
The vulnerability in the Windows Help and Support Center has been a constant irritation to antivirus experts for the third week in succession. I will try to provide an analysis of the problem with the help of KSN.
We first detected samples of the exploit on 10 June and at the time of writing, over 14,000 attacks using CVE-2010-1885 have been registered.
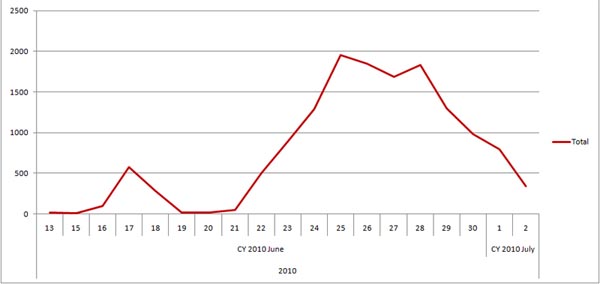
The graph above shows the number of detections per day.
However, the most important feature is the figure indicating the exploit’s distribution on the Internet. According to KSN, on 2 July, 2010 the total number of websites hosting the exploit averaged 300.
Below are a couple of Top 10s for two variants of the exploit:
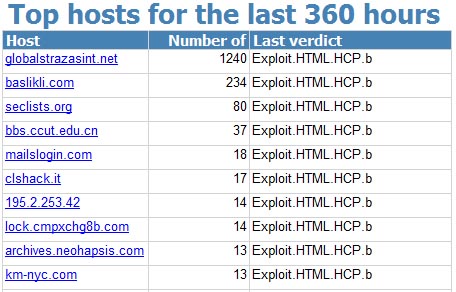
In the first Top 10 the two obvious leaders are malicious sites which spread malware using a Pay-per-Install scheme. They include so-called exploit packs that attack users via several vulnerabilities at a time. There are also a few legitimate IT security sites in the list that published examples of the exploit.
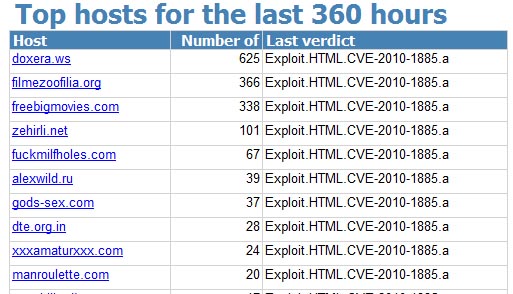
In the second list the situation is more straightforward. All of the sites listed, and there are around 200 in total, also participate in illegal partner, or affiliate, programs.
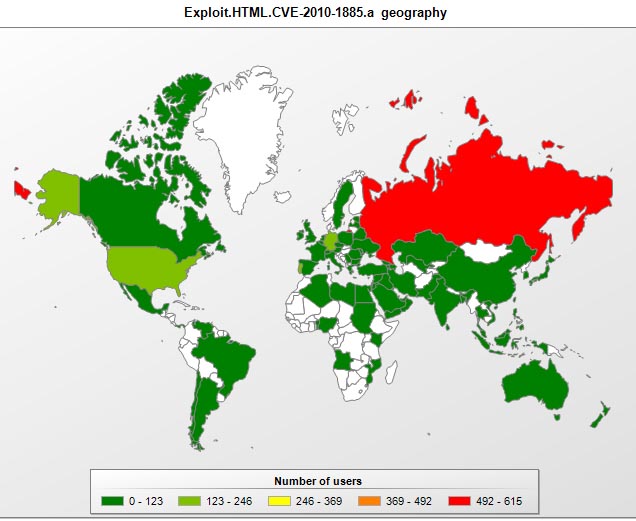
The majority of sites currently spreading malware with the help of the HCP exploit can be traced back to Russia and that is why Russia is the worst affected by this vulnerability and leads in terms of the number of users attacked.
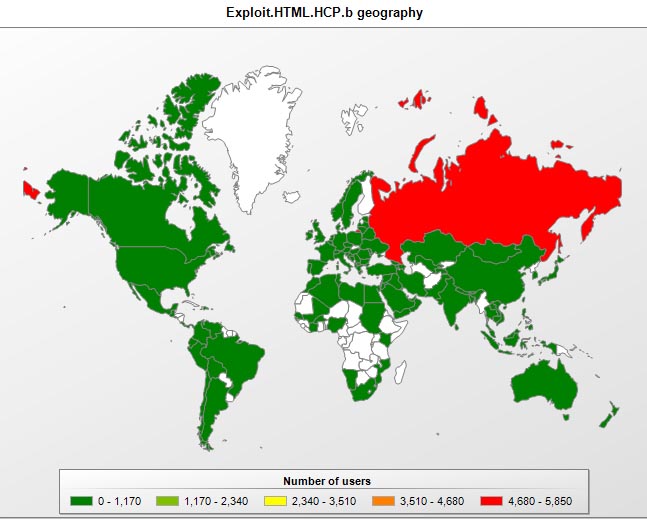
Users in the USA, Portugal and Germany have also been targeted more than in other countries.
P.S. Microsoft has not announced any plans to release a patch for this vulnerability ahead of schedule, which means another couple of uneasy weeks on the Internet for users of Windows XP and Windows Server 2003.






















The figures behind the headache