
Last night the Kido (aka Conficker/ Downadup) botnet kicked into action – what everyone’s been on the lookout for since 1st April.
The computers infected with Trojan-Downloader.Win32.Kido (aka Conficker.c) contacted each other over P2P, telling infected machines to download new malicious files.
This latest Kido variant – Net-Worm.Win32.Kido.js – is very different to previous ones, with two notable points: once again it’s a worm, and it’s only functional until 3rd May. We’re still digging into the files, and we’ll post updates.
Kido doesn’t only download updates for itself; it’s the other files it downloads which really make the story interesting.
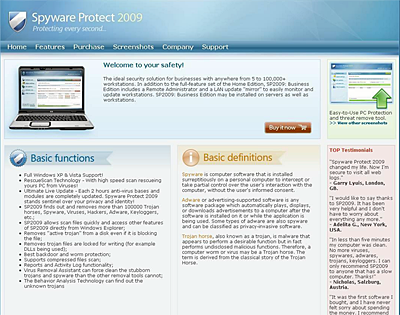
One of the files is a rogue antivirus app, which we detect as FraudTool.Win32.SpywareProtect2009.s. The first version of Kido, detected back in November 2008, also tried to download fake antivirus to the infected machine. And once again, six months later, we’ve got unknown cybercriminals using the same trick.
The rogue software, SpywareProtect2009, can be found on spy-protect-2009.com, spywrprotect-2009.com, spywareprotector-2009.com.
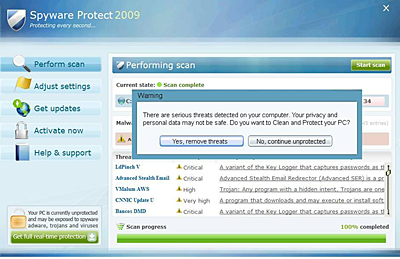
Once it’s run, you see the app interface, which naturally asks if you want to remove the threats it’s “detected”. Of course, this service comes at a price – $49.95.
At the moment, the rogue antivirus comes from sites located in Ukraine (131-3.elaninet.com.78.26.179.107) although Kido is downloading it from other sites.
The latest version of Kido also downloads Email-Worm.Win32.Iksmas.atz to infected systems. This email worm is also known as Waledac, and is able to steal data and send spam. When it first appeared in January 2009, a lot of IT experts noted the similarity between Kido and Iksmas. The Kido epidemic was mirrored by an email epidemic caused by Iksmas which was on just as large a scale. But up until now, there wasn’t any firm evidence of a link between the two worms.
The evidence appeared last night. Both Kido and Iksmas are now present on infected machines and part of the gigantic botnet designed to conduct spam mailings. And, although there’s no confirmation of this yet, it may be that sites belonging to companies and organizations which are part of the Conficker Working Group will find themselves under attack.
UPDATE: Our colleagues over at ISC have just posted saying the the CWG site is down; they’re looking into it.
UPDATE 2: Wired is reporting that the outage is due to cable sabotage.























The neverending story