
Digital game distribution services have not only simplified the sale of games themselves, but provided developers with additional monetization levers. For example, in-game items, such as skins, equipment, and other character-enhancing elements as well as those that help one show up, can be sold for real money. Users themselves can also sell items to each other, with the rarest fetching several thousand dollars. And where there’s money, there’s fraud. Scammers try to get hold of login details to “strip” the victim’s characters and sell off their hard-earned items for a juicy sum.
One of the most popular platforms among users (and hence cybercriminals) is Steam, and we’ve been observing money-making schemes to defraud its users for quite some time. Since June, however, such attacks have become more frequent and, compared to previous attempts, far more sophisticated.
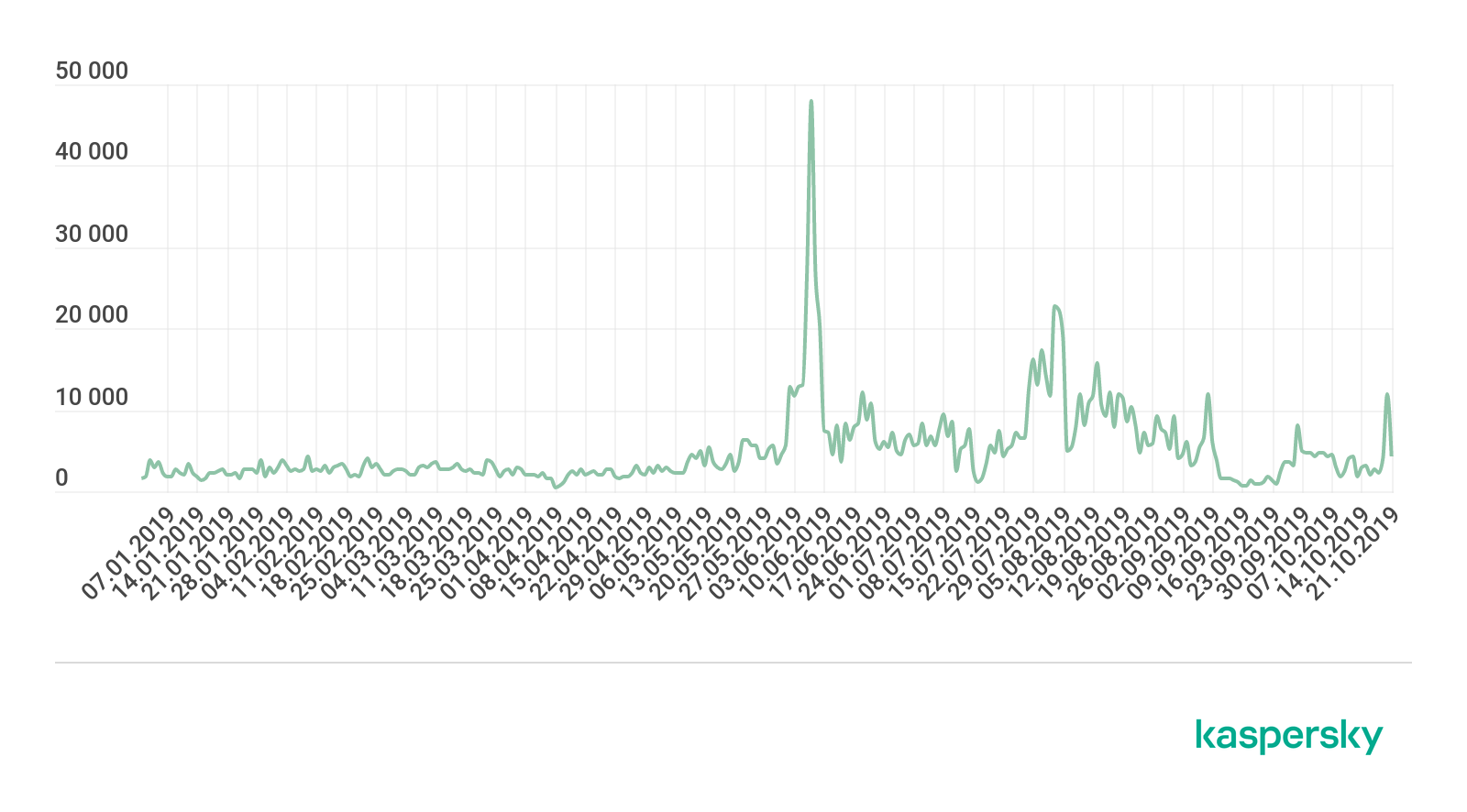
Steam phishing attacks, January 2019 – September 2019
It all starts with an online store
Like many others, the scam we uncovered is phishing-based. Attackers lure users to websites that mimic or copy online stores — in this case, the ones linked to Steam — that sell in-game items. The fake resources are high-quality and it is really hard, sometimes even impossible, to distinguish them from the real thing. Such phishing sites:
- Are very well implemented, no matter if copied or made from scratch
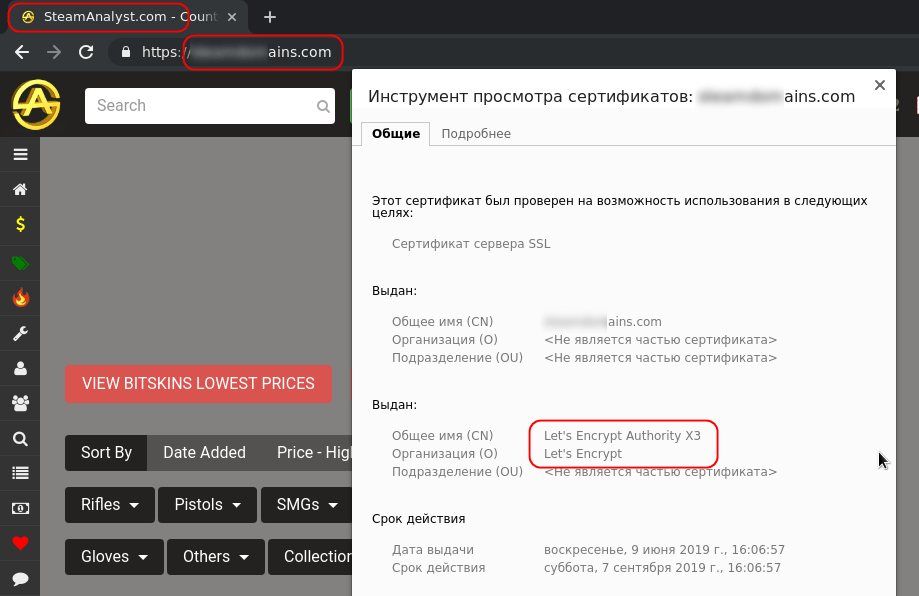
- Have a security certificate and support HTTPS
- Issue a warning about the use of cookies
- Provide some links to the original website (that go nowhere when clicked)
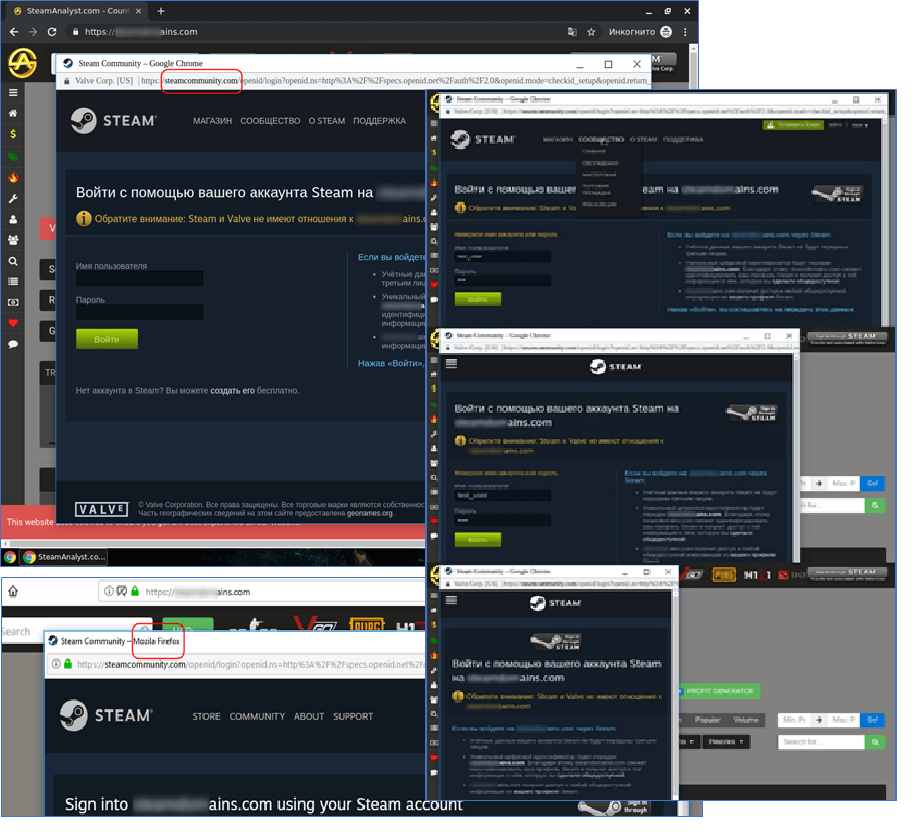
The longer a user spends on the site, the more likely they are to spot something odd. Therefore the scammers do not want users to stay long, and phishing sites get down to business very quickly: on clicking any link, the user immediately sees a window asking for their Steam login and password. By itself, this might not raise a red flag. The practice of logging into a service through another account (Facebook, Google, etc.) is quite common, and Steam accounts can likewise be used to log into third-party resources. All the more so since the supposed trading platform requires access to the user’s account to obtain data on what items they have.
The fake login/password window is very similar to the real one: the address bar contains the correct URL of the Steam portal, the page has an adaptive layout, and if the user opens the link in another browser with a different interface language, the content and title of the fake page change in accordance with the new “locale.”
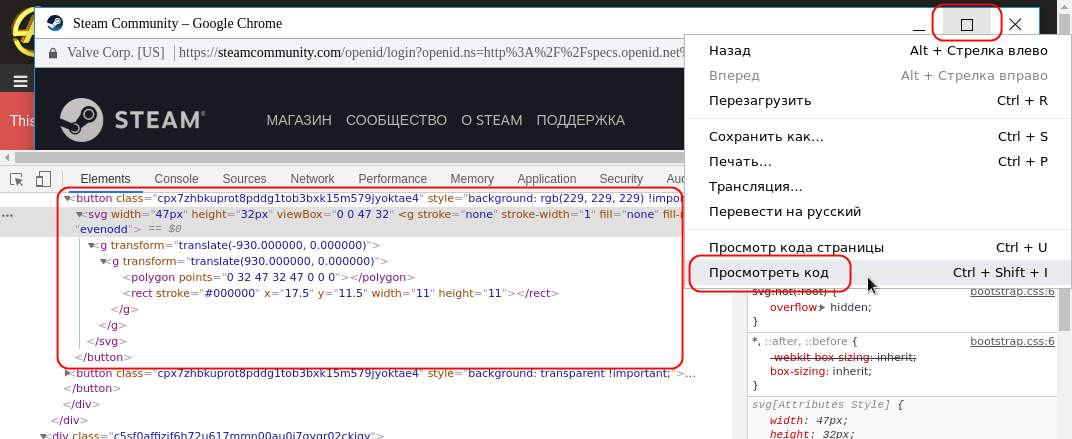
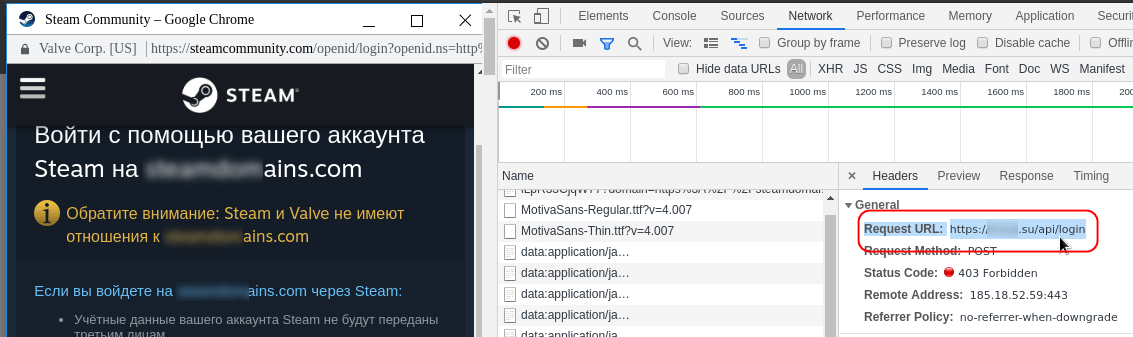
However, right-clicking on the title of this window (or control elements) displays the standard context menu for web pages, and selecting “view code” exposes the window as a fake, implemented using HTML and CSS:
In one example, the username and password are transferred using the POST method through an API on another domain that also belongs to scammers.
The fake login form is given extra credence by the fact that the entered data is verified using the original services. On entering the wrong login and password, the user is shown an error message:
When a valid login and password pair is entered, the system requests a two-factor authorization code that is sent by email or generated in the Steam Guard app. Obviously, the entered code is also forwarded to the scammers, who gain full control over the account as a result:
Other varieties
Besides creating “complex” login windows using HTML and CSS, cybercriminals also employ the good-old trick of a fake form in a separate window, but with an empty address value. Although the window display method is different, the operating principle is the same as above. The form verifies the entered data, and if the login and password match, it prompts the victim to enter a two-factor authorization code.
How to stay protected
The main tips for guarding against this and similar scams are essentially no different to those for identifying “ordinary” phishing sites. Look carefully at the address bar and its contents. In our example, it contained the correct URL, but less sophisticated variants are more common — for example, the website address might not match the store name, or display the words “about:blank”.
Pay close attention to login forms on “external” resources. Right-click on the title bar of the window containing the form, or try to drag it outside the main browser window to make sure it’s not fake. Besides, if you suspect that the login window is not real, open the Steam main page in a new browser window and log into your account from there. Then go back to the suspicious login form and refresh the page. If it’s real, a message will appear saying that you’re already logged in.
If everything seems normal, but something still arouses suspicion, check the domain using WHOIS. Genuine companies do not register domains for short periods and do not hide their contact details. Lastly, activate two-factor authentication through Steam Guard, follow Steam’s own recommendations, and use a security solution with anti-phishing technology.
Steam-powered scammers




















Victim01
I got scammed this way not through an online store but when registering to Destiny through what at least looked like the Bungie website. I’ve no idea what was fake and what real, everything looked legit.