
November in figures
- The amount of spam in email traffic was up 1.4 percentage points compared to October and averaged 80.6%.
- The amount of phishing emails doubled compared with October’s figure, accounting for 0.02% of all mail traffic.
- Malicious files were found in 3% of all emails, an increase of 0.5 percentage points from October.
Spam in the spotlight
New Year and other types of fraud
The fraudsters are trying to take advantage of the pre-holiday excitement and in anticipation of Christmas and the New Year they are distributing mass mailings enticing users to leave their financial and personal data on a phishing site. Their idea is clear enough – with all the hustle and bustle of the festive period people are less cautious and more willing to make purchases via the Internet. That is why fake notifications about blocked bank cards or accounts are of particular concern – after all, that money was going to be spent on presents.
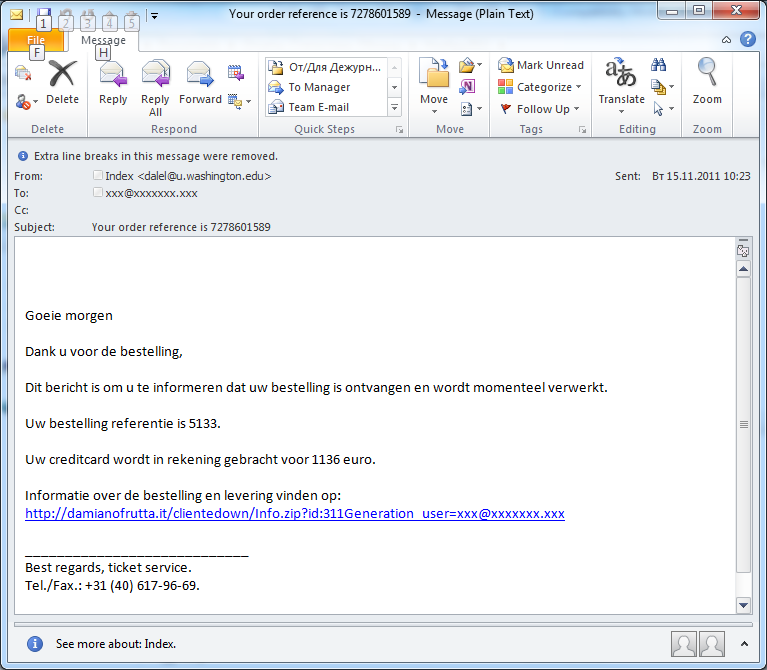
Have you ordered your presents yet?
In November, we registered several mass mailings of fake notifications from online stores. The names of specific Internet stores were not used – the recipients were merely invited to look through a bill or click a link to check an order reference. During the holiday rush many users will not pay very close attention to the attributes of such messages because they may well have ordered something at an online store and presume the messages are related to their purchases. In fact, these emails contained links to malicious code.
As can be seen from the screenshot above, these mass mailings were not only distributed in English but in other European languages. In particular, we registered emails in German, Italian and Dutch.
Fake notifications from social networking sites
Social networking sites have long been exploited by spammers advertising pharmaceuticals or spreading malware, and user accounts have been consistently targeted by phishers. Spam in November included numerous mass mailings related to social networking sites.
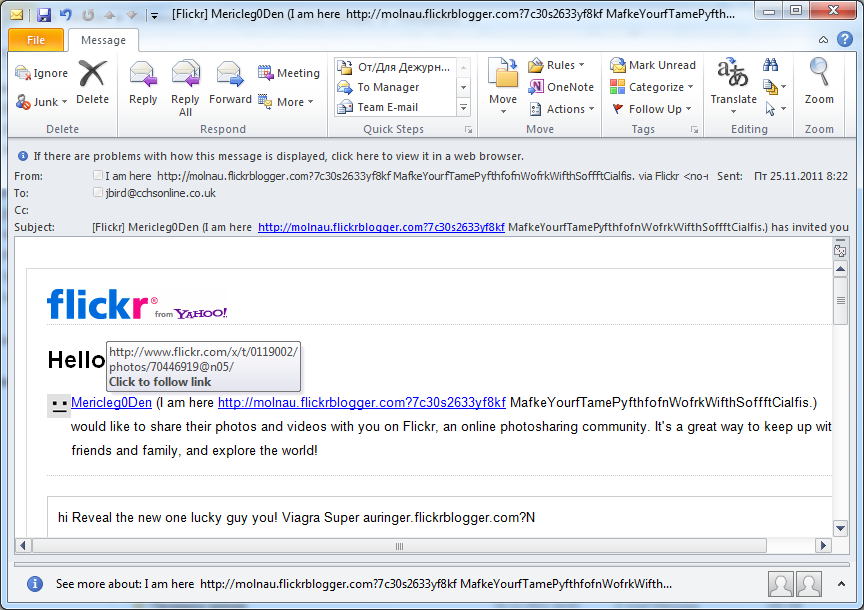
Flickr
Flickr is not often exploited by spammers. However, in November even this social networking site could not escape their attention. Interestingly, these emails were sent from Flickr accounts, using the “invite a friend” function. The spammers “invited” lots of people and tried to get them to click links which in fact led to a pharmaceutical site. This method of advertising could allow the spammers to bypass spam filters because technically the emails looked like legitimate messages – after all, they were sent using a legitimate function of the photo-sharing site.
As can be seen from the screenshot, the link in the email mentions pills to counter erectile dysfunction.
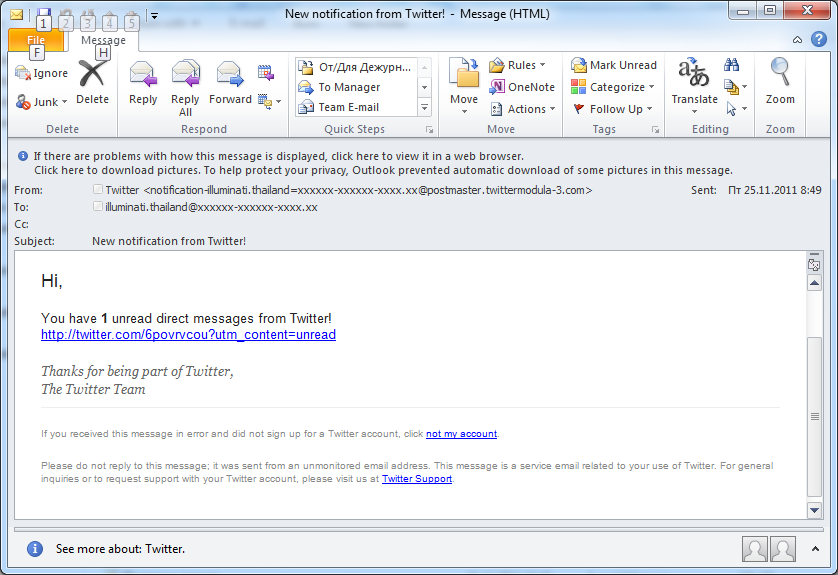
Twitter fell victim to a similar spammer trick – invitations to join the social networking site were allegedly sent on behalf of Twitter users. The invitations contained a rather steamy text and a link that redirected the user to a porn site. Tellingly, the link in the email uses a URL shortening service in the cn domain zone.
Fake notifications from Twitter were also registered this month though in fewer quantities than in the summer of 2010 when the Internet endured a real explosion of such notifications. However, they are still popular with spammers: on clicking the link the user is redirected to a site containing both a Viagra ad and malicious code.
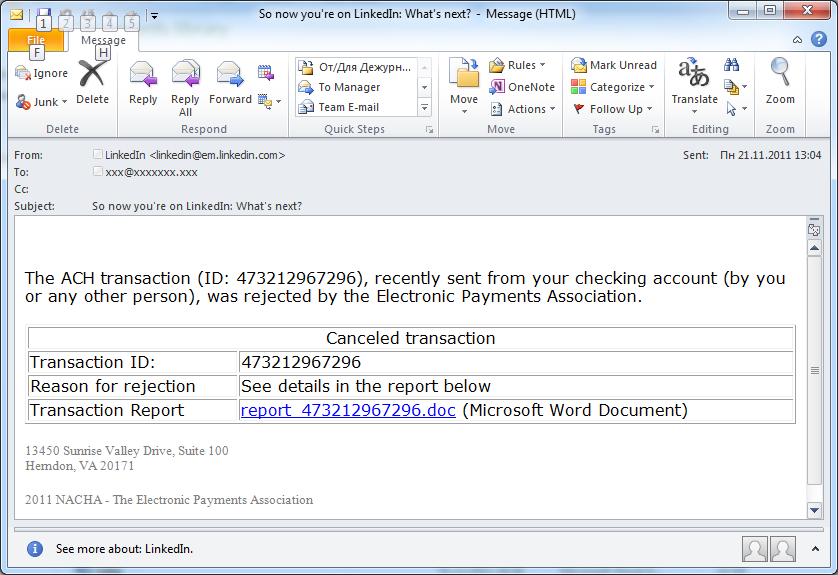
In November, there was an unusual incident involving LinkedIn. In addition to the traditional fake notifications containing links to pharmaceutical sites, this month saw a rather strange mass mailing.
The header of the message read: “So now you’re on LinkedIn: What’s next?” The “From” field imitated an official notification from LinkedIn. And then the bad news: when the user opened the email he was surprised to learn that a recent transaction made via an e-pay system from his account had been canceled!
Fake notifications from the Nacha e-pay system appear regularly in users’ inboxes. They usually have more appropriate headers and the “From” field usually contains the name of the e-pay system. What caused the mistake this time is not clear.
Notably, November’s spam included several mass mailings which contained fake notifications from LinkedIn.
The holiday season goes on
In November, spammers continued to send emails dedicated to different holidays. In the US, and a few other countries, Thanksgiving was a popular theme; in the Islamic world the focus was on Eid al-Adha.
The emails exploiting the theme of Eid al-Adha were mostly in Turkish and advertised religious tourism. ‘Thanksgiving’ emails advertised holiday presents.
The spammers did not neglect the coming Christmas and the New Year holidays either.
The amount of mass mailings containing offers of travel and tourism doubled in November (+3.5 percentage points), which is most probably down to the upcoming holidays.
Statistical summary
Sources of spam
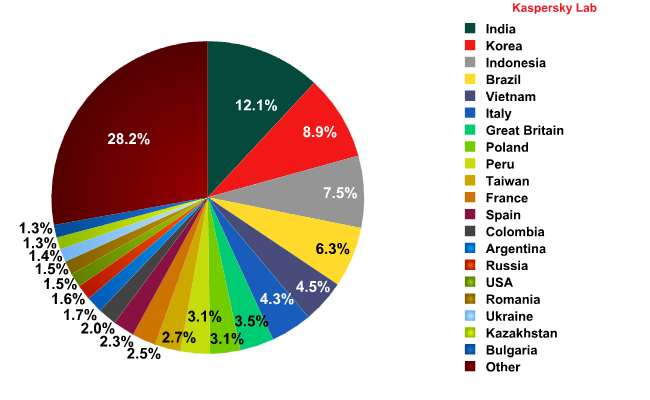
Top sources of spam in November 2011
In November, the top four leading spam sources remained largely unchanged, although Brazil and Indonesia swapped places. The general level of spam emanating from the Top 5 countries increased by 7.2 percentage points, with the contribution of each country grewing: India (+1.86 percentage points), South Korea (+2.31 percentage points), Indonesia (+2.29 percentage points), and Brazil (+0.12 percentage points).
Italy distributed less spam in November (-0.76 percentage points compared to October’s figure) and dropped to 6th place.
Malware in mail traffic
In November, the share of malicious files found in all emails amounted to 3% — an increase of 0.5 percentage points compared to October.
The top two countries with the highest levels of email antivirus detection remained unchanged: Russia stayed out in front, 6 percentage points ahead of the US. Both countries showed an increase – of 3.39 and 2.77 percentage points respectively – compared with October.
In November, the share of antivirus detections in the UK nearly halved, accounting for 4.8%. A similar drop was recorded in Australia (3.1%) which placed these countries 4th and 10th in the rating.
The changes in the share of antivirus detections on the territory of the other Top 10 members were insignificant, fluctuating within the range of 1 percentage point.
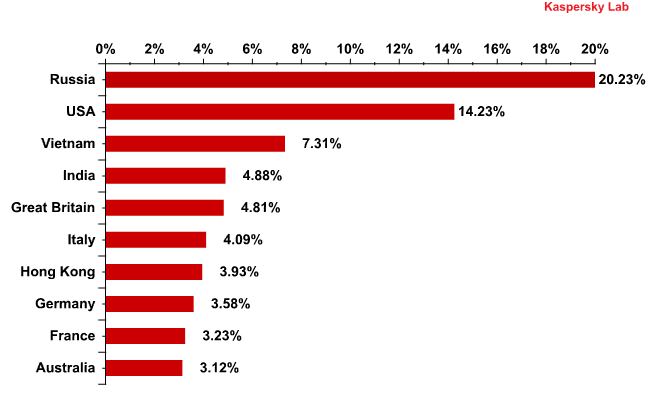
Distribution of email antivirus detections, by country: November 2011
November’s list of the most frequently detected malicious programs did not see many changes either.
Trojan-Spy.HTML.Fraud.gen topped the rating for the umpteenth time, appearing in 12% of all malware spread via email – only 1 percentage point less than in the previous month. This Trojan uses spoofing technology and appears in the form of an HTML page. It comes with a phishing email containing a link to a fake site resembling that of a well-known bank or e-pay system where the user is asked to enter a login and a password.
Second came Email-Worm.Win32.Mydoom.m, a mail worm whose only functions are to harvest email addresses and to send copies of themselves to these addresses. Another long-term resident of this Top 10 with the same set of functions is Email-Worm.Win32.NetSky.q in 10th place. 8th place was occupied by Bagle.gt. It is yet another mail worm, but as well as the usual functionality it downloads malicious programs from the Internet.
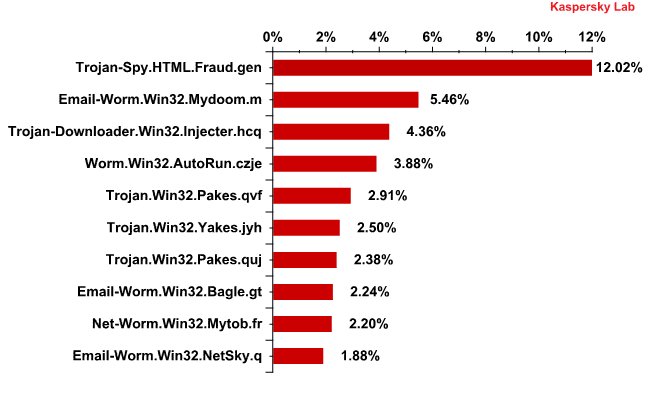
Top 10 malicious programs spread via email in November 2011
November’s Top 10 malicious programs that spread via email included only one Trojan.Win32.Yakes modification – Trojan.Win32.Yakes.jyh. To recap, Yakes is a classic Downloader Trojan that downloads other malicious programs once installed on a computer.
The Trojans occupying 5th and 7th positions belong to the Trojan.Win32.Pakes family used to help other malicious programs evade antivirus detection.
Phishing
The percentage of phishing emails in all mail traffic doubled compared with October’s figure and averaged 0.02%.
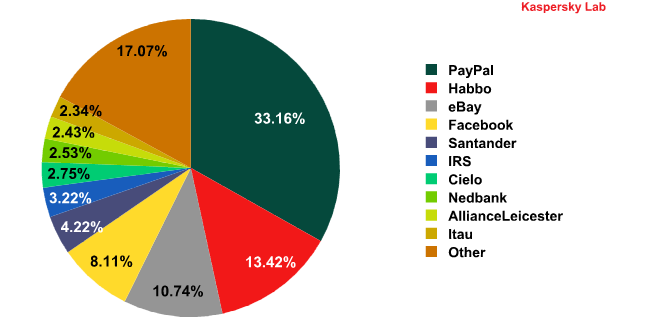
Top 10 organizations targeted by phishers*
* This rating is based on the number of phishing URLs on the Internet that attempt to obtain user logins and passwords for various online services. The rating is not demonstrative of the security level of the organizations named above, but rather the popularity of their services among users, which in turn explains their popularity among phishers.
The Top 10 rating of organizations most often targeted by phishers has seen major shifts compared with the previous month.
The rise of Habbo to second place was a major surprise – in October it had dropped out of the Top 10 altogether. The share of attacks on this social networking site increased tenfold. The number of attacks targeting Facebook grew slightly placing it in 4th position.
There were no online games among the Top 10 phishing targets.
At the same time banking organizations remained firmly in the sights of phishers – half of the Top 10 entries were banks.
Interestingly, the end of the year has been marked by an intensification of phishing attacks targeting the IRS, which may be linked to the filing of annual tax returns in the US.
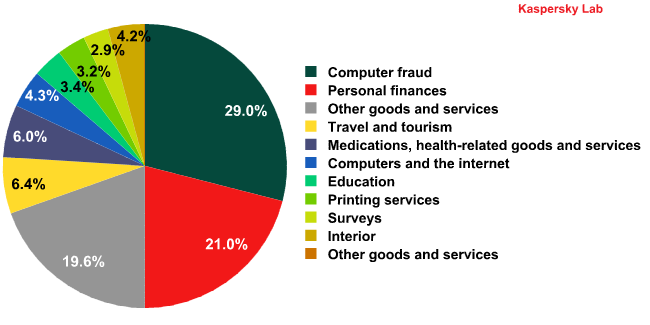
Spam by category
There was no change among the top three categories of English-language spam. Fraudulent emails remained on top. The share of financial spam – second in the rating – increased by 4 percentage points.
These categories may owe their popularity to the on-going financial crisis and the upcoming holidays. During this period money worries are especially acute and spammers take advantage of the situation, offering quick loans and dubious get-rich-quick schemes.
The Other goods and services category occupies 3rd place in the rating. The lion’s share of this category’s messages is dedicated to Christmas. Overall, the amount of emails exploiting the Christmas or New Year theme accounted for 3-3.5% of all spam traffic.
Conclusion
In November, the distribution of spam mailings and the distribution of email antivirus detections saw no major changes.
Currently, the phishers’ attention is distributed fairly evenly between real and virtual money, which they are trying to extort from users. The return of Habbo to the Top 10 phishing targets means the virtual environment is becoming attractive for them once again.
In December, spam flows will obviously be affected by the festive rush: we will see further growth in the number of emails offering holiday tours and corporate celebrations. The Other goods and services category will include various offers for presents. We also expect an increase in the amount of fraudulent emails. By the end of December and during the long New Year break in Russia, we will no doubt see the traditional downturn in spam activity. Spam mailings over this period will include partner emails with malicious attachments and Viagra ads.






















Spam report: November 2011