
It’s unusual for a day to go by without finding some new variant of a known ransomware, or, what is even more interesting, a completely new one. Unlike the previously reported and now decrypted Xpan ransomware, this same-but-different threat from Brazil has recently been spotted in the wild. This time the infection vector is not a targeted remote desktop intrusion, but a more massively propagated malicious campaign relying on traditional spam email.
Since the infection is not done manually by the bad guys, their malware has a higher chance of being detected and we believe that is one of the reasons for them to have added one more level of protection to the code, resorting to a binary dropper to launch the malicious payload.
Given that this particular ransomware is fairly well known by now, instead of opting for the usual branding and marketing efforts in which most ransomware authors invest time, this group has decided to choose an unnamed campaign, showing only an email address for technical support and a bitcoin address for making the payment. It has become a kind of urban legend that if you can’t find something on Google, then it doesn’t exist.
Not very long ago, we saw the birth of truly autochthonous Brazilian ransomware, without much technical sophistication and mainly based on an open-source project. While there’s a long road ahead for local bad guys to achieve the level of the key players on the ransomware scene, this particular family is interesting to study since there have been versions in English, Italian, and now Brazilian Portuguese. Is this ransomware being sold as a commodity in underground forums with Brazilian crews just standing on the shoulders of giants? Or is this a regional operation just starting out?
As one of the very few ransomware variants that prepend a custom ‘Lock.’ extension to the encrypted files instead of appending it, the task of recognizing this malware is not particularly difficult. However, understanding its true origins could still be considered an ongoing debate.
The drop
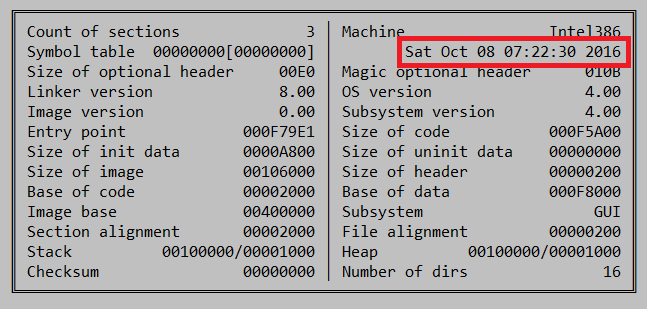
If we trust that the first transaction corresponds to the very first victim, the campaign has probably been active since 2016-04-04 17:29:26 (April 4th, 2016). In reality, this is not exactly accurate. The timestamp of the original dropper shows that the sample was actually compiled at the beginning of October:
That would mean that the criminal behind the campaign might have had different ransomware campaigns running in the past, or is just using the same BTC wallet for more than his criminal deeds.
The dropper is protected by the popular .NET obfuscator SmartAssembly, as can be seen by the string “Powered by SmartAssembly 6.9.0.114”. Once executed, it tries to mask itself in the Alternate Data Stream of the NTFS file system in Windows:
“%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Sims.exe:Zone.Identifier
It’s capable of disabling Windows LUA protection:
“HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM”; Key: “ENABLELUA”; Value: “00000000”
(cmd.exe /c %WINDIR%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
Reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f)
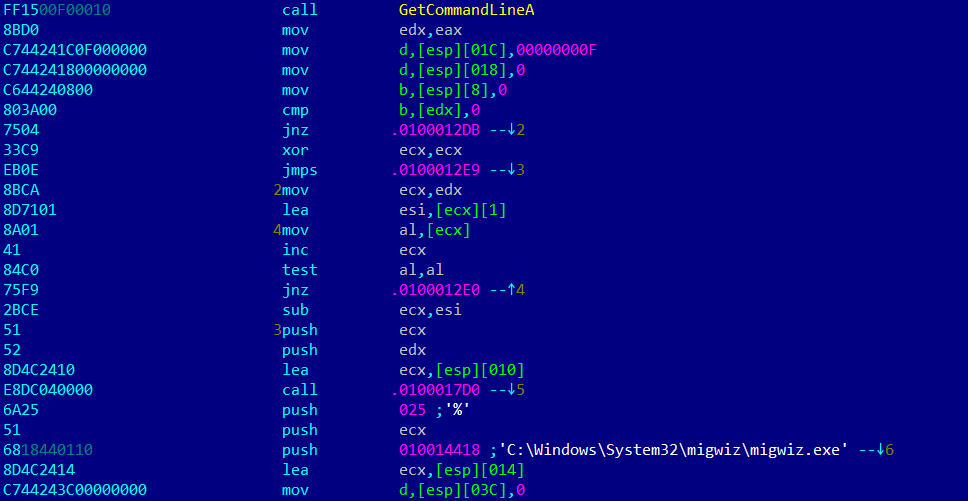
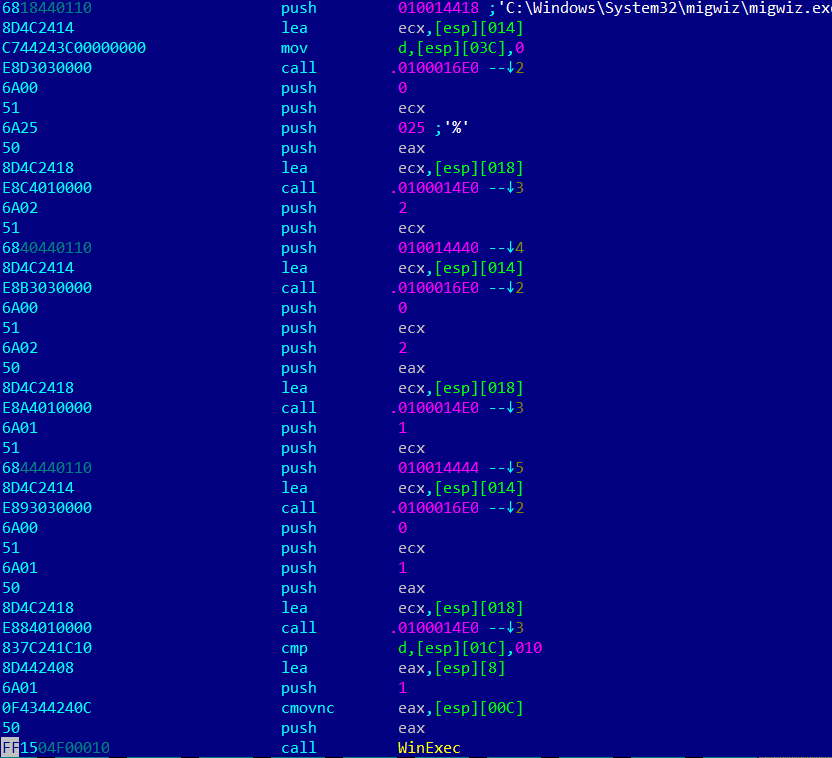
The mechanism used to write new information to the registry is quite unusual: it uses the official windows application ‘migwiz.exe’ in order to bypass the UAC screen, not requiring any action from the user to execute with elevated privileges.
The malware is able to do that by writing a library ‘cryptbase.dll’ to the same folder as the ‘migwiz.exe’ file. Then, as soon as it’s launched, the process will load this library, which has a WinExec call that will launch the command line provided by the parameter.
The reason why they are using MigWiz is because this process is one that is in Microsoft’s auto-elevate list, meaning it can be elevated without asking for explicit permission.
As a simple mean of information gathering, the dropper will read the name of the infected computer:
HKLM\SYSTEM\CONTROLSET001\CONTROL\COMPUTERNAME\ACTIVECOMPUTERNAME”; Key: “COMPUTERNAME
Moreover, it includes data stealer techniques, such as retrieving information from the clipboard, or while it’s being typed on the keyboard. Additionally it has the capability to reboot the user’s machine.
@4333be: push ebp
@4333bf: mov ebp, esp
@4333c1: sub esp, 14h
@4333c4: push ebx
@4333c5: mov ebx, dword ptr [ebp+08h]@4333c8: lea eax, dword ptr [ebp-04h]@4333cb: push eax
@4333cc: push 00000028h
@4333ce: call dword ptr [00482310h] ;GetCurrentProcess@KERNEL32.DLL
@4333d4: push eax
@4333d5: call dword ptr [0048202Ch] ;OpenProcessToken@ADVAPI32.DLL
@4333db: test eax, eax
@4333dd: je 0043341Eh
@4333df: lea ecx, dword ptr [ebp-10h]@4333e2: push ecx
@4333e3: push 00487D68h ;SeShutdownPrivilege
Finally, it drops and executes the file tmp.exe (corresponding hash B4FDC93E0C089F6B885FFC13024E4B9).
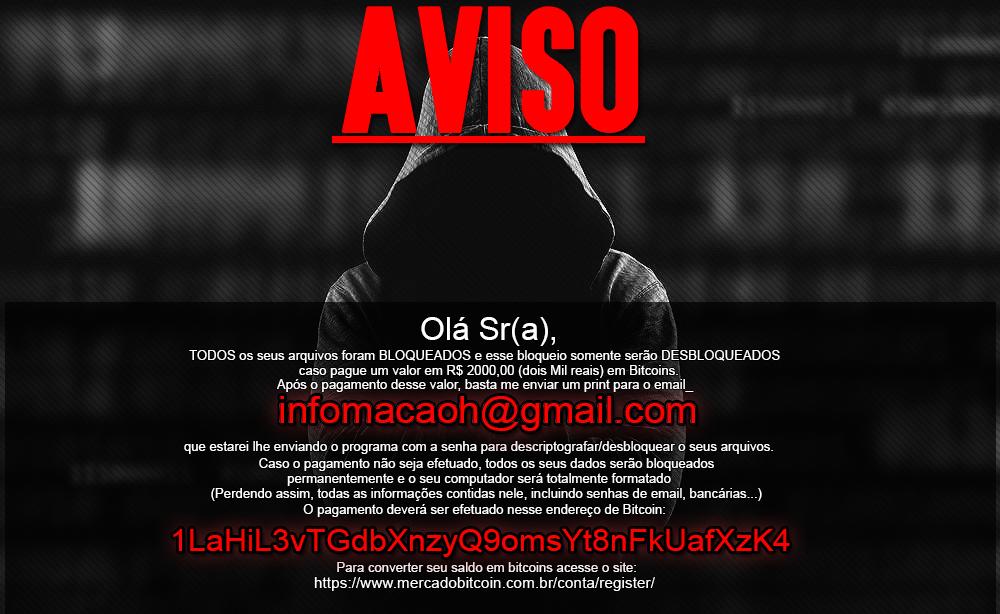
Hello sir, hello madam, your files have been locked
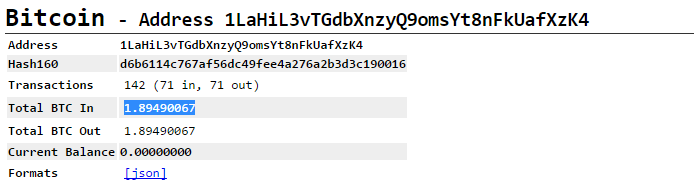
After the infection has been completed, as is usual in all ransomware families, the ransom note is shown. This time, it is written in Brazilian Portuguese and demanding 2000 BRL, which equates to around 627 USD or 1 BTC at the time of writing.
The bitcoin address provided (1LaHiL3vTGdbXnzyQ9omsYt8nFkUafXzK4) for payment shows total deposits for 1.89 BTC although many transactions have been made since the creation of this wallet. This is leading us to believe that either the criminal has been using the wallet for other purposes or they have bargaining with the victims and offering them a lower price, as depicted by the amount in each transaction.
The ransom note is very succinct, without giving any special payment URL or any other type of information. The victim will have to learn about bitcoin payments the hard way, and should they need support they can reach the criminals through a single email point of contact.
AVISO
Ola Sr(a),
TODOS os seus arquivos foram BLOQUEADOS e esse bloqueio somente serão DESBLOQUEADOS
caso pague um valor em R$ 2000,00 (dois Mil reais) em Bitcoins
Após o pagamento desse valor, basta me enviar um print para o email
infomacaoh@gmail.com
que estarei lhe enviando o programa com a senha para descriptografar/desbloquear o seus arquivos.
Caso o pagamento não seja efetuado, todos os seus dados serão bloqueados
permanentemente e o seu computador sera totalmente formatado
(Perdendo assim, todas as informações contidas nele, incluindo senhas de email, bancárias…)
O pagamento deverá ser efetuado nesse endereço de Bitcoin:
1LaHiL3vTGdbXnzyQ9omsYt8nFkUafXzK4
Para converter seu saldo em bitcoins acesse o site:
https://www.mercadobitcoin.com.br/conta/register/
Growth of ransomware in Brazil
The growth of ransomware in Brazil has been nothing short of impressive, taking into consideration that during October 2016 alone the popular ransomware family Packed.NSIS.MyxaH.gen family grew by 287.96%, and another of the usual suspects Trojan-Ransom.Win32.CryptXXX.gen grew by 56.96%, (when compared to the previous month in each case.)
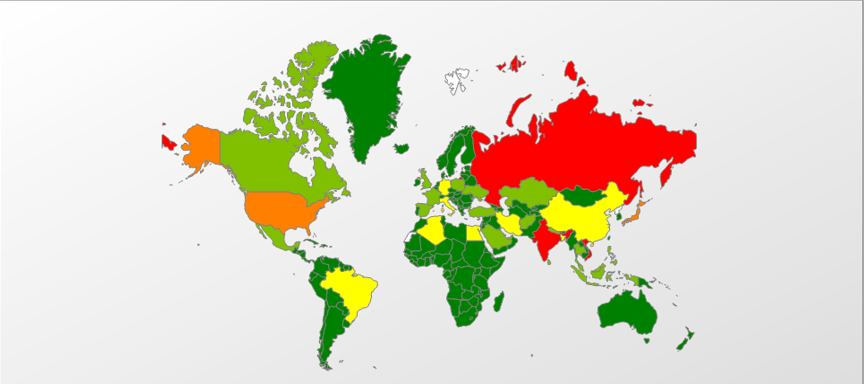
In 2016, the 3 most important families of ransomware have been Trojan-Ransom.Win32.Blocker, accounting for 49.63% of the total infections, Trojan-Ransom.NSIS.Onion, 29.09%, and Trojan-Ransom.Win32.Locky, 3.99%. Currently, Brazil is the eighth most affected country worldwide as far as ransomware infections go for this year, and ranked first in Latin America.
Indicators of compromise
File: 04.exe
Size: 1049600
MD5: 86C85BD08DFAC63DF65EAEAE82ED14F7
Compiled: Saturday, October 8 2016, 11:22:30 – 32 Bit .NET
File: tmp.exe
Size: 842220
MD5: BB4FDC93E0C089F6B885FFC13024E4B9
Compiled: Sunday, January 29 2012, 21:32:28 – 32 Bit



















The “notification” ransomware lands in Brazil