
A while back I blogged about “offerwalls” that were collecting leaked user data. But now it seems that not only users are under attack. Recently while browsing Reddit, I found the account of a popular app developer who claims that another developer on the Android Market had stolen his app, added ad spam code to it, and uploaded it under his own account with the same name. After some research I discovered that this was, in fact, the case
The app, called ElectricSleep was originally created by Jon Willis. You can find it HERE
According to the description, ElectricSleep can “Improve the quality of your sleep with this smart alarm clock. ElectricSleep is an alarm clock that records your sleep cycles and wakes you up gently during a light sleep cycle. The sleep data it records is saved and analyzed so that you can understand and improve upon your sleeping habits.”
In comparing the original app to the stolen version, the first obvious sign of tampering was in the permissions:
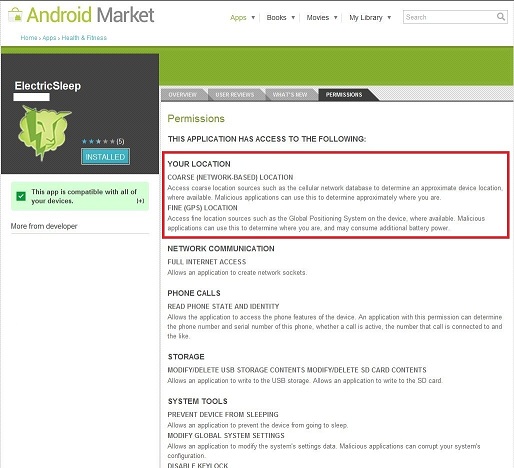
The real app does not ask for Location permission:
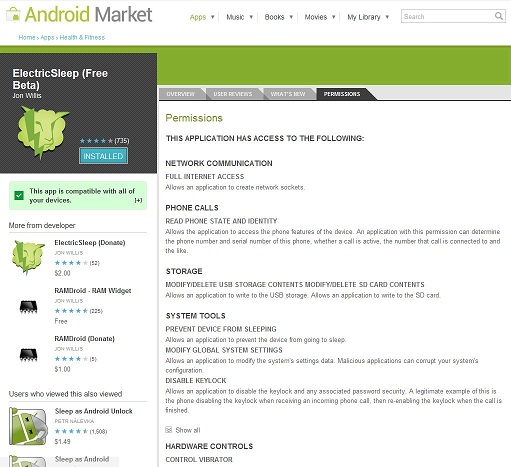
So in researching what the copied app does, I was able to discover that a Pay-Per-Install library was added to the original code. The library comes as part of an SDK from a company called AirPush:

Airpush does exactly what its name states. It pushes different types of advertisements to end users, and these advertisements generate revenue for the app developer, or in this case, the app copier. How much money can be made? Well according to Airpush’s website:
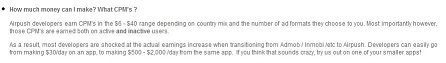
“Airpush developers earn CPM’s in the $6 – $40 range”. CPM stands for “Cost Per M”, or cost per thousand. This means that Airpush pays the developer every time 1,000 impressions are made. How much is paid is in constant fluctuation.
Essentially what has happened is that a rogue developer has downloaded Mr. Willis’ app, added pay-per-install code, and then uploaded the modified app as his own under a different developer account. The offending app has since been removed, but the developer account of the infringer is still active.
Users are no doubt sick of intrusive advertising without warning. As a result, another developer has released “AirPush Detector” which is capable of detecting advertising frameworks installed in apps. While these Pay-Per-Install services are not illegal, they can be intrusive, and stealing apps just to add on advertising code is definitely in violation of the Android developer License agreement.
AirPush Detector can be found HERE




















Stealing apps, installing ads