacks on companies in Turkey increased significantly. According to US-CERT and the UK National Cyber Security Centre, the Energetic Bear/Crouching Yeti APT group is linked to the Russian government.
The initial infection tactics used by the group is a multi-step process that begins with phishing emails being sent out with malicious documents and infecting various servers. Some infected servers are used by the group as auxiliaries – used only for hosting various tools. Others are infected so they can be used in watering hole attacks, with some servers hosting an SMB link that leads to other servers that steal the authentication data of potential victims.
With some rare exceptions, the Energetic Bear/Crouching Yeti group uses publicly available tools to carry out their attacks. All the utilities discovered by the Kaspersky Lab ICS CERT experts have open source code that is freely available on GitHub. This makes the task of attack attribution very difficult without additional group “markers”.
In most cases observed by Kaspersky Lab ICS CERT, the attackers performed tasks to identify vulnerabilities, gain persistence on different nodes and steal authentication data in order to develop the attack further.
An analysis of the compromised servers and the attacks on them showed that for Energetic Bear/Crouching Yeti, almost any vulnerable server on the internet is seen as a potential foothold from which to develop targeted attacks.
The investigation into the initial, intermediate and subsequent targets of these attacks also revealed a diverse geography. The largest number of victims and targets was in Russia, followed by Turkey and Ukraine. Under half of the systems attacked were related to industry, agricultural services and utilities.
Attacks on industrial enterprises using RATs
Kaspersky Lab ICS CERT reported on yet another wave of phishing emails containing malicious attachments aimed primarily at industrial enterprises in Russia. The malicious program used in the attacks installs legitimate software for remote administration – TeamViewer or Remote Manipulator System/Remote Utilities (RMS) – that allows attackers to gain remote control over the targeted systems. Various techniques are used to mask the presence and activity of the unauthorized software.
When they need to move further within a compromised network, the attackers can download an additional set of malicious programs, which is specifically tailored to the attack on each individual victim. This set of malware may contain spyware, additional remote administration tools, software to exploit vulnerabilities in the operating system and application software, as well as the Mimikatz utility, which makes it possible to obtain account data for Windows accounts.
Also, Kaspersky Lab products blocked multiple attacks on the industrial network of an automobile manufacturer and service company, in particular, on computers designed to diagnose the engines and onboard systems of trucks and heavy-duty vehicles.
A RAT was installed and intermittently used on at least one of the computers in the company’s industrial network. Over a period of several months, numerous attempts to launch various malicious programs using the RAT were blocked on the computer. The blocked programs included modifications of the malware detected by Kaspersky Lab products as Net-Worm.Win32.Agent.pm. When launched this worm immediately begins to proliferate on the local network using exploits for the MS17-010 vulnerabilities – the same ones that were published by ShadowBrokers in the spring of 2017 and were used in attacks by the infamous WannaCry and ExPetr cryptors.
The Trojan-Downloader.Nymaim malware family was also blocked. Representatives of this family are often used to download modifications of the Necus family botnet agent which in turn is used to infect computers with ransomware from the Locky family.
Statistics
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and regulatory restrictions.
Methodology
The data was received from ICS computers protected by Kaspersky Lab products that Kaspersky Lab ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
- supervisory control and data acquisition (SCADA) servers;
- data storage servers (Historian);
- data gateways (OPC);
- stationary workstations of engineers and operators;
- mobile workstations of engineers and operators;
- Human Machine Interface (HMI).
The statistics analyzed also include data received from computers of industrial control network administrators and software developers who develop software for industrial automation systems.
For the purposes of this report, attacked computers are those on which our security solutions have been triggered at least once during the reporting period. When determining percentages of machines attacked, we use the ratio of unique computers attacked to all computers in our sample from which we received anonymized information during the reporting period.
ICS servers and stationary workstations of engineers and operators often do not have full-time direct internet access due to restrictions specific to industrial networks. Internet access may be provided to such computers, for example, during maintenance periods.
Workstations of system/network administrators, engineers, developers and integrators of industrial automation systems may have frequent or even full-time internet connections.
As a result, in our sample of computers categorized by Kaspersky Lab ICS CERT as part of the industrial infrastructure of organizations, about 42% of all machines had regular or full-time internet connections in H1 2018. The remaining machines connected to the Internet no more than once a month, many much less frequently than that.
Main figures
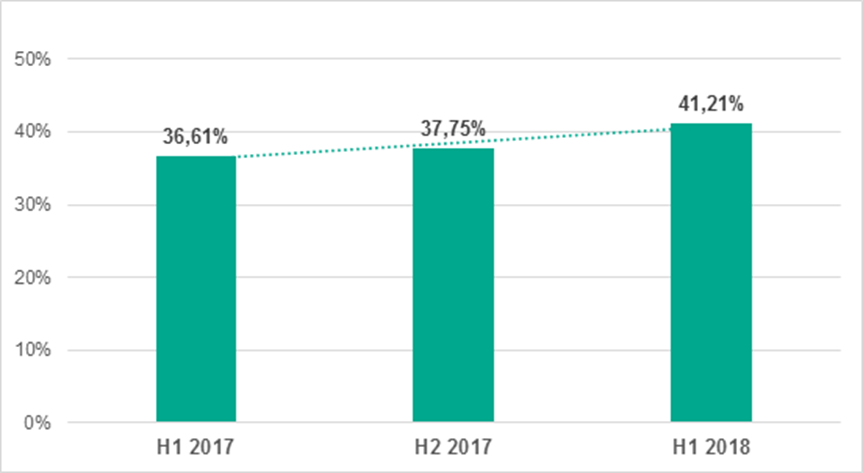
The percentage of ICS computers attacked in H1 2018 increased by 3.5 p.p. compared with H2 2017 and reached 41.2%. The year-over-year increase was 4.6 p.p.
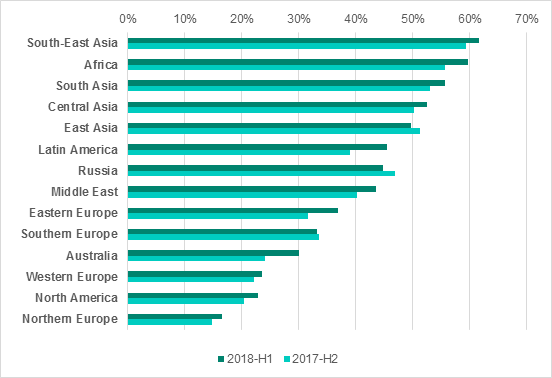
A comparison between different regions of the world shows that:
- countries in Africa, Asia and Latin America are significantly worse off in terms of the percentage of ICS computers attacked than countries in Europe, North America and Australia;
- the figures for Eastern Europe are considerably greater than those for Western Europe;
- the percentage of ICS computers attacked in Southern Europe is higher than that in Northern and Western Europe.
Presumably, this situation could be due to the amounts of funds invested by organizations in infrastructure protection solutions.
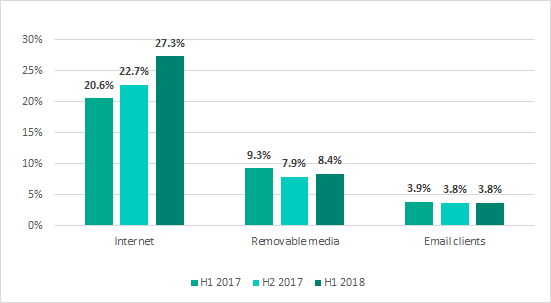
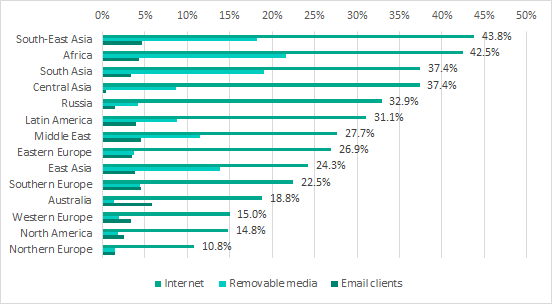
The main sources of infection for computers in organizations’ industrial network infrastructure are the internet, removable media and email. Contrary to the conventional wisdom about control networks being isolated, in the past years the internet became the main source of infection for computers on organizations’ industrial networks.
While a year ago, in H1 2017, the internet was the source of threats blocked on 20.6% of ICS computers, in H1 2018 the figure was as high as 27.3%.
More information about events during H1 2018, detailed statistics and our recommendations you may find in the full version of the report (PDF)
Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) is a global project launched by Kaspersky Lab in 2016 to coordinate the efforts of automation system vendors, industrial facility owners and operators, and IT security researchers to protect industrial enterprises from cyberattacks. Kaspersky Lab ICS CERT devotes its efforts primarily to identifying potential and existing threats that target industrial automation systems and the Industrial Internet of Things.

















Threat Landscape for Industrial Automation Systems in H1 2018