
At the end of the last year the authors of Duqu and Stuxnet tried to eliminate all traces of their activity. They wiped all servers that they used since 2009 or even earlier. The cleanup happened on October 20.
There were virtually no traces of Duqu since then. But several days ago our colleagues in Symantec announced that they found a new “in-the-wild” driver that is very similar to known Duqu drivers. Previous modifications of Duqu drivers were compiled on Nov 3 2010 and Oct 17 2011, and the new driver was compiled on Feb 23 2012.
So, the authors of Duqu are back after a 4 months break.
Duqu is back
The newly discovered driver does not contain any new functionality compared to its previous versions. The code contains only minor modifications, and they were most likely done to evade detection from antivirus programs and detection tools such as the CrySyS Duqu Toolkit. Here’s a list of changes compared to older versions:
- The code was compiled with different optimization settings and/or inline attributes of functions.
- The size of the EXE stub that is injected with the PNF DLL was increased by 32 bytes.
- The LoadImageNotifyRoutine routine now compares the module name with “KERNEL32.DLL” using hash checksums instead of simple string comparison.
- The size of the encrypted configuration block was increased from 428 to 574 bytes. There are no new fields in in the block, but the size of the registry value name (“FILTER”) field was increased. This makes the registry value name easily modifiable – probably for future use.
- The algorithm of the two subroutines that decrypt the encrypted config block, registry value and PNF DLL has been changed. This is the third known algorithm used in the Duqu encryption subroutines.
- The algorithm of the hash function for the APIs has changed. All the hash values were changed correspondingly.
Old hash function, used in previous versions of the Duqu driver:
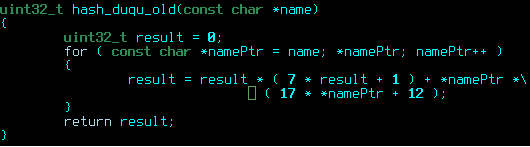
New hash function:
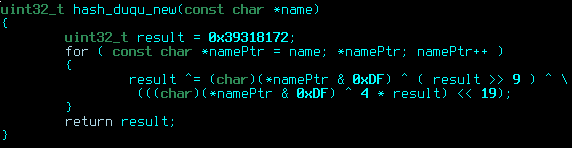
The fact that the new driver was found in Iran confirms that most of Duqu incidents are related to this country.
Number of incidents
According to the information collected from our sources and from our colleagues in Symantec, there are at least 21 incidents related to Duqu.
During the investigation of several incidents we discovered more than one modification of Duqu per incident. We treat each such group of samples as a single case.
Several infected machines did not contain main Duqu modules, but at the same time they contained the files created by these modules, with names starting with “~DQ”, “~DF”, “~DO”. A number of incidents were discovered while analyzing the contents of captured C&C servers. These incidents were also included in our statistics.
Most of the victims of Duqu were located in Iran.
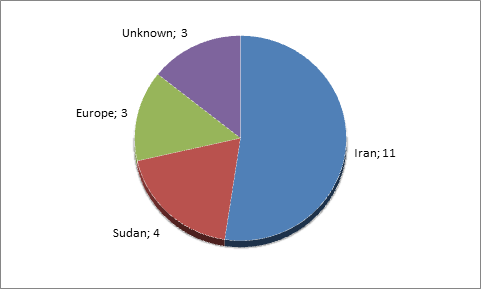
Geographical distribution of Duqu incidents
The scope of activities of companies that became victims of Duqu and information targeted by the Trojan indicates that the attackers were looking for any information related to production control systems used in different industries in Iran, and for information about trade relationships of particular organizations.
It is beyond any doubt that there were more Duqu incidents than we actually know, but we assume that there were no more than several dozens of them in total.
Known modifications of Duqu
The following table contains information about all the components of Duqu we know about. The files marked with green are known. The files marked with red are missing; they were not found on infected machines, however, we know the names and sizes of some of the missing files indirectly.
| # | File name | Size | Date | Country | 1st level C&C | 2nd level C&C | Discovered by |
| a | cmi4432.sys | 29568 | 03.11.2010 | Hungary | India | Philippines | Crysys |
| cmi4432.pnf | 192512 | 17.07.2011 | |||||
| cmi4463.pnf | |||||||
| b | jminet7.sys | 24960 | 03.11.2010 | Hungary | India | Philippines | Crysys |
| netp191.pnf | 232448 | 04.11.2010 | |||||
| netp192.pnf | |||||||
| c | igdkmd16b.sys | 25088 | 03.11.2010 | Iran | Vietnam | Germany | Kaspersky |
| netp794.pnf | 232448 | 16.02.2011 | |||||
| netq795.pnf | |||||||
| c2 | igdkmd16b.sys | 25088 | 17.10.2011 | Iran | Vietnam | Germany | Kaspersky |
| netp794.pnf | 240640 | 18.10.2011 | |||||
| netq795.pnf | |||||||
| d | iraid18.sys | 24960 | Iran | Kaspersky | |||
| ird18.pnf | |||||||
| ird182.pnf | |||||||
| e | e1g61i32.sys | 24960 | 03.11.2010 | Sudan | Kaspersky | ||
| e1g62i32.pnf | 192512 | ||||||
| e1g61i32.pnf | |||||||
| f | adp95xx.sys | 24960 | 03.11.2010 | Sudan | Netherlands | South Korea | Kaspersky |
| adp95xx.pnf | 248320 | 17.04.2011 | |||||
| adp96xx.pnf | |||||||
| g | bpmsg.sys | 24832 | Iran | Kaspersky | |||
| main pnf unknown | |||||||
| config pnf unknown | |||||||
| h | allide1.sys | Europe | Belgium | ? | Symantec | ||
| iddr021.pnf | 232448 | 04.11.2010 | |||||
| iddr022.pnf | |||||||
| i | nfrd965.sys | 24960 | 17.10.2011 | Austria/Indonesia? | Vietnam | ? | VirusTotal/Symantec |
| netf1.pnf | 240640 | 18.10.2011 | |||||
| netf2.pnf | |||||||
| i2 | nfrd965.sys | 24960 | 03.11.2010 | Austria/Indonesia? | Symantec | ||
| j | iastor451.sys | 24960 | 03.11.2010 | South Korea? | VirusTotal | ||
| main pnf unknown | |||||||
| config pnf unknown | |||||||
| k | adpu321.sys | 24960 | 17.10.2011 | UK | VirusTotal | ||
| main pnf unknown | |||||||
| config pnf unknown | |||||||
| k2 | adpu321.sys | 24960 | 03.11.2010 | ? | systemexplorernet | ||
| main pnf unknown | |||||||
| config pnf unknown | |||||||
| l | jminet1.sys | 24960 | 03.11.2010 | Iran | Kaspersky | ||
| netq793.pnf | |||||||
| netq794.pnf | |||||||
| m | ql50xx.pnf | 24960 | 03.11.2010 | Sudan | Kaspersky | ||
| main pnf unknown | |||||||
| ql50xz.pnf | |||||||
| n | battd.sys | 24960 | 03.11.2010 | Iran | Kaspersky | ||
| battd771.pnf | |||||||
| battd772.pnf | |||||||
| o | mcd9x86.sys | 24320 | 23.02.2012 | Iran | Symantec | ||
| main pnf unknown | |||||||
| config pnf unknown | |||||||
We have a total of 14 drivers, including one signed driver (cmi4432.sys); there are also 4 missing driver samples.
There are 7 different versions of the main Duqu module (PNF DLL) in our collection. These modules are set up to interact with five 1st tier C&C servers that have been shut down as a result of actions taken by Kaspersky Lab and Symantec. Several 2nd tier C&C servers were shut down, too.
Conclusions
The return of the Duqu Trojan in February 2012 after 4 months of silence indicates that our original assumptions were correct. When you invest as much money as were invested in Duqu and Stuxnet, it’s impossible to simply shutdown the operation. Instead, you do what cybercriminals have learned to do through long experience – change the code to evade detection and carry on as usual.
With a total of less than fifty victims around the world, Duqu remains of the most mysterious Trojans ever spotted in the wild. Its focus on Iran indicates a persistent attacker with a strong, clear agenda. Its complexity and multiple layers of encryption and obfuscation indicate how important it is for the project to remain under the radar. It can be assumed that future developments will focus on this direction.





















The mystery of Duqu: Part Ten