
Year 2022 in numbers
| Parameter | H1 2022 | H2 2022 | 2022 |
| Percentage of attacked ICS computers globally | 31.8% | 34.3% | 40.6% |
| Main threat sources | |||
| Internet | 16.5% | 19.9% | 24.0% |
| Email clients | 7.0% | 6.4% | 7.9% |
| Removable devices | 3.5% | 3.8% | 5.2% |
| Network folders | 0.6% | 0.6% | 0.8% |
| Percentage of ICS computers on which malicious objects from different categories were blocked | |||
| Malicious scripts and phishing pages (JS and HTML) | 12.9% | 13.5% | 17.3% |
| Denylisted internet resources | 9.5% | 10.1% | 13.2% |
| Spy Trojans, backdoors and keyloggers | 8.6% | 7.1% | 9.2% |
| Malicious documents (MSOffice+PDF) | 5.5% | 4.5% | 6.2% |
| Worms | 2.8% | 2.5% | 3.5% |
| Viruses | 2.4% | 2.4% | 3.2% |
| Miners – executable files for Windows | 2.3% | 1.5% | 2.7% |
| Web miners running in browsers | 1.8% | 1.8% | 2.5% |
| Malware for AutoCAD | 0.6% | 0.6% | 0.8% |
| Ransomware | 0.6% | 0.4% | 0.7% |
Global threat statistics
In H2 2022, the percentage of ICS computers on which malicious objects were blocked increased by 3.5 percentage points compared to the previous six-month period, reaching 34.3%. This was higher than the percentages for 2021 and even 2020.
Percentage of ICS computers on which malicious objects were blocked, 2020 – 2022
In H2 2022 the percentage of ICS computers on which malicious objects were blocked increased in the automotive industry (+4.6 p.p.) and in the energy sector (+1 p.p.). In other industries tracked, the percentage decreased.
Percentage of ICS computers on which malicious objects were blocked in some industries, H2 2022
Geography
In different regions of the world, the percentage of ICS computers on which malicious activity was prevented ranged from 40.1% in Africa and Central Asia, which led the ranking, to 14.2% and 14.3%, respectively, in Western and Northern Europe, which were the most secure regions.
Regions of the world ranked by percentage of ICS computers on which malicious objects were blocked, H2 2022
African and Central Asian countries were prevalent among the 15 countries and territories with the highest percentage of ICS computers on which malicious objects were blocked in H2 2022.
15 countries and territories with the highest percentage of ICS computers on which malicious objects were blocked, H2 2022
In the Top 10 ranking of countries with the lowest percentage of ICS computers on which malicious objects were blocked, all countries, with the exception of Israel, were European.
10 countries and territories with the lowest percentage of ICS computers on which malicious objects were blocked, H2 2022
In H2 2022, the most significant increase among all countries in the percentage of ICS computers on which malicious objects were blocked was observed in Russia, where that percentage increased by 9 p.p.
Russia. Percentage of ICS computers on which malicious objects were blocked, 2020 – 2022
Variety of the malware detected
In H2 2022, Kaspersky security solutions blocked malware from 7,684 different families on industrial automation systems.
Percentage of ICS computers on which the activity of malicious objects from different categories was prevented, H2 2022
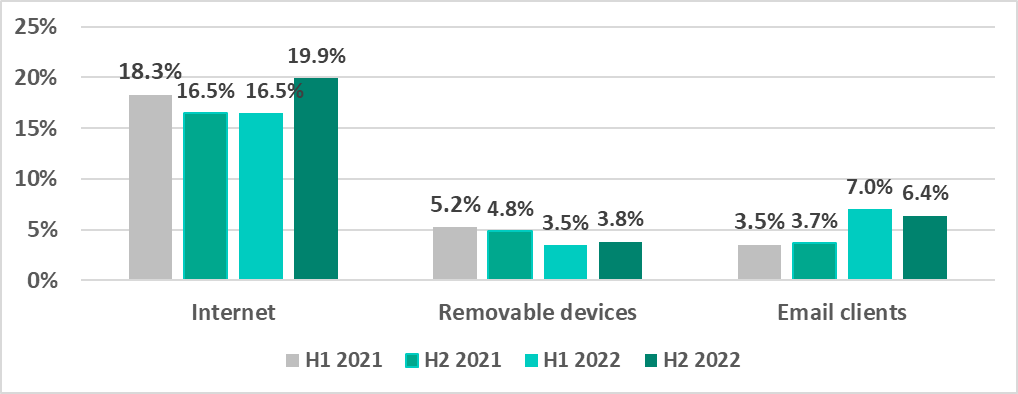
Main threat sources
The internet, removable devices and email clients remained the main sources of threats for computers in the operational technology infrastructure of organizations.
Percentage of ICS computers on which malicious objects from different sources were blocked, 2021 – 2022
In H2 2022, a very significant growth in the percentage of ICS computers on which internet threats were blocked – 12 p.p. and 7.8 p.p., respectively – was recorded in the regions of Russia and Central Asia.
Regions ranked by percentage of ICS computers on which internet threats were blocked, H2 2022
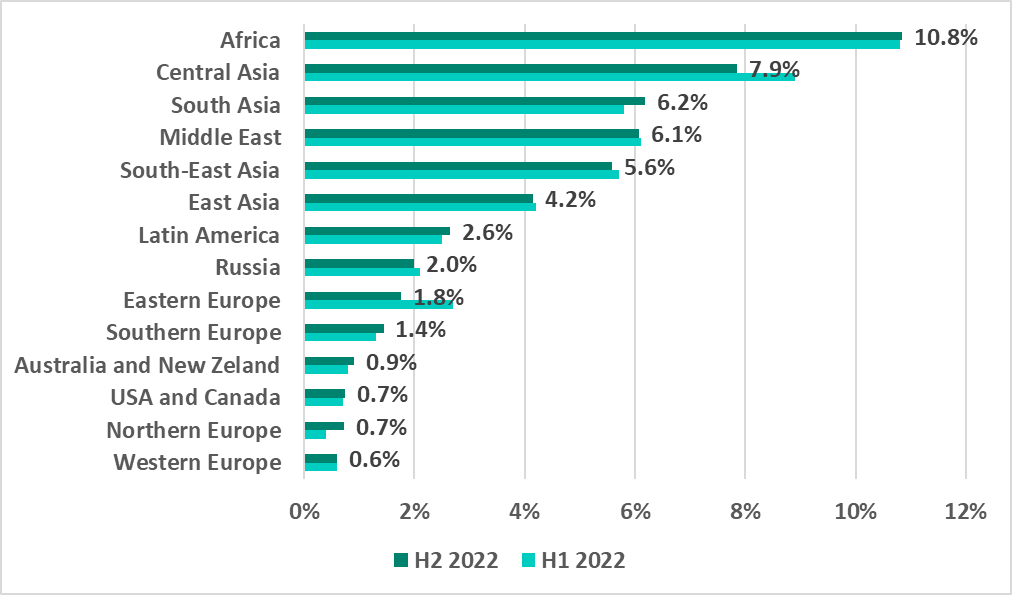
As per tradition, Africa topped the ranking of regions based on the percentage of ICS computers on which malware was blocked when removable devices were connected.
Regions ranked by percentage of ICS computers on which malware was blocked when removable devices were connected, H2 2022
Southern Europe topped the ranking of regions based on the percentage of ICS computers on which malicious email attachments and phishing links were blocked. Northern Europe was the only region in which the percentage increased (+0.3 p.p.) in H2 2022.
Regions ranked by percentage of ICS computers on which malicious email attachments and phishing links were blocked, H2 2022
The full report has been published on the Kaspersky ICS CERT website.


























Threat landscape for industrial automation systems for H2 2022