Nothing holds a potential reader’s attention stronger than a story about a catastrophe. A few days ago we came across an excellent example of a mass mailing where spammers took full advantage of this universal fascination with destruction.
The mass mailing in question is intended primarily for the US users. In it, the spammers list a series of recent tragedies and predict that worse is yet to come. They also propose a solution – just click the link to find out how to protect yourself and your family from harm.
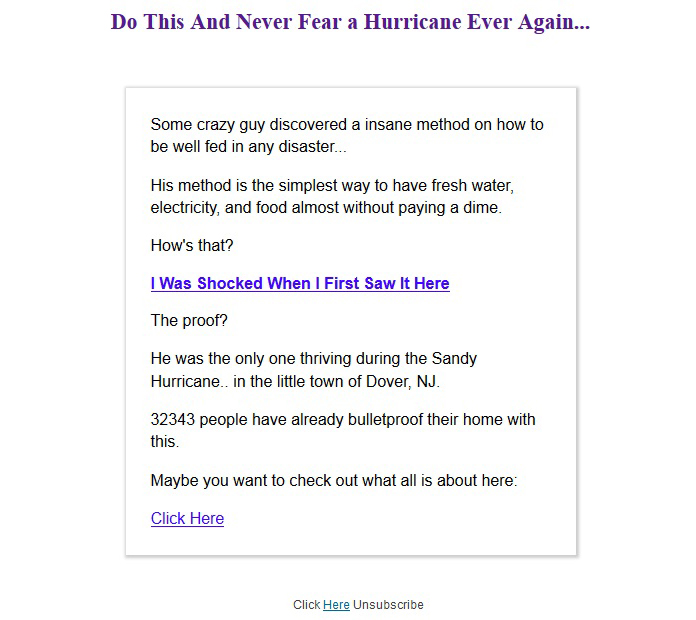
In the email below the authors mention Sandy hurricane that hit North America about two years ago.
The spammers recall the crisis that faced many Americans after that hurricane – stranded in badly-damaged houses without food or electricity. The author of the email claims to know a guy who lived right in the center of the storm, in a wind-lashed city in New Jersey, and who suffered no shortages of anything. Click the link, and the spammers promise you’ll enjoy the same good fortune if disaster strikes your neighborhood.
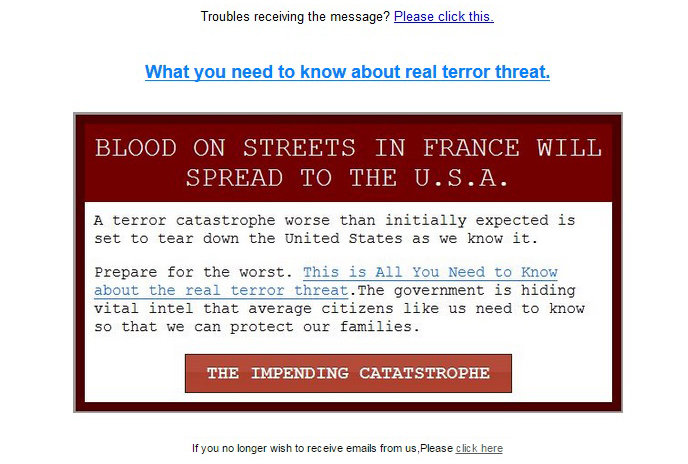
Yet another example mentions the recent terror attacks in France.
In this email, the spammers paint a bleak picture of America’s immediate future, claiming the government is hiding the truth but expects blood to flow in the streets as it did in France. But there is an answer – just click the link and you’ll find out how to protect your family from any attack.
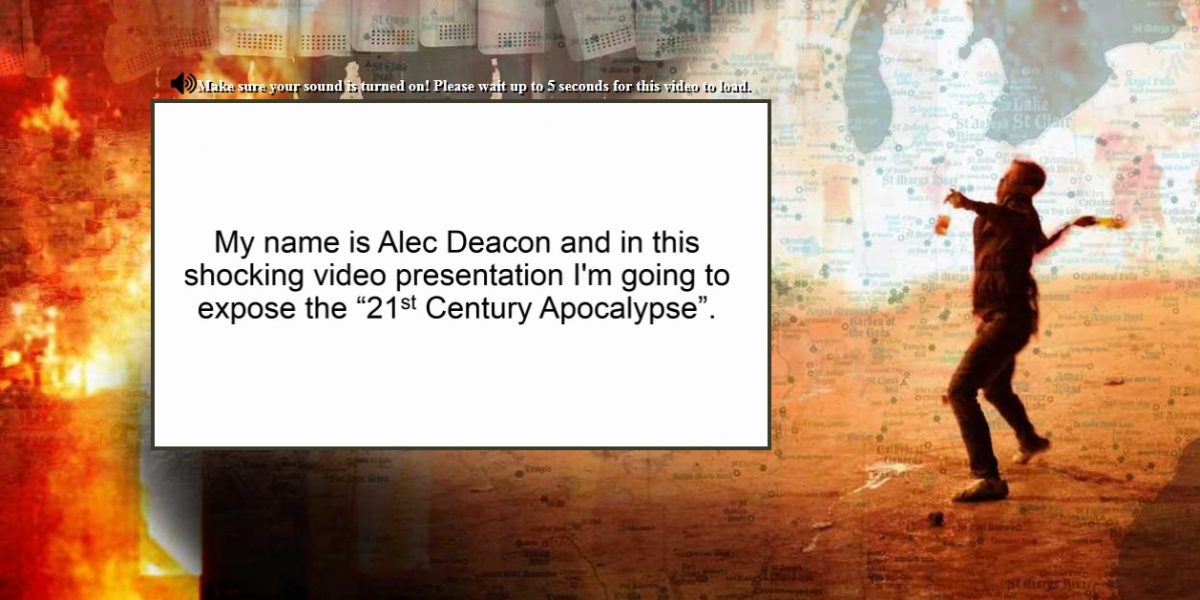
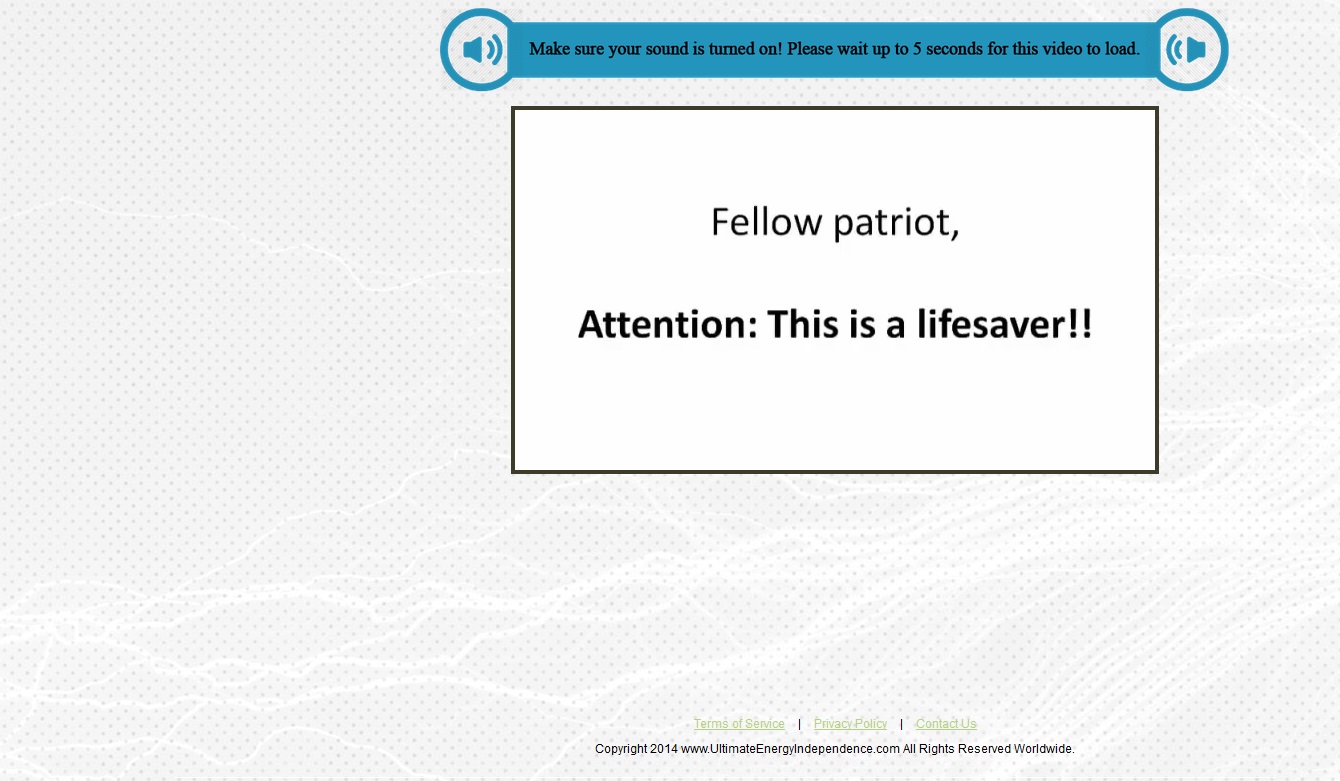
When users follow these links they are taken to sites that are also striking. They start with an audio presentation of a confidential story told by a well-wisher.
The design of the site, the voice and the details of the story differ but the essence is the same: anyone who spends a few minutes to listen to the audio will be introduced to our hero, understand why he decided to share his warnings about the disasters in store for America and, eventually, find out how to build a miracle machine that can be easily assembled in your own home. The link to the video tutorial on self-assembly of this life-saving device costs just a few dozen dollars and shows you how to create a generator so simple that even your grandmother could make it work. Happy buyers don’t only get an autonomous source of energy to be used in the event of disaster; they ca also save on household energy bills.
The audio is supported by a presentation which displays the speaker’s text. So even users who cannot turn on the sound need only have the patience to watch for a few minutes, see the offer and reward the spammers for their efforts to spread paranoia by sending them their hard-earned dollars.

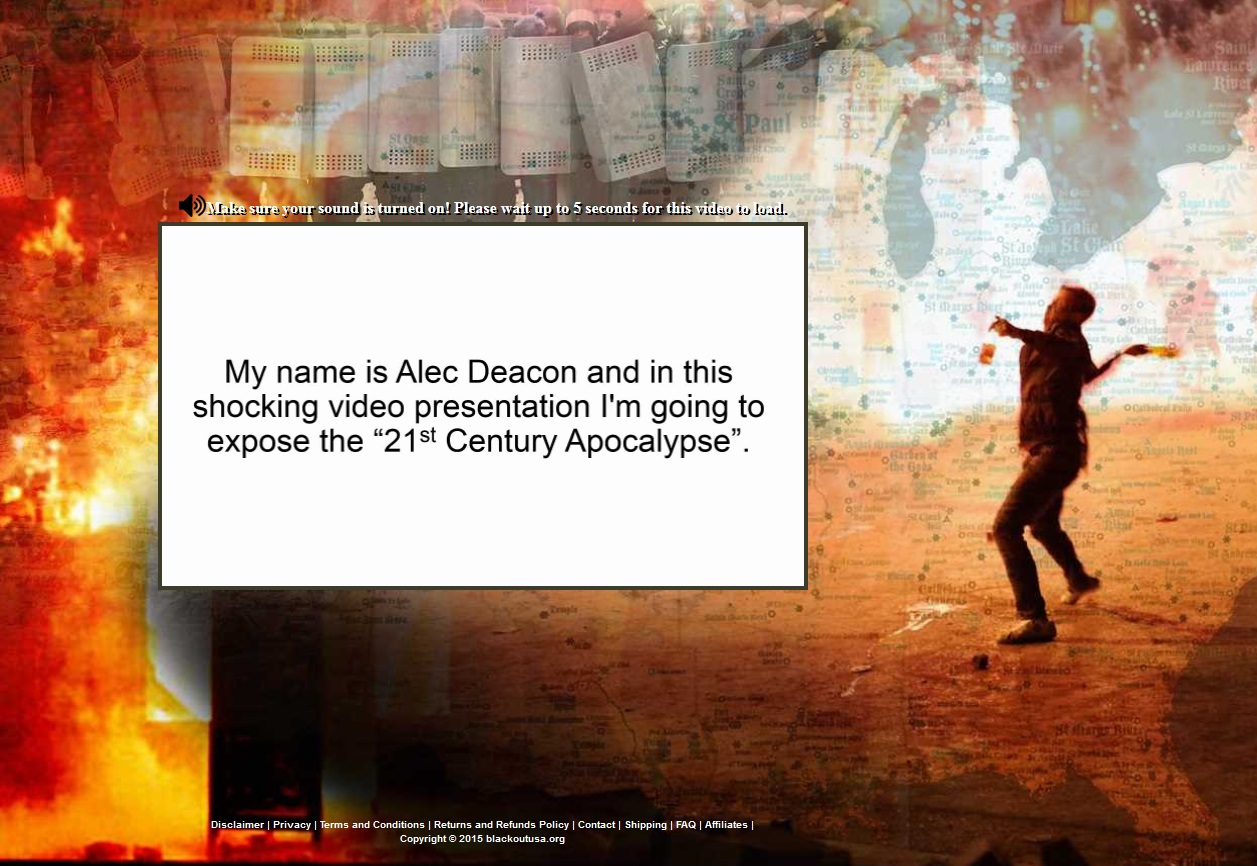
















Spammers against hurricanes and terrorist attacks