
The publication was updated on April 16, 2020
Introduction and methodology
Six months ago, we created a special alert that notifies users about commercial spyware (stalkerware) products installed on their phones. This report examines the use of stalkerware and the number of users affected by this software in the first eight months of 2019.
Сonsumer surveillance technology has evolved rapidly in recent years and the very purpose of surveillance activity has changed dramatically. The rise of the internet and subsequent explosion in mobile device usage has led to a thriving type of surveillance software – known as stalkerware. The software allows users to spy on other people – for example, to monitor their messages, call information and GPS locations – in complete stealth. It can often be used to abuse the privacy of current or former partners and even strangers. This can be done by simply manually installing an application on the targeted victim’s smartphone or tablet. Once in place, the stalker receives access to a range of personal data, despite being remote from the victim. It differs greatly from parental control software. While parental control apps aim to restrict access to risky and inappropriate content and persistently notifies a user about its requests, stalkerware is about providing the abuser with surveillance to spy on a victim, without the consent of an individual.
The vast majority of stalkerware apps are not available on official app stores – like Google Play – and installation requires access to a dedicated website and access to the victim’s device. Those with bad intentions may use it to monitor employee emails, track children’s movements and even spy on what a partner is up to. Such uses may lead to harassment, surveillance without consent, stalking and even domestic violence. However, current laws to regulate the use of stalkerware are not yet strong enough to deter culprits from abusing and taking advantage of other people.
The data in this report has been taken from aggregated threat statistics obtained from the Kaspersky Security Network, to measure how often and how many users encountered stalkerware threats in the first eight months of 2019, compared to what was found last year. The Kaspersky Security Network is the infrastructure dedicated to processing cybersecurity-related data streams from millions of voluntary participants around the world. In this blog, we have explored why stalkerware is being used and where it is implemented most prolifically.
Main findings
- From January to August 2019, around the world, there were more than 518,223 cases when our protection technologies either registered presence of stalkerware on users’ devices or detected an attempt to install it – a 373% increase in the same period in 2018
- In the first eight months of 2019, 37,532 users encountered stalkerware at least once. This is a 35% increase from the same period in 2018 when 27,798 users were targeted
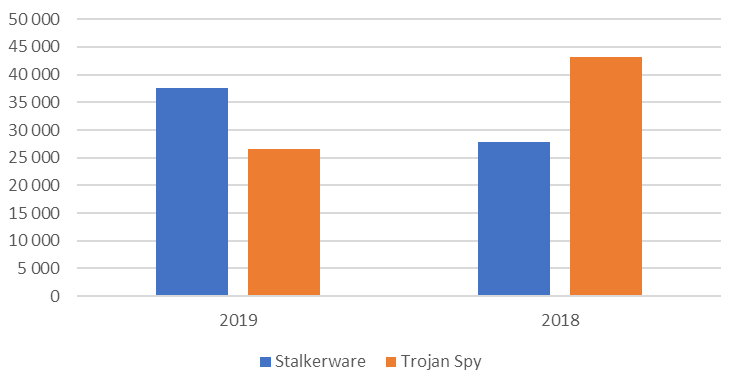
- The number of users targeted by full-throttle spyware detected as Trojan-Spy reached 26,620 the first eight months of 2019, which makes it a minority compared to the number of users who encountered stalkerware
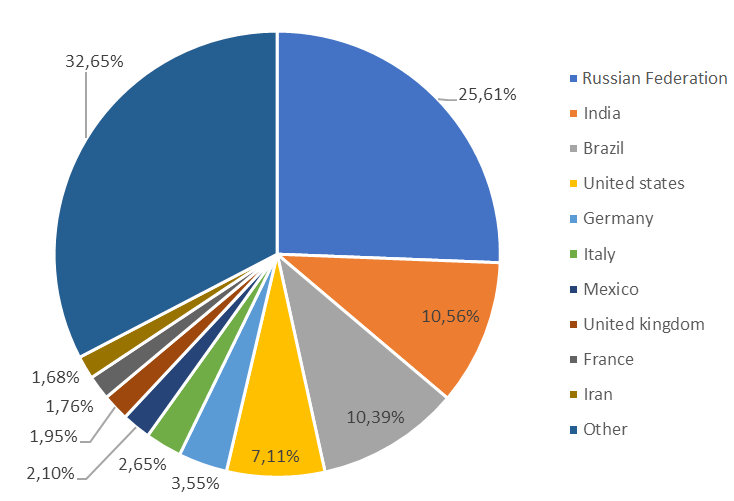
- The Russian Federation remains the most prominent region for stalkerware globally, accounting for 25.6% of potentially affected users, in the first eight months of 2019. India is in second place with 10.6% of affected users, and Brazil is in third place (10.4%). The United States hold forth place with 7.1%
- When it comes to Europe – Germany, Italy and the UK hold the top three places respectively
Main findings, updated April 2020
- By the end of 2019, number of our mobile users facing stalkerware rose by 67%: 40,386 unique users were attacked in 2018, while in 2019 this number increased to 67,500
- There was a twofold increase in the number of the attacks during the second half of 2019 when compared to the first half. In January 2019, 4483 Kaspersky mobile users were attacked; in September 2019, this number rose to 9546, and, in December 2019, this number reached 11052 attacked users
- Russia, Brazil, India, and the US are the most prominent regions for stalkerware globally, accounting for 23.4%, 9.4%, 9% and 5.6% of affected users respectively in 2019
- When it comes to Europe – Germany (3.1%), Italy (2.4%) and France (1.8%) are the top three affected places respectively
Rise of the stalkerware problem
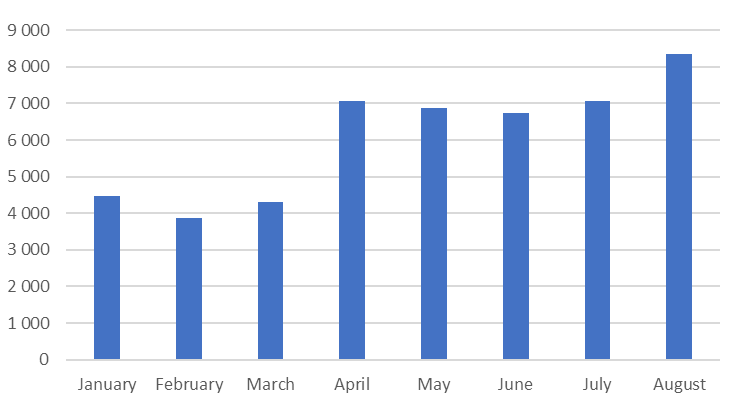
This year has seen a sharp rise in the number of detections of stalkerware on Android devices protected by Kaspersky products. One reason for this rise could be the improvement in detecting stalkerware software through cybersecurity solutions. In April, Kaspersky launched functionality in its Android security app – Privacy Alert – that specifically alerts users if a software that can be used for stalking is found on their device. Since then, the number of detections has steadily risen. For instance, 4,315 users encountered stalkerware in March 2019, compared to 7,075 in April – a 64% increase in just one month. This figure rose to 9,251 during August, 94% higher than the month before the functionality was launched.
These openly-sold consumer surveillance programs are often used for spying on colleagues, family members or partners, and are in great demand. For a relatively modest fee, sometimes as little as $7 per month, these apps stay hidden while keeping their operators informed about the device activity, such as its owner’s location, browser history, text messages, social media chats, and more. Some of them can even make video and voice recordings.
To further examine the extent of the stalkerware problem, Kaspersky has analyzed the last eight months’ worth of activity. Between January to August 2019, 37,533 users encountered stalkerware on their devices at least once. This is a 35% increase from the same period in 2018 when 27,798 users were targeted. Overall, there were 518,223 cases when Kaspersky products either registered the presence of stalkerware on users’ devices or detected an installation attempt in the period from January to August 2019 – a staggering 373% increase compared to the period in 2018.
Examples of software used for stalking purposes
The most prolific stalkerware family in 2019 was identified as Monitor.AndroidOS.MobileTracker.a, which affected 6,559 unique users. In second place, Monitor.AndroidOS.Cerberus.a was detected on the devices of 4,370 users, closely followed in third place by Monitor.AndroidOS.Nidb.a (4,047).
Comparing the results from 2018, the top two differ from last year. Monitor.AndroidOS.Nidb.a and Monitor.AndroidOS.PhoneSpy.b were found most on the devices of users in 2018, reaching 4,427 and 2,819 respectively. Monitor.AndroidOS.XoloSale.a was the third most common stalkerware reaching 1,946 users.
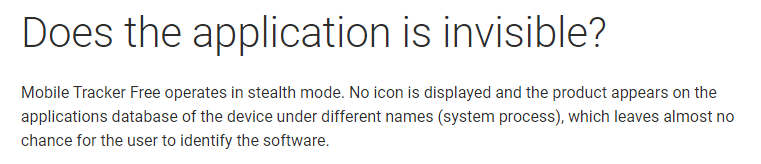
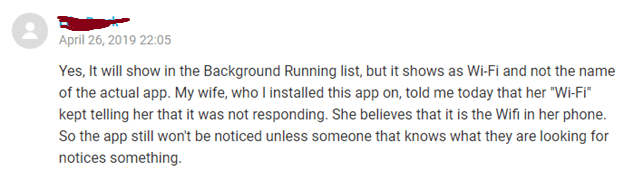
In our internal classification system, a Monitor.AndroidOS.MobileTracker.a record is used to identify a Mobile Tracker Free application, which is positioned as a tool to track the activity of children or employees. In fact, the application allows tracking of the user’s location, their correspondence both in SMS messages and messenger applications (WhatsApp, Hangouts, Skype, Facebook Messenger, Viber, Telegram, etc.), as well as calls. A third-party can also access victims’ photos from the phone and the camera in real-time, along with their browser history, files on the device, calendar and contact list. In addition, the application provides the ability to remotely control the device. As well as all of this, there is a possibility of working in a hidden mode under the disguise of system applications.
The next application – Cerberus (Monitor.AndroidOS.Cerberus.a) – is positioned as an anti-theft app. However, it also allows a stalker to work in ‘hidden’ mode and to prevent its deletion. Among other things, it provides the ability to track the location of the device, take pictures from the camera and screenshots, as well as record audio from the microphone.
The third-placed Monitor.AndroidOS.Nidb.a is in fact a group of similar applications: iSpyoo/TheTruthSpy/Copy9. Unlike the previous two applications, some representatives of this group openly advertise themselves as a means of spying on a partner and even write articles about it.
The set of functions is quite standard for such programs yet still impressive – website tracing, interception of correspondence in SMS and in messenger applications, call tracing and browser history. Like many other similar applications, they require super-user rights (administration rights) to operate some functions. They can work in ‘hidden’ mode, and their names in the list of installed applications mimic the system processes.
Where is stalkerware found?
There is a global market for legal spyware and stalkerware software, as proven by the diverse range of regions where the most attacks are taking place. The top 10 countries with the largest share of users attacked with stalkerware do not have geopolitical similarities and are not in close proximity.
Kaspersky’s findings show that Russia is the region where stalkerware activity is peaking. Persistent activity in India has led to the country being the second most prominent region for stalkerware-related incidents from January to August, with 10.56% users affected.
Brazil accounted for 10.39% of attacked users in 2019, while the United States are now fourth (7.11%). There are advocacy groups in the country raising awareness about the dangers of stalkerware and conducting revealing user research. 72 domestic violence shelters were surveyed by National Public Radio, with 85% of domestic violence workers saying they have assisted victims whose abuser tracked them using GPS. Nearly three-quarters (71%) of domestic abusers monitor survivors’ computer activities, while 54% tracked survivors’ cell phones with stalkerware. The fifth most prevalent country in 2019 was Germany with (3.55%).
Stalkerware on the cyberthreat landscape
When comparing stalkerware and spyware to the rest of the attacks mobile users face – such as adware, riskware and malware – it takes up a big share of less targeted not-a-virus programs. In the first eight months of 2019, Kaspersky detected 2,350,862 users attacked with potentially unwanted threats and just 1.60% of them were related to stalkerware. However, unlike the majority of mass potential threats (like adware), stalkerware requires a specific stalker to act and carry out its operation. Every target is being stalked and chosen on purpose. So, while the numbers are lower, stalkerware takes a more targeted effort to affect a victim and has a disturbing figure of abuse behind each of them.
To get the big picture when assessing the stalkerware development dynamics, we’ve compared stalkerware to the full scale, illegal survelliance malware for PC that we detect as Trojan Spy. The results have proved, that while illegal spyware is in decline, stalkerware is thriving.
Our analysis of the first eight months of 2019 shows that the number of users who encountered stalkerware had, in fact, surpassed the figure for Trojan-Spy attacks. While 2018 saw more than 43,000 spyware targets compared to around 28,000 stalkerware targets, in 2019 the picture changed. The number of users that encountered stalkerware grew by 35% to reach over 37,000, while spyware tools accounted for 26,620 of targets.
There has been a notable rise in the number of stalkerware-related incidents registered by Kaspersky products when compared to all threats from the figures in 2018. Between January and August last year, such software made up just 1.01% of the overall number of users who faced any kind of potentially dangerous (adware and others from not-a-virus category) software (2,740,023). It appears that stalkerware is growing in popularity, while more traditional malware attacks are less prolific than they were 12 months ago.
Conclusion and recommendations
It is clear to see that stalkerware is on the rise and becoming much more prominent in the cybersecurity landscape. In accordance with the overall number of detected riskware, adware and spyware attack fluctuations year-on-year, the percentage of stalkerware-related incidents continues to rise. It may take time to discover the role of stalkers on the cyberthreat landscape, but more incidents are now accounted for. Thanks to improved cybersecurity software, there has been a sharp rise since Kaspersky launched its own solution to notify users about stalkerware in April 2019.
There has also been a level of consistency around which countries are the most likely to experience stalkerware-related incidents, with Russia, India, the United States and Germany amongst the most prominent for the last two years.
The good news for users is that functionality and effective solutions are being put in place so they can protect themselves. Practical ways to solve the problem are coming to the fore. IT security companies and advocacy organizations working with domestic abuse victims should join forces to ensure that cybersecurity companies respond better to stalkerware. Such initiatives would help victims through technology and expertise.
We believe that every person has a right to be privacy-protected. That’s why we deliver security expertise, work closely with international organizations and law enforcement agencies to fight cybercriminals, as well as develop technologies, solutions and services that help you stay safe from the cyberthreats.

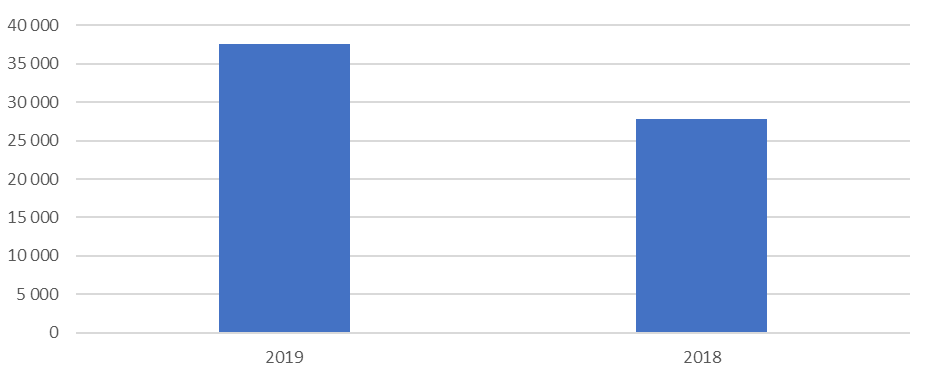




















The State of Stalkerware in 2019