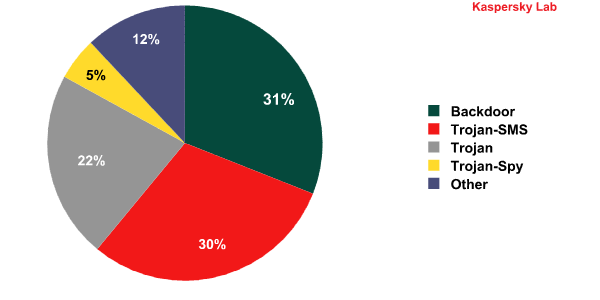
Forecasts for 2014 – Expert Opinion
In 2014 we expect significant growth in the number of threats related to economic and domestic cyber-espionage, with cyber-mercenaries/cyber-detectives playing an active role in such attacks. The full report is available here