
September in figures
- The amount of spam in email traffic fell by 1.5 percentage points compared to August’s figure and averaged 81.1%.
- 59.8% of all phishing attacks targeted PayPal. Facebook re-entered the Top 5 most popular phishing targets, accounting for 3.8% of all attacks.
- Malicious files were found in 4.33% of all emails, a decrease of 1.96 percentage points compared with the previous month.
Spam in the spotlight
Viagra’s downfall
The most significant event of the month was the announcement in mid-September that the Spamlt partner program would be closed down on 1 October. Programs such as Spamlt comprise thousands of affiliates, each calling themselves a “webmaster”, working day and night to drive as much user traffic to their partners’ stores as possible. The stores sell fake watches, fake antivirus software, fake pills and even fake love, with the webmasters making thousands of dollars per day in commissions. The closure of Spamlt will undoubtedly result in some major changes to the spam category rankings: Spamlt is, or was, to be more precise, a partner program distributing pharmaceutical spam, so its demise will no doubt affect the amount of Viagra adverts that end up in users’ inboxes.
However, the beginning of September saw considerable growth in the amount of spam promoting pharmaceutical products. This may be down to the fact that those partners who already knew about the closure tried to make as much profit from pharmaceutical spam while it was still possible. The first sign of a reduction in this category of spam appeared around 20-26 September when its share decreased by a quarter – from 65% to 48%. The spammers switched to distributing malware, with the amount of messages containing malicious code increasing considerably at that time.
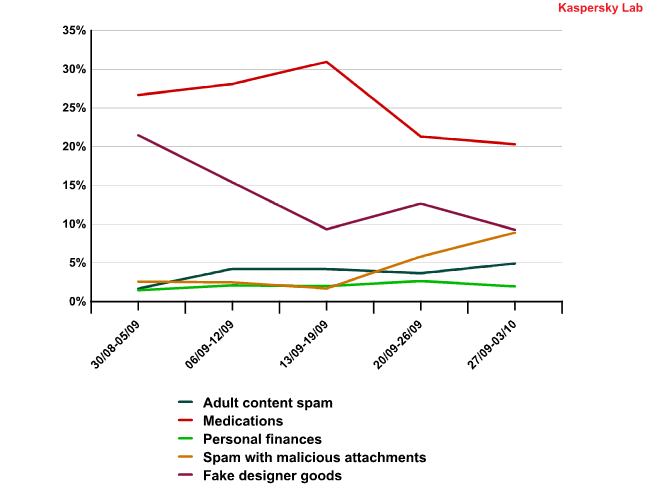
Shifts in partner spam in September 2010
In September, the share of spam related to other partner programs also increased: there were more bulk mailings advertising fake designer goods, cheap software and porn sites (the growth of the latter was particularly noticeable compared to the previous month), suggesting that spammers who used to be Spamlt partners were trying to find alternative sources of income.
Although Spamlt was a major source of medication spam, its closure does not mean that Viagra adverts will disappear from email inboxes. For a start, another partner program called Glavmed is still prospering on the Internet, and the closure of one platform does not guarantee that its creators will not open a new one in a month or two.
What links LinkedIn and ZeuS?
Users of the LinkedIn social network were the victims of one of the biggest spam attacks in September. At the end of the month messages were distributed with a link to the malicious program ZeuS which has been the focus of many an antivirus company’s attention. The attack peaked on three days – 25, 27 and 29 September – though messages were also registered on 28 and 30 September.
The messages were headed ‘LinkedIn Update’, ‘LinkedIn Messages’ and ‘LinkedIn Alert’. The text in the body of the message informed users about two unread messages that could be accessed by clicking a link. Unsurprisingly, this led to the user’s computer being infected with one of the variations of the Trojan-Spy.Win32.Zbot (ZeuS) program. The link to the ‘private messages’ either led to automatically generated second level domains in the .info zone or to hacked domains in the .com zone (in the latter case the links ended in 1.html).

Samples of fake notifications from LinkedIn containing a link to a site infected by Zbot
Almost all domains registered in the .info zone and used in this attack are now free and available for purchase.
Justice and spam
There was only one legal-related incident worthy of note in September and it involved ZeuS.
A hive of media activity was sparked by the arrests of several dozen Eastern Europeans by U.S. and British law enforcement bodies. They were accused of using ZeuS to steal about $70 million over the last eighteen months. Most of those arrested were so-called mules involved in laundering the stolen money. The criminals cashed the money using fake credit cards with credentials they acquired with the help of ZeuS, which was distributed via email.
The arrests appear to have forced the other members of the criminal gang to lie low, at least in the USA and the UK, because there was a considerable decrease in the number of Zbot (ZeuS) detections by mail antivirus programs in the territory of these countries on the day of the arrests, 30 September.

Trojan-Spy.Win32.Zbot in September. The USA and the UK
More about domain zones
In the passage above about LinkedIn and ZeuS we mentioned the automatic registration of domain names.
Since China toughened domain registration at the end of December 2009 the amount of spammer sites in the .cn domain zone has decreased dramatically. However, the spammers went off in search of other areas of the Internet to place their content. This caused a mass migration of sites advertising Viagra, fake Rolex watches and pills to improve male virility over to the Russian domain zone. The number of spam mailings on sites in the .ru domain zone started growing in January-February 2010. In September, almost every bulk mailing advertising Viagra contained a link to a site located in the Russian domain zone.

Emails containing links to the Russian domain zone
Statistical summary
Spam in mail traffic
The amount of spam detected in mail traffic decreased by 1.5 percentage points and averaged 81.1% in September 2010. A low of 76.9% was recorded on 15 September with a peak value of 87.4% being reached on 12 September.

Spam in mail traffic in September 2010
Sources of spam
In September the top 20 most popular sources of spam looked like this:
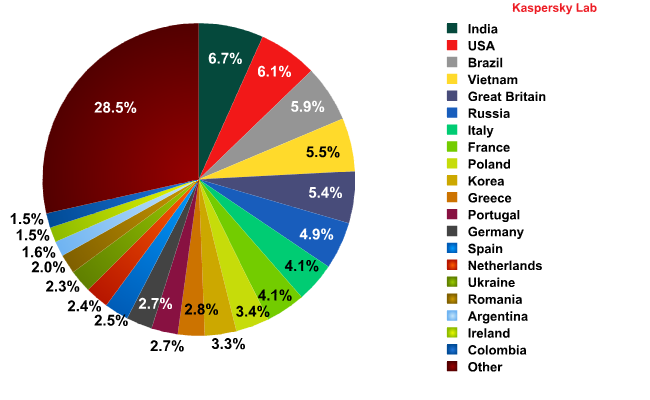
Sources of spam in September 2010
In September, the amount of spam coming from a number of countries was very similar. This meant that India was the biggest single source of spam, despite the level of spam being distributed from the country decreasing slightly. The UK was in a similar situation, coming fifth in the rating though the volume of unsolicited emails spreading from there only increased by 0.2 percentage points.
The quantity of spam distributed from Brazil rose by 3.1 percentage points.
Canada, China, Hong Kong and North Korea dropped out of the Top 20 having each distributed less than 1.5% of all spam in September.
The amount of spam originating in Europe increased in September: France’s share grew by 2.3 percentage points; Greece – 2 percentage points; Ireland – 1.3 percentage points; the Netherlands – 1 percentage point; Portugal – 1.5 percentage points; Poland – 1.3 percentage points and Germany – 0.8 percentage points. As a result Europe was the worst affected region in the world, accounting for 42% of all distributed spam.
Malware in mail traffic
Malicious attachments were most frequently found in mail traffic received in the USA (12%) followed by the UK, Japan and Spain.

Countries where mail antivirus detected malware most frequently in September 2010
Malicious files were found in 4.3% of all emails, a decrease of 2 percentage points compared with the previous month. Despite the decrease, the percentage of malicious attachments in mail traffic remains high.
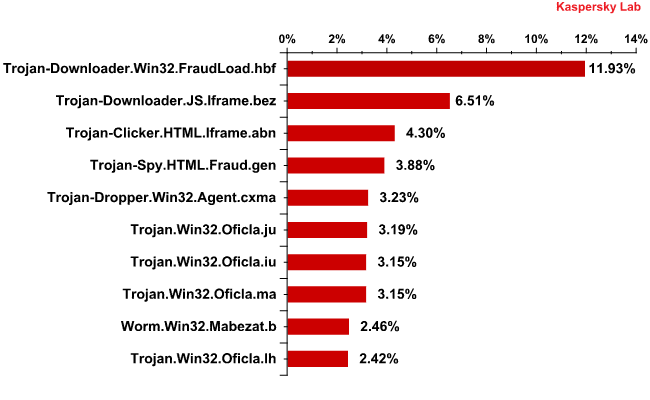
The Top 10 malicious programs distributed via email traffic in September 2010
Trojan-Downloader.Win32.FraudLoad.hbf which was especially active at the end of the month claimed first place in September’s malicious Top 10. The programs from the FraudLoad family download a rogue antivirus program that is designed to extort money from the users of victim computers. In September, the share of this Trojan-Downloader.Win32.FraudLoad.hbf averaged 12% of all the malware found in mail traffic.
The Trojan-Downloader.JS.Iframe.bez and Trojan-Clicker.HTML.Iframe.abn script Trojans came second and third in the rating. Both malicious objects are an html page written in Javascript. However, their functionality is different: Trojan-Downloader.JS.Iframe.bez downloads other malicious and advertising programs or their updates from the Internet and launches them without a user being aware of it, while Trojan-Clicker.HTML.Iframe.abn opens Internet pages in the browser increasing the traffic ranking of the site (also without informing the user about its activity). Trojan-Clicker.HTML.Iframe does not present an obvious threat to the system, but the Trojan uses up mail traffic allowing the criminals to earn money via the unauthorized exploitation of a user’s computer. In addition, the site opened by the Trojan may be infected by another more dangerous malicious program.
Fourth place is occupied by long-term Top 10 resident Trojan-Spy.HTML.Fraud.gen which uses spoofing technology and appears in the form of an HTML page. This malicious program comes with a phishing email containing a link to a fake site of a well-known bank or an e-pay system where the user is asked to enter a login and a password.
The lower half of our rating is dominated by the Oficla family. The programs from this family download other malicious programs and adware, or updates for them, from the Internet and launch them on a victim computer.
Phishing

Top 10 organizations targeted by phishing attacks in September 2010
In September, PayPal had the unenviable distinction of being targeted most by the phishers once again. The share of attacks on this e-pay system increased by 3 percentage points compared to the previous month’s figures.
Compared to August, there were no changes in the four leaders. However, the share of attacks targeting HSBC decreased while World of Warcraft gamers were attacked more often. Only 0.6 percentage points separate these two phishing targets, but there’s no saying when or if WoW will replace HSBC in third place. After dropping out of the Top 5 in August, the number of attacks targeting Facebook doubled in September, making the social network the most likely to replace HSBC in third.
Conclusion
A reduction in Viagra spam in October is the most eagerly anticipated outcome of Spamlt’s closure. However, there is little hope of seeing a similar decline in the amount of emails containing malicious attachments, because this is one of the most profitable areas for those involved in partner programs after Viagra. Due to the closure of this major source of pharmaceutical spam and the time it will to take to create a new platform, lots of cybercriminals will no doubt look to maintain their profits by switching to the decidedly more user-unfriendly distribution of malicious programs.






















Spam report: September 2010